Vendor Access Overview
What is Vendor Access?
Vendor Access is a feature of Admin By Request's Secure Remote Access product that allows external users, such as third-party vendors, to be given secure access to internal devices. This access is managed entirely through their local Internet browser app - there is no need for any additional locally installed software.
Related information
Prerequisites
The main prerequisite for Vendor Access applies to Single Sign-On, where SSO must be enabled for each user who will login to the Vendor Access page (https://access.work).
Additional requirements depend on your environment and whether or not you are using Cloudflare's managed service as a gateway, or hosting your own on-premise gateway.
Prerequisites are listed under these headings - review those relevant to your environment:
 Data location
Data location
Your data is stored in a data center that is located in one of the geographic locations listed below. These are in Europe, the USA, the UK and Asia.
To determine your data location, go to page Tenant Settings > Data in the portal and click the RETENTION tab.
Note the geographic location shown in field Data Location - it will be one of the following:
-
EU West, Netherlands (Europe)
-
US East, Virginia (USA)
-
US West, California (USA)
-
London, United Kingdom (UK)
-
EU Central, Germany (Europe)
-
Singapore (Asia)
To determine the API prefix for your data center, go to page Tenant Settings > API Keys in the portal and check which API prefix is shown under About API Keys. The data center API URL (also known as the API prefix) will be one of the following:
-
https://dc1api.adminbyrequest.com (Europe - Netherlands)
-
https://dc2api.adminbyrequest.com (US East)
-
https://dc3api.adminbyrequest.com (UK)
-
https://dc4api.adminbyrequest.com (Europe - Germany)
-
https://dc5api.adminbyrequest.com (US West)
-
https://dc6api.adminbyrequest.com (Asia)
Make a note of your prefix - among other things, this is the domain used when an API Key is created.
You can also see your API prefix on the API web pages (e.g. Public API > Auditlog API). However, a small script runs in the background that determines to which data center you are attached, so JavaScript must be enabled in your browser for this to work.
 IP addresses and API URLs
IP addresses and API URLs
Admin By Request uses port 443 and the IP addresses and API URLs that need access through firewalls are as follows.
If your data is located in Europe (Netherlands):
-
IP: 104.45.17.196
-
DNS: api1.adminbyrequest.com
-
DNS: macapi1.adminbyrequest.com
-
DNS: linuxapi1.adminbyrequest.com
If your data is located in the USA (East):
-
IP: 137.117.73.20
-
DNS: api2.adminbyrequest.com
-
DNS: macapi2.adminbyrequest.com
-
DNS: linuxapi2.adminbyrequest.com
If your data is located in the UK:
-
IP: 85.210.211.164
-
DNS: api3.adminbyrequest.com
-
DNS: macapi3.adminbyrequest.com
-
DNS: linuxapi3.adminbyrequest.com
If your data is located in Europe (Germany):
-
IP: 9.141.94.162
-
DNS: api4.adminbyrequest.com
-
DNS: macapi4.adminbyrequest.com
-
DNS: linuxapi4.adminbyrequest.com
If your data is located in the USA (West):
-
IP: 172.184.188.29
-
DNS: api5.adminbyrequest.com
-
DNS: macapi5.adminbyrequest.com
-
DNS: linuxapi5.adminbyrequest.com
If your data is located in Asia (Singapore):
-
IP: 52.230.54.129
-
DNS: api6.adminbyrequest.com
-
DNS: macapi6.adminbyrequest.com
-
DNS: linuxapi6.adminbyrequest.com
Wherever you are, you can also use api.adminbyrequest.com, but the regional URLs will likely be more responsive.
 Cloud gateway (managed service)
Cloud gateway (managed service)
-
If you are using Secure Remote Access, you need to allow your browsers access to the following cloud gateways:
-
cloudgatewayeu1.accessbyrequest.com (Europe - Netherlands)
-
cloudgatewayus1.accessbyrequest.com (US East)
-
cloudgatewayuk1.accessbyrequest.com (UK)
-
cloudgatewaygermany1.accessbyrequest.com (Europe - Germany)
-
cloudgatewayuswest1.accessbyrequest.com (US West)
-
cloudgatewaysingapore1.accessbyrequest.com (Asia)
They are called over WSS (Websockets Secure) on port 443 from the browser.
