Tenant Settings
Identity
 Entra ID tab
Entra ID tab
Portal menu: Settings > Tenant Settings > Identity > ENTRA ID
The Entra ID Connector allows endpoints to retrieve Entra ID (previously Azure AD) groups for sub-settings. The Entra ID Connector is NOT used for single sign-on to the portal; it is used solely for sub-setting groups.
If you are using on-premise Active Directory, you do not need to configure anything - collection of groups for Active Directory is "configuration-less".
Example values:
|
acme.onmicrosoft.com |
|
xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
|
azVqedkQlVX9bHLBZjGCQZ6+iZIh4goI7u53i9WlZN8= |
Refer to https://learn.microsoft.com/en-us/entra/identity-platform/quickstart-register-app for more information on registering apps with the Microsoft identity platform.
The National Cloud regions of Azure are designed to make sure that data residency, sovereignty, and compliance requirements are honored within geographical boundaries.
|
Setting |
Type |
Description |
|---|---|---|
|
Enable Connector |
Toggle Default: Off |
On - Turns on the Entra ID Connector and allows endpoints to retrieve Entra ID groups for sub-settings. Off - The Entra ID Connector is disabled and endpoints will use sub-settings as described under "Sub-Settings", rather than using Entra ID rules. |
|
Tenant |
Text |
Standard email address format. Use a new line for each address. |
|
Application ID |
Text |
The value assigned to an application when it is registered with the Microsoft identity platform. |
|
Secret Key |
Text |
The application certificate or client secret generated when the app is registered. |
|
Hybrid Preference |
Selection Default: Prefer Active Directory |
An option available for selection when a computer is both AD-joined and the user makes an Entra ID Workjoin:
|
|
National Cloud |
Toggle Default: Off |
On - Enables selection of a physically isolated instance of Azure. Reveals National Service, which is where the actual geographic instance is selected. Off - Disables selection of a physically isolated instance of Azure. Hides National Service. |
|
National Service (hidden if National Cloud is Off) |
Selection Default: US Government L4 / GCC High |
The geographic instance selected:
|
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Google tab
Google tab
Portal menu: Settings > Tenant Settings > Identity > GOOGLE
The Google Connector is used to retrieve Google groups for sub-settings from endpoints that use the Windows Google identity provider.
The configuration is tested when Save is clicked.
Version required
Google Connector is supported in Windows Endpoint 8.5 or newer.
|
Setting |
Type |
Description |
|---|---|---|
|
Enable Connector |
Toggle Default: Off |
On - Turns on the Google Connector, allowing the retrieval of groups from endpoints that use the Windows Google identity provider. Off - The Google Connector is disabled. |
|
Admin Account (disabled if Enable Connector is Off) |
Text |
The Google account that issues the secret key. |
|
JSON Private Key (disabled if Enable Connector is Off) |
Text |
The Google API key used to retrieve groups. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 JumpCloud tab
JumpCloud tab
Portal menu: Settings > Tenant Settings > Identity > JUMPCLOUD
The JumpCloud Connector is used to retrieve groups for sub-settings from endpoints that use the Windows JumpCloud identity provider.
The configuration is tested when Save is clicked.
Version required
JumpCloud Connector is supported in Windows Endpoint 8.5 or newer.
|
Setting |
Type |
Description |
|---|---|---|
|
Enable Connector |
Toggle Default: Off |
On - Turns on the JumpCloud Connector, allowing the retrieval of groups from endpoints that use the Windows JumpCloud identity provider. Off - The JumpCloud Connector is disabled. |
|
API Key (disabled if Enable Connector is Off) |
Text |
The JumpCloud API key used to retrieve groups. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Okta tab
Okta tab
Portal menu: Settings > Tenant Settings > Identity > OKTA
The Okta Connector is used to retrieve groups for sub-settings from Okta groups.
Endpoints must be joined to either Active Directory or Entra ID.
The configuration is tested when Save is clicked.
