Portal Administration for Unattended Access
Introduction
This topic documents configuration parameters in the Admin Portal that can be used to manage Unattended Access Settings and Sub Settings.
Fields that can be set/configured in the portal are presented in tables, with each table showing:
-
Setting - the name of the field that controls the setting
-
Type - the type of value that can be entered or selected and its default value
-
Description - how the setting is used and notes about any implications it may have on other settings
To change any of the settings in the portal, log in to the portal and select the setting from the menu.
In this topic
Unattended Access Settings
Portal menu: Secure Remote Access > Settings > Unattended Access Settings
Settings here are the global settings for all endpoints participating in the feature. You can overrule settings for listed domain users or computers under the sub-settings menu.
 Authorization
Authorization
Portal menu: Secure Remote Access > Settings > Unattended Access Settings > Authorization
AUTHORIZATION tab
Unattended Access is a feature that allows portal admins to remote control computers using only a browser and without requiring a user to be present at the remote computer.
Allow Unattended Access is the overall setting that determines whether or not the feature is enabled.
|
Setting |
Type |
Description |
|---|---|---|
|
Allow Unattended Access |
Toggle Default: On |
On - Allows computers to be accessed remotely without a user present. Reveals Require approval and Require reason fields. Off - Computers cannot be accessed remotely without a user present. Hides Require approval and Require reason fields. Note that Remote Support might still be possible, depending on Remote Support settings. |
|
Require approval (hidden if Allow Unattended Access is Off) |
Toggle Default: Off |
On - Sends a request to the IT team, which must be approved before remote access to the server or device is granted. Makes Require reason mandatory (i.e. must be On). Off - Allows remote access to the server or device without approval. Makes Require reason optional (i.e. can be either On or Off). |
|
Require reason (hidden if Allow Unattended Access is Off) |
Toggle Default: Off |
On - A reason for remote access must be provided, and it must comprise at least two words. This information is stored in the Auditlog. Off - No reason is required for remote access, but details of the actions performed are stored in the Auditlog. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
NOTIFICATION tab
Email notification to administrators is available when Require approval is checked under Authorization.
Notifications can be sent for the following scenarios:
-
Each new request for approval (Run As Admin) or admin session access (Admin Session)
-
When malware is detected (Workstation Settings > [OS] Settings > Malware)
-
When unattended remote access is requested (Unattended Access)
-
When either an end user or portal admin initiates a Remote Support session.
As with other request types, new requests for approval always appear under Requests > Pending in the Portal top menu. This is the case for both Endpoint Privilege Management and Secure Remote Access.
The Notification setting enables and configures additional email notification for new requests. If multiple email addresses are specified, they must be on separate lines.
Phone notification is separate and happens automatically via push notifications to phones with the mobile app installed.
|
Setting |
Type |
Description |
|---|---|---|
|
Send email notifications |
Toggle Default: Off |
On - Additional email notifications are sent to the email addresses listed in Email addresses. Off - Email notifications are not sent. |
|
Email addresses |
Text |
Standard email address format. Use a new line for each address. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Settings
Settings
Portal menu: Secure Remote Access > Settings > Unattended Access Settings > Settings
RESOURCES tab
Enable or disable file sharing.
At the time of writing, this is available only for RDP and SSH devices. File sharing does not work for Mac currently, as Secure Remote Access for Mac is based on VNC.
|
Setting |
Type |
Description |
|---|---|---|
|
Allow file sharing |
Toggle Default: On |
On - Allows the upload of files to the server in the cloud. Off - Disables the ability to upload files to the server. If file upload is a concern, this setting should be disabled (i.e. set to Off). |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
RECORDING tab
Screen recording means that the remote session is recorded.
Files are stored locally and can be requested in the auditlog by expanding the relevant line.
|
Setting |
Type |
Description |
|---|---|---|
|
Screen recording |
Toggle Default: Off |
On - Screen recording is enabled. Off - Screen recording is disabled. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Security
Security
Portal menu: Secure Remote Access > Settings > Unattended Access Settings > Security
PASSWORDLESS tab
Used to connect to endpoints passwordless. This setting creates a local shadow account for the portal user. The password is 256 characters long and is automatically rotated and exchanged with the target server with no visibility to the portal user. The local account is enabled only when the portal user is connected.