Further, if you wish to remotely access endpoints using Unattended Access and Remote Support:
-
Outbound MQTT broker connectivity via Websockets - port 443 - for the following:
-
If your data is located in Europe (Netherlands):
Ten nodes (FastTrackHubEU1.azure-devices.net to FastTrackHubEU10.azure-devices.net) -
If your data is located in the USA (East):
Ten nodes (FastTrackHubUS1.azure-devices.net to FastTrackHubUS10.azure-devices.net) -
If your data is located in the UK:
Ten nodes (FastTrackHubUK1.azure-devices.net to FastTrackHubUK10.azure-devices.net) -
If your data is located in Europe (Germany):
Ten nodes (FastTrackHubGermany1.azure-devices.net to FastTrackHubGermany10.azure-devices.net) -
If your data is located in the USA (West):
Ten nodes (FastTrackHubUSWest1.azure-devices.net to FastTrackHubUSWest10.azure-devices.net) -
If your data is located in Asia:
Ten nodes (FastTrackHubSingapore1.azure-devices.net to FastTrackHubSingapore10.azure-devices.net)
-
-
For Unattended Access, RDP needs to be enabled on port 3389 on the device
-
-
Cloudflare connectivity:
-
UDP outbound - port 7844 for the following:
-
region1.v2.argotunnel.com
-
region2.v2.argotunnel.com
-
If your firewall supports Server Name Indication (SNI), you need to allow the following URLs (UDP outbound - port 7844):
-
cftunnel.com
-
h2.cftunnel.com
-
quic.cftunnel.com
-
Refer to https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/deploy-tunnels/tunnel-with-firewall/ for more information on Cloudflare's "tunnel with firewall" configuration.
-
-
The endpoint needs to be enrolled with an Admin By Request Secure Remote Access license (see Product Enrollment).
-
For Windows endpoints, RDP needs to be enabled on port 3389 on each device.
 On-premise gateway (self-hosted)
On-premise gateway (self-hosted)
-
Access to pull Docker images from adminbyrequest.azurecr.io
-
Admin By Request API - port 443 - for the following:
-
connectorapi1.adminbyrequest.com (if your data is located in Europe - Netherlands)
-
connectorapi2.adminbyrequest.com (if your data is located in the USA)
-
connectorapi3.adminbyrequest.com (if your data is located in the UK)
-
connectorapi4.adminbyrequest.com (if your data is located in Europe - Germany)
-
connectorapi6.adminbyrequest.com (if your data is located in Asia)
-
-
Outbound MQTT broker connectivity via Websockets - port 443 - for the following:
-
If your data is located in Europe (Netherlands):
Ten nodes (FastTrackHubEU1.azure-devices.net to FastTrackHubEU10.azure-devices.net) -
If your data is located in the USA (East):
Ten nodes (FastTrackHubUS1.azure-devices.net to FastTrackHubUS10.azure-devices.net) -
If your data is located in the UK:
Ten nodes (FastTrackHubUK1.azure-devices.net to FastTrackHubUK10.azure-devices.net) -
If your data is located in Europe (Germany):
Ten nodes (FastTrackHubGermany1.azure-devices.net to FastTrackHubGermany10.azure-devices.net) -
If your data is located in the USA (West):
Ten nodes (FastTrackHubUSWest1.azure-devices.net to FastTrackHubUSWest10.azure-devices.net) -
If your data is located in Asia:
Ten nodes (FastTrackHubSingapore1.azure-devices.net to FastTrackHubSingapore10.azure-devices.net)
-
-
Cloudflare connectivity:
-
UDP outbound - port 7844 for the following:
-
region1.v2.argotunnel.com
-
region2.v2.argotunnel.com
-
If your firewall supports Server Name Indication (SNI), you need to allow the following URLs (UDP outbound - port 7844):
-
cftunnel.com
-
h2.cftunnel.com
-
quic.cftunnel.com
-
Refer to https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/deploy-tunnels/tunnel-with-firewall/ for more information on Cloudflare's "tunnel with firewall" configuration.
-
-
In order for the on-premise gateway to be able to discover devices on the network, these need to be available to the gateway on ports 3389 (RDP), 22 (SSH) or 5900/5901 (VNC).
How does Vendor Access work?