Version required
Okta Connector is supported in Windows Endpoint 8.5 or newer.
|
Setting |
Type |
Description |
|---|---|---|
|
Enable Connector |
Toggle Default: Off |
On - Enables the Okta Connector. Off - The Okta Connector is disabled. |
|
URL (disabled if Enable Connector is Off) |
Text |
The Okta URL identifying the tenant. |
|
Secret Key (disabled if Enable Connector is Off) |
Text |
The Okta API key used to retrieve groups. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Data
 Privacy tab
Privacy tab
Portal menu: Settings > Tenant Settings > Data > PRIVACY
The PRIVACY tab provides a way to anonymize data collection, so that data is still logged and available for analysis, but identification of individual users is not possible.
Key points:
-
Obfuscation creates an alias for each user. You can track activity, but you cannot decode the true identity of any user.
-
Collection of data should be left on unless you have a reason not to do this. If disabled, you will have to find contact information elsewhere.
-
Inventory collects both hardware and software inventory. If disabled, only the computer name is collected and shown in the "Inventory" menu.
-
Geo-tracking maps the endpoint IP address to location using a public IP-to-location database to show in inventory and reports.
Changes apply only to new data. This is by design to avoid accidentally deleting existing data.
|
Setting |
Type |
Description |
|---|---|---|
|
Obfuscate user accounts |
Toggle Default: Off |
On - Create an alias for each user. Off - Do not create aliases for users. |
|
Collect user names |
Toggle Default: On |
On - Record the name of each user associated with an ABR event. Off - Do not record user names. |
|
Collect user email addresses |
Toggle Default: On |
On - Record email addresses associated with a user. Off - Do not record email addresses. |
|
Collect user phone numbers |
Toggle Default: On |
On - Record phone numbers associated with a user. Off - Do not record phone numbers. |
|
Collect inventory |
Toggle Default: On |
On - Record hardware and software inventory data. Off - Do not record inventory data. |
|
Allow geo-tracking |
Toggle Default: On |
On - Record the location of the public IP address associated with the user’s endpoint. Off - Do not record IP addresses. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
If you want to record device owners for endpoints, Collect inventory must be ON.
This is because there is no way to identify the device owner if no inventory data is collected. Therefore, if Collect inventory is OFF (portal menu Settings > Tenant Settings > Data > PRIVACY), setting Lock device to owner (portal menu Endpoint Privilege Management > Settings > [OS] Settings > Lockdown > OWNER) has no effect.
 Retention tab
Retention tab
Portal menu: Settings > Tenant Settings > Data > RETENTION
Data retention is the period of time, we keep your auditlog data.
Be careful decreasing the data retention period. If you decrease the data retention period and Save, data older than the new period will be permanently deleted.