This setting has no effect in an agentless set up, where the client software is not installed on the server.
At the time of writing, passwordless access is available for Windows endpoints only.
|
Setting |
Type |
Description |
|---|---|---|
|
Passwordless access |
Toggle Default: Off |
On - Passwordless access is enabled - a local admin account that is an alias of the logged-in portal user will be created every hour. Reveals Account is admin field. Off - Passwordless access is disabled. Hides Account is admin field. |
|
Account is admin (hidden if Passwordless access is Off) |
Toggle Default: Off |
On - The rotating account will have admin-level access.. Off - The rotating account will not have admin-level access. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
MFA tab
MFA (Multi-Factor Authentication) requires the portal user to re-authenticate with single sign-on when connecting remotely to an endpoint.
If the logged-on portal user does not log on with SSO (single sign-on), the user will be denied access to the endpoint.
|
Setting |
Type |
Description |
|---|---|---|
|
Require MFA |
Toggle Default: On |
On - The logged-on portal user must authenticate via SSO when connecting remotely to an endpoint. Off - Portal user does not need to authenticate via SSO to remotely connect. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
SESSION EXPIRY tab
Session expiry is the maximum length a remote session may last. When this time expires, the remote session will be disconnected.
Selecting Unlimited is not recommended, as this would result in no expiry on the remote session.
|
Setting |
Type |
Description |
|---|---|---|
|
Session expiry |
Selection Default: 4 hours |
Select a value between 15 minutes and Unlimited. Custom is also available - if selected, choose the required number of Hours and Minutes. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Gateways
Gateways
Portal menu: Secure Remote Access > Settings > Unattended Access Settings > Gateways
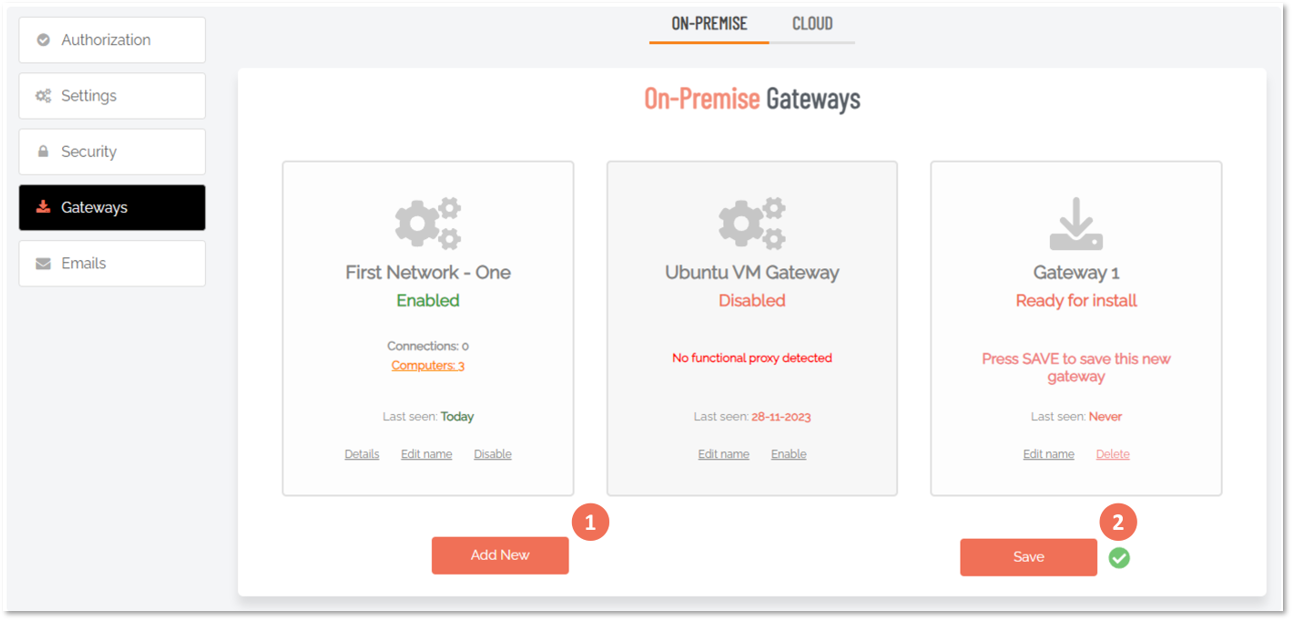
The Gateways menu provides both dashboard and detailed information views. The default view is the Gateway Dashboard, which provides an overview of existing gateways and links and buttons for further information.