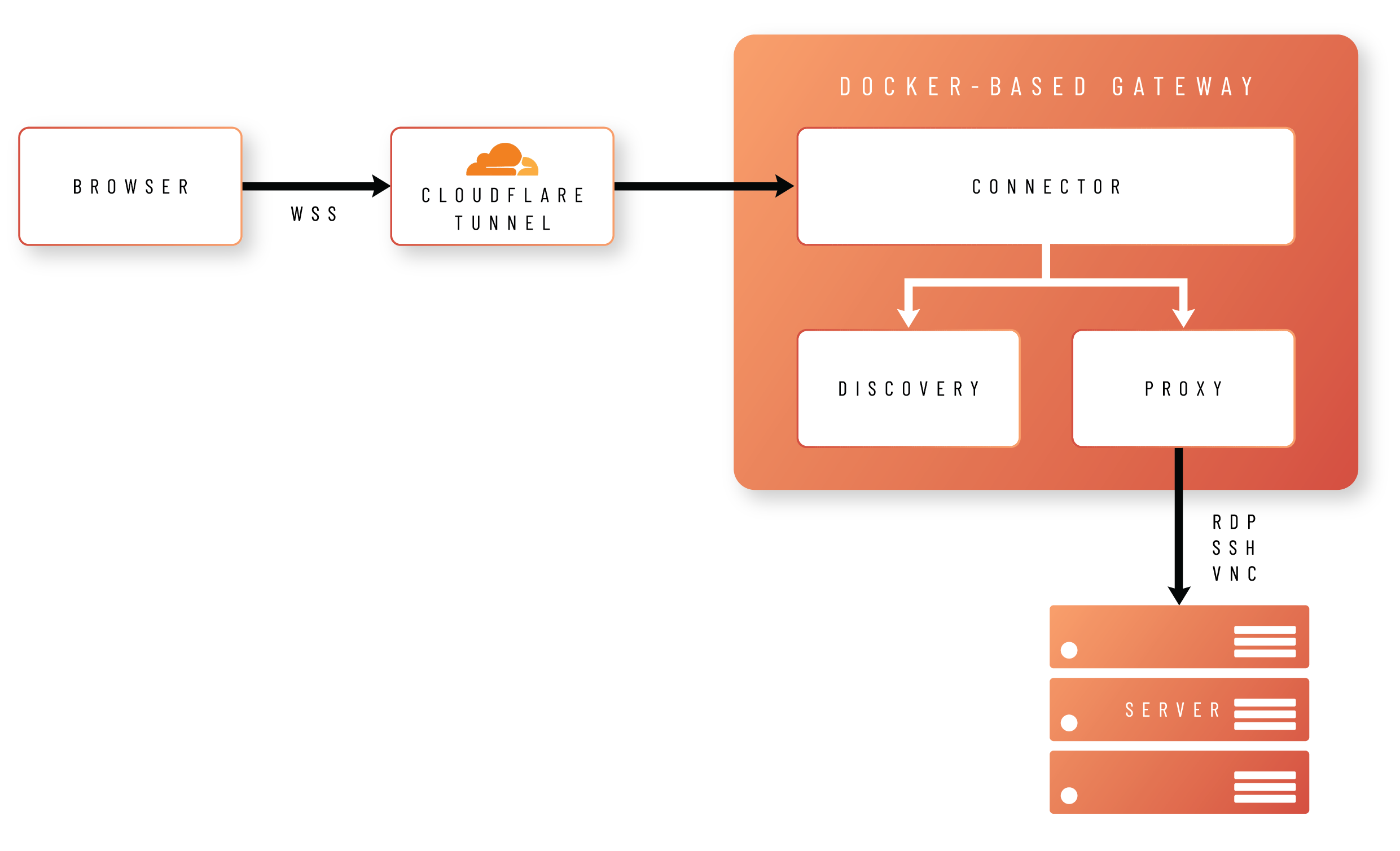
Architecture
The idea behind Vendor Access is to allow users to connect to your remote endpoints using nothing but their browsers.
In order to achieve this, the browser creates a Secure WebSocket connection to a Docker-based gateway, hosted either in your own infrastructure (self-hosted) or as a managed service.
The gateway comprises three different images:
-
Connector
Handles validation and translation of the data between the portal and the proxy container, as well as managing logs, health checks and other data. -
Proxy
Establishes a protocol connection between Admin By Request and your endpoint using either RDP, SSH or VNC. -
Discovery
Handles automatic discovery of connectable devices running on the same network as the gateway.