|
Setting |
Type |
Description |
|---|---|---|
|
Data Location |
Read-only text |
The geographic location of the data center that stores the data accessed via this portal. |
|
Retention period |
Selection Default: 1 year |
The length of time the auditlog data accessed via this portal will be stored and made available for access. Values:
|
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
You can set the Auditlog retention policy in Settings > Tenant Settings > Data > RETENTION. The range is from three months to five years and the standard period (i.e. the default) is one year.
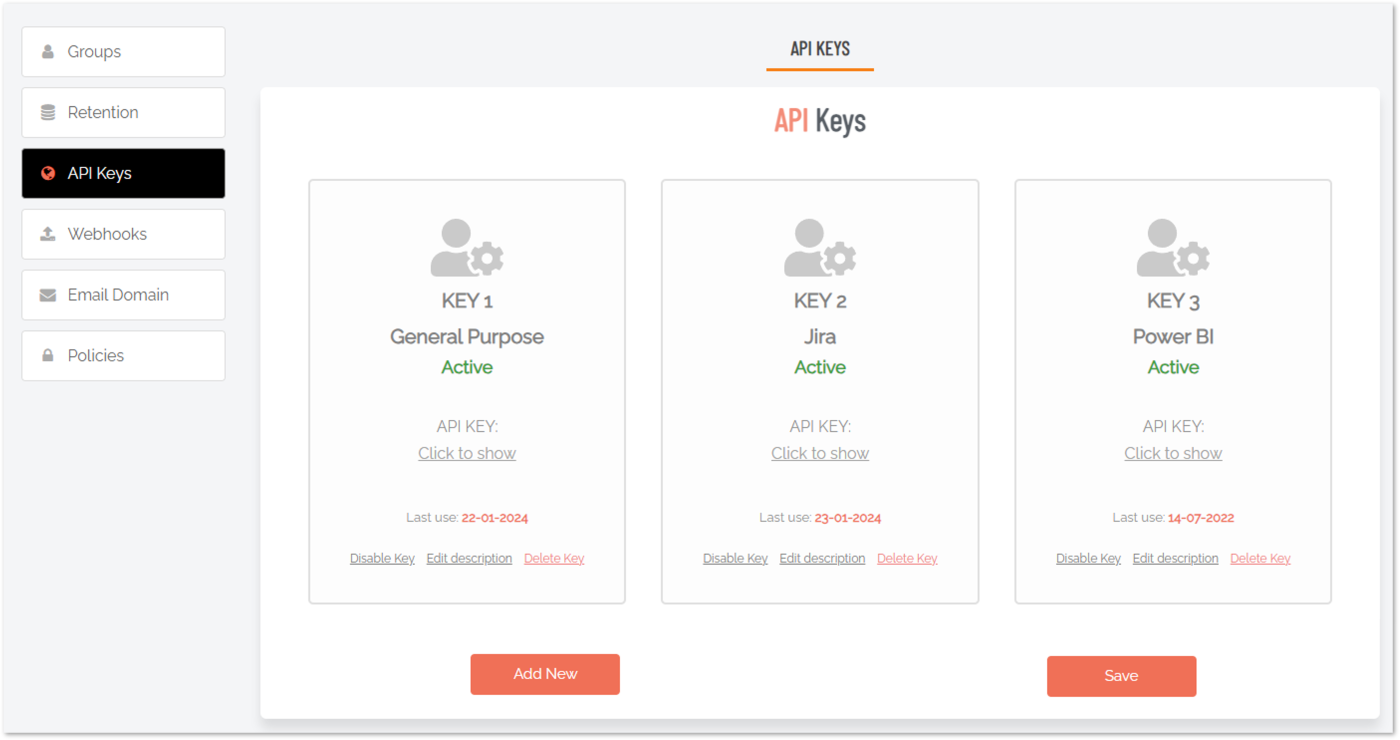
 API Keys tab
API Keys tab
Portal menu: Settings > Tenant Settings > Data > API KEYS
API Access allows you to extract your data through our public API. Refer to this page for an overview of how our API works.
Your API prefix is one of the following (check the link to your API server at the bottom of the Tenant Settings portal page or on the Requests API documentation page):
-
https://dc1api.adminbyrequest.com
-
https://dc2api.adminbyrequest.com
The API Keys menu provides both dashboard and detailed information views. The default view is the API Dashboard, which provides an overview of existing API Keys and links and buttons for further information:
|
Setting |
Type |
Description |
|---|---|---|
|
API Keys |
Dashboard |
Displays information about all existing API keys and provides links and buttons for updating, drilling down further and creating new API keys. |
|
Click to show |
Link |
Displays the API key and provides a link so that it can be copied to the clipboard. |
|
Disable key |
Link |
Changes the key from Active to Disabled. Click Save to confirm the change. |
|
Edit description |
Link |
Opens the API key name field in edit mode, allowing the name to be changed. Click the small Save icon to update. |
|
Delete key |
Link |
Deletes the API key. Click Save to confirm. |
|
Add New |
Button |
Creates a new Active API Key and labels it General Purpose. Edit the name as necessary (via link Edit description) and click Save to save the new key. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Webhooks tab
Webhooks tab
Portal menu: Settings > Tenant Settings > Data > WEBHOOKS
Webhooks are a way for you to subscribe to events in real-time instead of pulling data out in intervals from our public API.
A webhook is often referred to as a web callback or HTTP push API. Your server must return HTTP 200 OK to signal that the data is received. Refer to this page for webhook and API documentation.
The following IP addresses are used to send webhooks:
-
If your data is located in Europe (Netherlands): 104.40.134.41
-
If your data is located in the USA: 52.168.52.158
-
If your data is located in the UK: 131.145.14.218
-
If your data is located in Europe (Germany): 9.141.94.163
-
If your data is located in Asia (Singapore): 135.171.17.26
These are the IP addresses we use to send webhook data to you. If you need to allow incoming traffic from us, please allow the relevant IP address.