Additional views are: New Gateway and Existing Gateway.
CLOUD tab
Cloud hosting is when Admin By Request hosts the gateway between your servers and the portal using a Cloudflare tunnel. Cloud hosting is the default for Unattended Access and is used when no on-premise gateway is detected. In fact, when first enabling Unattended Access, the CLOUD tab will not even be visible, since it is enabled by default and requires no configuration.
If configuring an on-premise gateway, the CLOUD tab becomes visible, allowing you to disable it in favor of the on-premise gateway.
Cloud hosting requires installation of the Admin By Request Server endpoint software. If this is not an option or you have devices on which you cannot install the endpoint software, you must use an on-premise gateway.
This option should only be disabled if you have on-premise gateways and want to make sure servers outside the gateway networks cannot be accessed.
|
Setting |
Type |
Description |
|---|---|---|
|
Allow cloud gateway |
Toggle Default: On |
On - Allows the remote access gateway to be hosted by Admin By Request in the cloud. Off - The remote access gateway cannot be hosted in the cloud. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
ON-PREMISE tab
On-premise gateways are used to create a create a traffic gateway from the Admin By Request portal to your internal network. You can set up multiple gateways on multiple networks and limit access to specific users and groups via portal user scopes and sub settings.
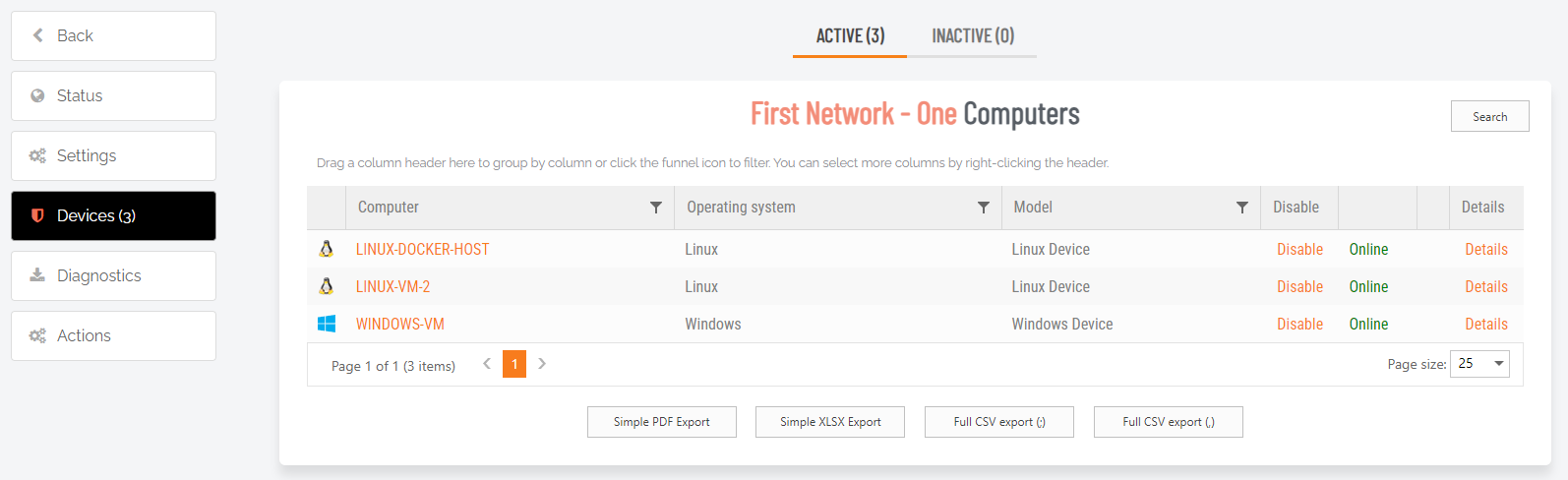
Gateway computers, accessed via link Computers (n), are the devices that can be remote controlled through this gateway. Note the following:
-
Computers will appear based on discovery.