Process
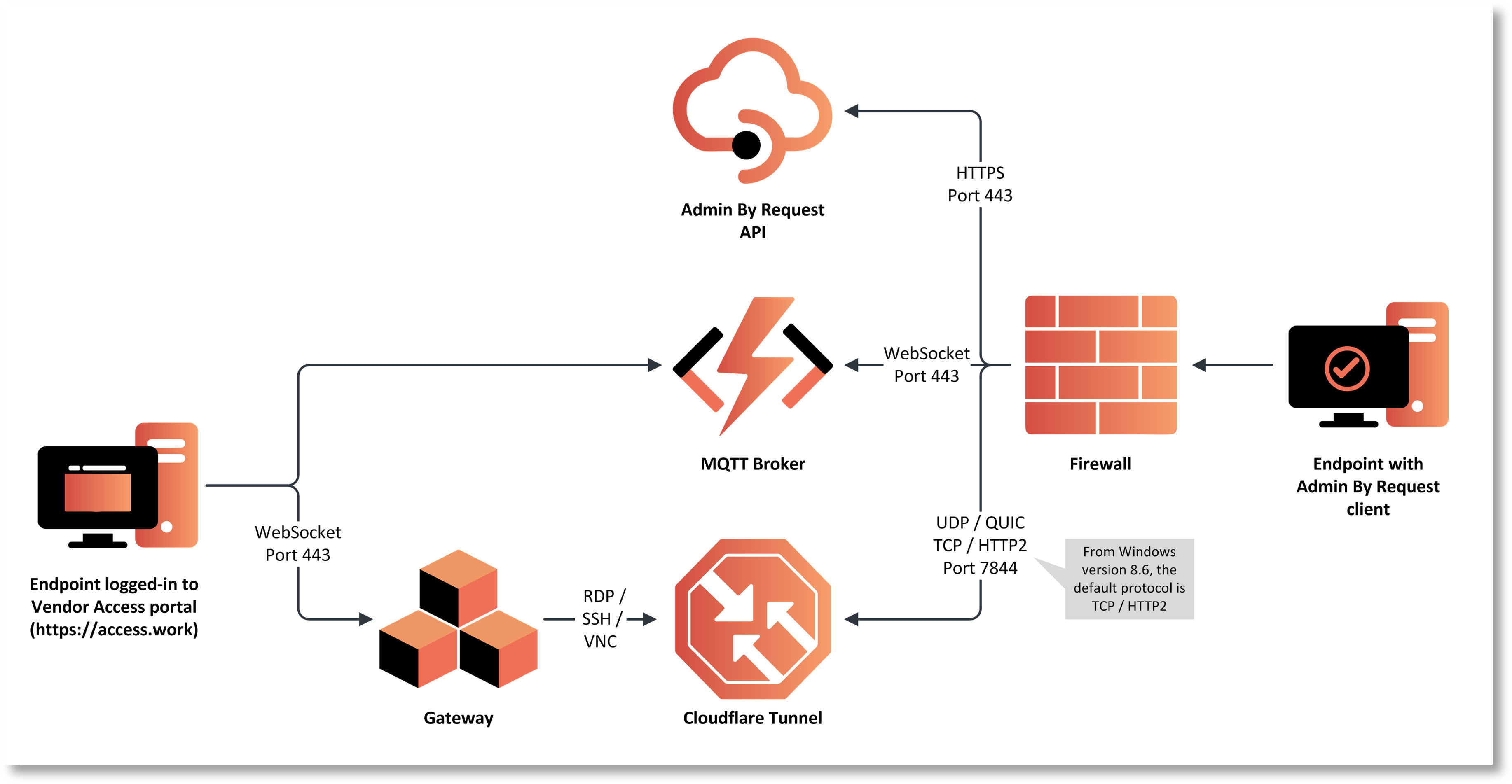
The process by which a user establishes a Vendor Access session is:
-
The user initiates a connection from https://access.work.
-
The Admin By Request client on the target endpoint receives an instruction from the MQTT Broker to fetch settings using the Admin By Request API.
-
The settings response instructs the Admin By Request client to open a Cloudflare Tunnel by making an outbound UDP call on port 7844 using the QUIC Protocol.
-
The Gateway is instructed to forward the RDP, SSH or VNC connection through the tunnel opened by the endpoint.
-
A secure WebSocket connection is established between the user's browser and the Gateway. The response stream from the RDP, SSH or VNC connection is routed back to the browser using this secure connection.
The process is illustrated in the following diagram:
What next?
This