Updating Client Software for Large Enterprises
Overview
Keeping the Admin By Request (ABR) client software up-to-date is essential for security, stability, and access to the latest features. This technical note provides best-practice guidance for enterprise administrators on how to manage ABR client software updates at scale, with a focus on avoiding redundancy, ensuring compliance, and minimizing administrative overhead.
This article is available in PDF format:
Recommended Update Strategy
Preferred Approach: Use Enterprise Software Deployment Tools
For enterprise-scale environments, we recommend using your internal software deployment tools to manage ABR client updates, rather than using the Admin By Request Auto Update feature.
Auto Update can (and should) be used in special cases - these are discussed later in this article.
Supported tools include:
-
Microsoft Endpoint Configuration Manager (MECM/SCCM)
-
Microsoft Intune
-
JAMF (macOS)
ABR client updates are also known to work with other MDM products, such as Ivanti / LANDesk. However, at the time of writing, only the three mentioned above are routinely tested.
We recommend deploying client updates using your MDM tool rather than Auto Update because that allows greater control over version targeting, deployment schedules, rollback capabilities, and compliance reporting.
Best Practices
-
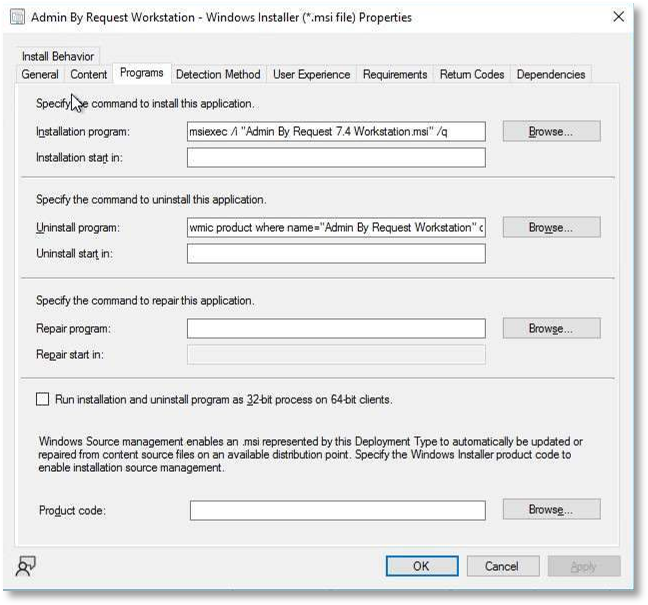
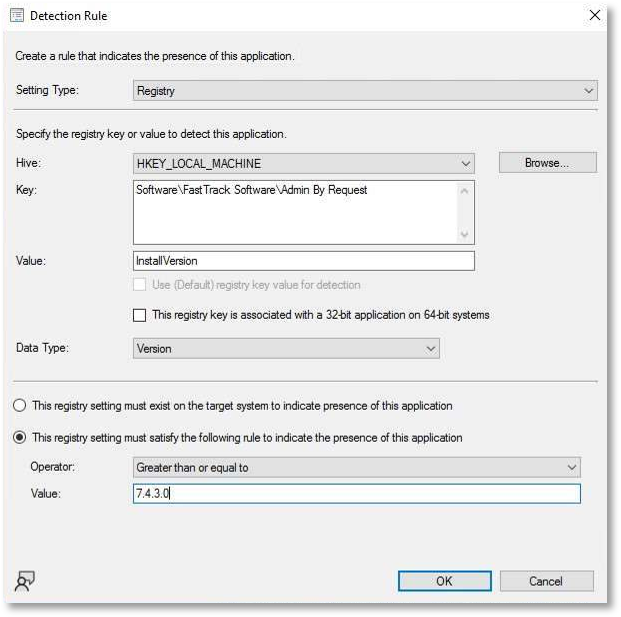
Enable version-aware deployment: Only deploy ABR updates if the installed version is older than the package being pushed.
For example (SCCM deployment condition):
-
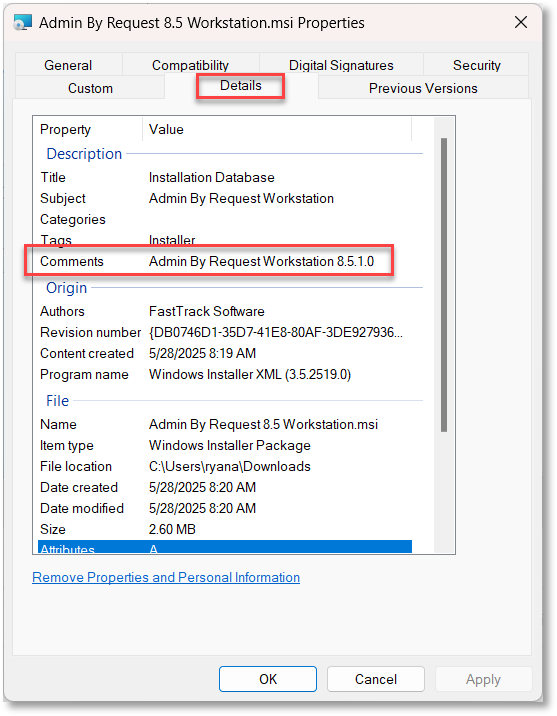
Source the exact ABR version from file properties of the downloaded installer. The download portal only displays major.minor (e.g., 8.5), whereas the full version (e.g., 8.5.1.0) is embedded in the file's metadata (Right-click > Properties):
-
Test update packages in a pilot group before broad rollout.
Auto Update Feature
The Auto Update feature allows clients to fetch updates directly from the ABR cloud. While this may seem convenient, sometimes it's not ideal for enterprises due to the following concerns:
-
Loss of control over version timing
-
Increased external internet dependency
-
Risk of unexpected behavior during broad deployment
Auto Update is configured via the Admin By Request portal at Settings > Tenant Settings > Auto-Update > WINDOWS WORKSTATION.
As well as Windows Workstation, separate settings are available for Windows Server, Mac and Linux endpoint clients.
Recommended Use Case
Enable Auto Update temporarily (i.e. for a defined period only) if:
-
Devices are off-network (e.g., field staff or remote workers)
-
You lack coverage through traditional deployment tools
-
You need to perform an emergency update (e.g., for a security patch)
Recommended Settings
Set Auto Update to ON for 2–4 weeks to catch unreachable endpoints. Afterwards, disable Auto Update to resume managed deployment.