-
If computers appear that are not supposed to be made available for remote control, they can be deleted from the list.
-
If computers have been deleted by mistake, they can be restored under the "Deleted" tab.
-
Offline computers are computers that were not seen in last discovery.
|
Setting |
Type |
Description |
|---|---|---|
|
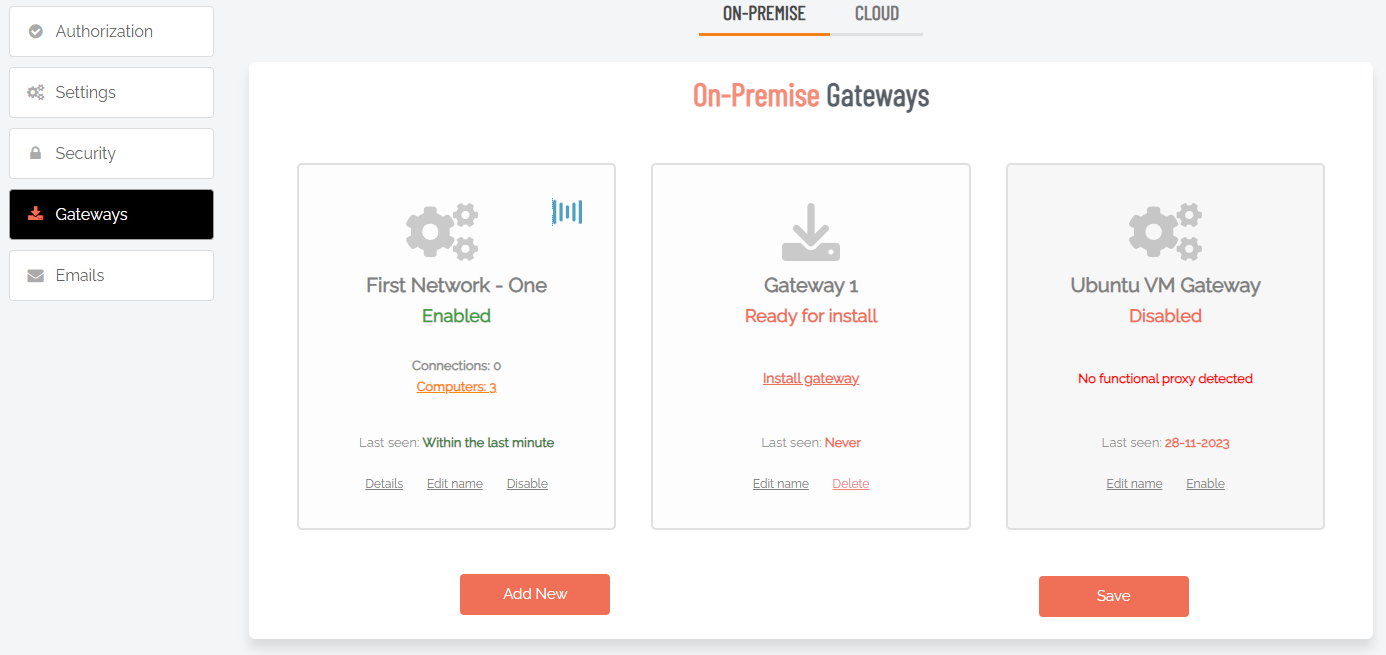
Gateway |
Dashboard |
Displays information about existing gateways and provides links and buttons for updating, drilling down further and creating new gateways. |
|
Computers (n) |
Link (drill-down) |
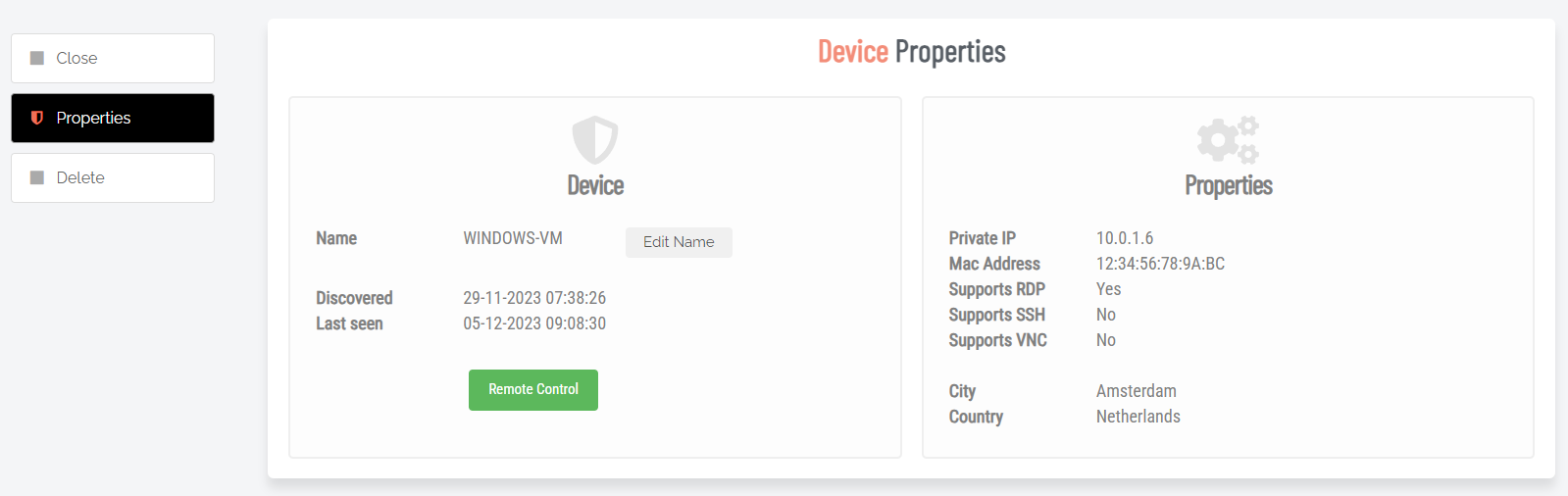
Clicking the drill-down link opens an inventory-style list of all devices accessible via this gateway. Devices can be entered manually or they can be discovered. Devices can be ACTIVE or INACTIVE and are displayed in the corresponding tab:
Use the Disable/Enable links to make a device active/inactive respectively. Use the Search button to search for devices in large lists and the Export buttons to export data in the format shown. |
|
Details |
Link (drill-down) |
Shows the current status of the gateway, including Internet and LAN availability. Use the Run discovery now button to renew discovery of connected devices. |
|
Edit name |
Link |
Opens the gateway name field in edit mode, allowing the name to be changed. Click the small Save icon to update. |
|
Disable |
Link |
Disables the gateway. Click Save to confirm. |
|
Add New |
Button |
Creates a new gateway and labels it Gateway 1, Ready for install. Edit the name if necessary and click Save to save the new gateway. Note that there are more steps required: once a gateway has been created, it must be installed. Refer to New Gateway for information on how to install a gateway. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
-
In the portal, go to Secure Remote Access > Settings > Unattended Access Settings and select menu Gateways.
-
Click Computers (n) for the gateway connected to the device.
-
In the list of computers, click the device you wish to connect to (either the Computer or Details column).
-
The connection should now appear directly in your browser.
To add a new gateway:
-
From the Gateway Dashboard, click Add New.
-
Click Save.
-
Click link Install gateway (see below).
Returns to the Dashboard.
Once a gateway has been created (and saved), it is ready to be installed, which is initiated by clicking link Install gateway from the Dashboard. This opens the Install menu for the new gateway.
DOCKER tab
Select the technical infrastructure that corresponds to your environment. The Install menu opens by default at the DOCKER tab, but KUBERNETES and CUSTOM are also available.
Docker can be used to host the gateway containers. Use the clipboard button Copy YML to clipboard to copy the Docker Compose YML file content to the local computer's clipboard and paste it into a docker-compose.yml file in the root of your Docker host.
We strongly recommend not to save the content to a local file. We use the clipboard to avoid downloading the content to your local machine because it contains your highly sensitive private keys that should never reside outside your Docker host. Once the gateway reports home, this page will disappear forever to protect your private keys.
|
Setting |
Type |
Description |
|---|---|---|
|
Automatic enrollment |
Toggle Default: On |
On - Discovered devices appear immediately in the ACTIVE list and the inventory. Automatic enrollment is recommended. Off - Discovered devices appear in the INACTIVE list and devices will need to be enabled one-by-one. |
|
Copy YML to clipboard |
Button |
Copies the required YML code to the local computer's memory. |
|
See content |
Link |
Displays the YML code in a scrollable window. |
KUBERNETES tab
Kubernetes is typically highly customized on your side and we therefore only provide a simple yml file compilation in a single file.
Parameter names and values in the Kubernetes settings table are the same as for the DOCKER tab.
CUSTOM tab
In a custom setup, you will need the secret keys listed in the yml file. Please contact us for more information, if necessary.
Parameter names and values in the Custom settings table are the same as for the DOCKER tab.
Returns to the Dashboard.
Shows the current status of the gateway, including Internet and LAN availability.
Use the Run discovery now button to renew discovery of connected devices.
DISCOVERY tab
Discovery finds computers and devices on your network where the gateway is installed. It is necessary to run discovery at least once to detect devices on your network. Once initial discovery is complete, you can disable it and enable temporarily when you know there are new devices on the network.
Automatic enrollment means that new devices appear right away in your inventory and are ready for remote control. If this option is off, new devices appear as Disabled in the Devices (n) menu - disabled devices can be enabled manually one-by-one.
|
Setting |
Type |
Description |
|---|---|---|
|
Enable discovery |
Toggle Default: On |
On - The discovery service is enabled and will check for new devices at the frequency set in Discovery interval. Off - The discovery service is disabled - no new devices will be found when they are attached to the network. |
|
Automatic enrollment |
Toggle Default: On |
On - Discovered devices appear immediately in the ACTIVE list and the inventory. Automatic enrollment is recommended. Off - Discovered devices appear in the INACTIVE list and devices will need to be enabled one-by-one. |
|
Discovery interval |
Selection Default: 15 m |
How often the discovery service checks for new devices. There are ten options, ranging from 5 minutes to weekly. |
|
Save |
Button |
Saves changes made to this setting. |
TUNNEL tab
Cloudflare Tunnel sits between the end user and your gateway to relay traffic.
If you disable the tunnel, you must provide your own on-premise webserver to relay incoming traffic to this gateway. Refer to What if I don’t want to use Cloudflare tunnels? for more information.
When changing this configuration, you can check under Status within a minute if the connection is functional.
|
Setting |
Type |
Description |
|---|---|---|
|
Use Cloudflare tunnel |
Toggle Default: On |
On - A Cloudflare-hosted tunnel will be created for traffic. Off - A Cloudflare tunnel will not be used. You must configure your own webserver to relay traffic. |
|
Save |
Button |
Saves changes made to this setting. |
IP RESTRICTIONS tab
IP Restrictions limits which IP addresses the user's browser can connect from. This feature can be used for highly sensitive networks. A few things to consider:
-
It may be more flexible to set IP address restrictions on your firewall in front of the gateway instead.
-
Your gateway may be configured to not receive requests from the internet, in which case the user must be on the local network or connect using VPN.
-
Your portal users should always be set up with Single Sign-On. Most SSO providers have conditional access, where you can set, for example, countries from which access is allowed.
|
Setting |
Type |
Description |
|---|---|---|
|
IP restrictions |
Toggle Default: Off |
On - Limits the IP addresses from which browsers can connect. Shows the .Allowed IPs field. Off - There are no IP restrictions. Hides the .Allowed IPs field. |
|
Allowed IPs |
Text |
A list of IP addresses that are permitted to access the gateway. Note that no computer will be able to connect to the gateway if IP restrictions is on and there are no entries in the list. |
|
Save |
Button |
Saves changes made to this setting. |
Clicking the drill-down link opens an inventory-style list of all devices accessible via this gateway. Devices can be entered manually or they can be discovered.
Devices can be ACTIVE or INACTIVE and are displayed in the corresponding tab:
-
ACTIVE: able to be connected to via Unattended Access and consume a license.
-
INACTIVE: are not able to be connected via Unattended Access and do not consume a license.
Use the Disable/Enable links to make a device active/inactive respectively.
Use the Search button to search for devices in large lists and the Export buttons to export data in the format shown.
Gateway computers are those that can be remote controlled through this gateway. Computers appear based on discovery. If computers appear that are not supposed to be made available for remote control, they can be disabled, which moves them to the INACTIVE tab. Any computers currently disabled can be enabled, which moves them to the ACTIVE tab. Offline computers are computers that were not seen in the last discovery.
CALLBACKS tab
Displays a log-style view of gateway callback events. Includes columns for:
-
Time - date and time the activity occurred.
-
Call - the type of event.
-
Data - the raw data in JSON form.
Rows can be sorted according to a column by clicking the column title (click again to reverse the sort), and data can be filtered by clicking a column's filter icon. Columns can also be rearranged by clicking, holding and dragging a column to another position.
Use the Refresh button to get the latest diagnostics.
LOGS tab
Click the Request Logs button to retrieve log files. Takes up to 60 seconds.
PURGE DEVICES tab
Purge devices removes devices that are offline in the Devices (n) ACTIVE or INACTIVE tabs.
Purged devices are effectively removed from the inventory, although they will automatically re-appear if they are discovered at a later time.
DELETE GATEWAY tab
Delete gateway deletes the gateway. Any computers in the Devices (n) menu that are not discovered by other gateways will not be accessible until a new gateway discovers these.
Deleting a gateway can lead to inaccessible devices.
 Emails
Emails
Portal menu: Secure Remote Access > Settings > Unattended Access Settings > Emails
 Request Emails tab
Request Emails tab
Emails go out when Require approval is turned On under Authorization. You can create your own email templates here with information specific to your company, such as a Help Desk phone number and custom instructions.
|
Setting |
Type |
Description |
|---|---|---|
|
Email template |
Selection Default: Run As Admin: Approved email |
Run As Admin | Admin Session: Approved email - Loads a template that advises the user (i.e. requester) that the request for access has been approved. Run As Admin | Admin Session: Denied email - Loads a template that advises the request for access has been denied without giving a reason. Run As Admin | Admin Session: Denied with reason - Loads a template that advises the request for access has been denied and provides the reason. Admin notify: New request - Loads a template that advises the administrator (i.e. person who approves or denies) that a request for access is waiting for attention. Admin notify: Malware detected - Loads a template that advises the administrator that malware has been detected, including a link to the Auditlog. |
|
Email sender |
Text Default: Admin By Request Team |
The email address to be used as the sender for the email. Can be used with custom domains. Use the Email address button to set up custom domains. Refer to Email Domain for more information on configuring an email address to be used as the sender for all user notifications. |
|
Email subject |
Text Default: Admin By Request |
Text that will appear in the subject line of emails. |
|
Get default |
Button |
Loads the default Email template for the option selected. NOTE:
|
|
Email address |
Button |
Switches to Email Domain in Tenant Settings in the portal, allowing you to use a custom domain as the sender. This allows sending email from domains other than @adminbyrequest.com. NOTE: This is optional, but you cannot add an email sender field of e.g. "tom@mydomain.com" unless you have first set up the custom email domain "mydomain.com" via the Email Domain setting in the portal (Settings > Tenant Settings > Email Domain). |
|
Template body |
Formatted text |
The body of the email to be sent. Includes three views:
Dynamic content tagsTags can be used in the body, which are place holders in curly braces. These are replaced with actual request values when emails are sent. The following tags are available:
|
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Ticketing System tab
Ticketing System tab
You can set up an email notification to your ticketing system and embed the tags below for dynamic content.
|
Setting |
Type |
Description |
|---|---|---|
|
Ticket system email |
Text |
The email address to which emails intended for your ticket system will be sent. For example: itsupport@mycompany.com |
|
Email sender |
Text Default: Admin By Request Team {ID} |
The email address to be used as the sender for the email. Can be used with custom domains. Use the Email address button to set up custom domains. |
|
Email subject |
Text Default: Admin By Request |
Text that will appear in the subject line of emails. |
|
Get default |
Button |
Loads the default Email template for the option selected. NOTE:
|
|
Email address |
Button |
Switches to Email Domain in Tenant Settings in the portal, allowing you to use a custom domain as the sender. This allows sending email from domains other than @adminbyrequest.com. NOTE: This is optional, but you cannot add an email sender field of e.g. "tom@mydomain.com" unless you have first set up the custom email domain "mydomain.com" via the Email Domain setting in the portal (Settings > Tenant Settings > Email Domain). |
|
Template body |
Formatted text |
The body of the email to be sent to the ticketing system. Includes three views:
Dynamic content tagsTags can be used in the body, which are place holders in curly braces. These are replaced with actual request values when emails are sent. The following tags are available:
Ticket IDYou can find a ticket by its ticket ID using the Search button in the Auditlog. Voided textIf a line has one or more tags and all tags in the line are empty, the entire line is automatically removed. |
Remote Access notification events
|
Setting |
Type |
Description |
|---|---|---|
|
User requests approval |
Toggle Default: On |
On - Sends a notification for User requests approval. Off - Does not send a notification. |
|
Admin approves user request |
Toggle Default: On |
On - Sends a notification for Admin approves user request. Off - Does not send a notification. |
|
Admin denies user request |
Toggle Default: Off |
On - Sends a notification for Admin denies user request. Off - Does not send a notification. |
|
User starts remote session |
Toggle Default: Off |
On - Sends a notification for User starts remote session. Off - Does not send a notification. |
|
User finishes remote session |
Toggle Default: Off |
On - Sends a notification for User finishes remote session. Off - Does not send a notification. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Sub Settings
Portal menu: Secure Remote Access > Settings > Unattended Access Sub Settings
Sub settings will overrule the global settings for the users or computers to which they apply. Both users and computers can be in Active Directory groups or organizational units.
If a user or computer hits multiple sub settings, the first in listed order that includes the setting concerned wins.
 Overruling a global setting
Overruling a global setting
As with sub-settings for EPM servers and workstations, SRA sub-settings mirror their respective global settings, with the addition of an Overrule global settings switch.
The following table lists the settings and sub-settings structure for both Unattended Access and Remote Support:
|
Unattended Access |
Remote Support |
|---|---|
|
Authorization |
Authorization |
|
Settings |
Endpoint |
|
Security |
Settings |
|
Gateways |
Security |
|
Emails |
Emails |
Each of these can be on or off, which is controlled by a Global Settings Overrule:
|
Setting |
Type |
Description |
|---|---|---|
|
Overrule global settings |
Toggle Default: On |
On - This setting will overrule its associated global setting. The global setting fields are then undimmed and become available for editing. Off - This setting will not overrule its associated global setting. The global setting fields remain dimmed. |
 Scope for sub-settings
Scope for sub-settings
The key to sub-settings is to define and activate their Scope.
In the portal sub-settings, Scope is the second-top menu item, immediately below the < Back button.
|
Setting |
Type |
Description |
|---|---|---|
|
Active |
Toggle Default: Off |
On - Sub-settings are active for the set named in Sub settings name. Off - Sub-settings are not active .for the set named in Sub settings name. |
|
Sub settings name |
Text |
The name assigned to this set of sub-settings. |
|
Portal user in group |
Text |
A list of groups into which users are placed, with multiple groups on separate lines. |
|
Computer in group |
Text |
A list of groups into which computers are placed, with multiple groups on separate lines. |
|
Computer in OU |
Text |
A list of organizational units into which computers are placed, with multiple OUs on separate lines. |
|
Network scope |
Toggle One entry for each Gateway Default: Off |
On - Scope is active for this gateway. Off - Scope is not active for this gateway. Network scope means that these sub settings only apply to the selected gateway combination. A gateway represents an on-premise LAN - if no toggles are on, there is no network scope. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 About sub-settings scope
About sub-settings scope
Note the following:
-
Tiering can be achieved by setting up a gateway on each tier and set portal user and sub settings network scopes.
-
Computer scope does not work for discovered devices, because the server endpoint software is required to collect groups and OUs.
-
Entra ID / Azure AD groups require you to set up the Entra ID Connector.
-
All scopes must be met. If multiple user groups and computer Organizational Units (OUs) are specified, the user must be member of at least one of the groups and the computer in one of the OU locations.
In the portal text fields, multiple groups or OUs (Organizational Units) must be specified on separate lines. OUs can be specified as either:
-
The bottom name, e.g. Sales. Any OU named Sales will match.
-
Path from root using backslashes, e.g. \US\Florida\Sales.
-
The fully distinguished name, e.g. C=US,ST=Florida,OU=Sales.