Webhooks are global across Windows, Mac, Linux and Server settings.
|
Setting |
Type |
Description |
|---|---|---|
|
Webhooks |
Read-only Table |
A list of the webhooks created by you for your tenant. Use the Edit link to change Webhook data and the Delete link to remove it. |
|
Create Webhook |
Button |
Creates a new webhook. |
Create Webhook Settings
|
Setting |
Type |
Description |
|---|---|---|
|
Enabled |
Toggle Default: On |
On - This webhook is enabled. Once the Create Webhook button is clicked, Enabled is set to On. Off - This webhook is disabled. |
|
Name |
Text |
Used in the list of Webhooks only to identify one Webhook from another. |
|
Push Data |
Selection (see Description) Default: Auditlog: Entry change |
The type of data to push:
|
|
Pushed Events |
Selection (see Description) Default: All events |
The type of events to push:
|
|
URL |
Text |
The web address that this webhook should push to. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Subscribed Events Table
This table operates as a typical parameter table, where parameters on the left are not operational, while parameters on the right are. Select a parameter by first clicking its check box and then clicking Add >> to make it operational.
Don't forget to Save when done.
Auto-Update
 Windows Workstation tab
Windows Workstation tab
Portal menu: Settings > Tenant Settings > Auto-Update > WINDOWS WORKSTATION
Internet Auto-update
Auto-update over the Internet pushes endpoint software updates to clients in the same way as
Admin By Request endpoint software updates are less than 3 megabytes in size and will typically be pushed in bulk four to eight weeks after general availability.
You can freely update clients while having internet updates on. Only clients with a lesser version than the current internet push version will be hit by the bulk endpoint software updates.
|
Setting |
Type |
Description |
|---|---|---|
|
Auto-update over the Internet |
Toggle Default: On |
On - Updates to Admin By Request on endpoints will happen over the Internet independently of anything else. Off - Updates will not be done over the Internet. They may still be done manually |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
LAN Auto-update
LAN updates force Admin By Request clients to pull endpoint software updates from a local network share.
You must manually download a newer version of the client in the portal "Download" menu and drop the file on the UNC path - generally, clients will automatically update within 4 hours.
The UNC path can be without a file name, in which case clients will use the highest version on the shared location. You can manually start the task on an endpoint by logging in as administrator and start the scheduled task "Admin By Request Auto-Updater".
The updater uses the local system account on clients. The share must have read access for the domain group "Domain Computers". If you have access to your netlogon share, this is by default readable to computer accounts.
|
Setting |
Type |
Description |
|---|---|---|
|
Update over LAN |
Toggle Default: On |
On - Updates to Admin By Request on endpoints will happen over the local network. Off - Updates will not be done over the local network. They may still be done over the Internet. |
|
UNC path |
Text |
Path to a shared location on the local network where endpoint client software is stored. If file name is included, that file will be installed. If file name is not included (i.e. path only), the latest version of client software will be used. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Windows Server tab
Windows Server tab
Portal menu: Settings > Tenant Settings > Auto-Update > WINDOWS SERVER
Internet Auto-update
Auto-update over the Internet pushes endpoint software updates to clients in the same way as
Admin By Request endpoint software updates are less than 3 megabytes in size and will typically be pushed in bulk four to eight weeks after general availability.
You can freely update clients while having internet updates on. Only clients with a lesser version than the current internet push version will be hit by the bulk endpoint software updates.
|
Setting |
Type |
Description |
|---|---|---|
|
Auto-update over the Internet |
Toggle Default: On |
On - Updates to Admin By Request on endpoints will happen over the Internet independently of anything else. Off - Updates will not be done over the Internet. They may still be done manually |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
LAN Auto-update
LAN updates force Admin By Request clients to pull endpoint software updates from a local network share.
You must manually download a newer version of the client in the portal "Download" menu and drop the file on the UNC path - generally, clients will automatically update within 4 hours.
The UNC path can be without a file name, in which case clients will use the highest version on the shared location. You can manually start the task on an endpoint by logging in as administrator and start the scheduled task "Admin By Request Auto-Updater".
The updater uses the local system account on clients. The share must have read access for the domain group "Domain Computers". If you have access to your netlogon share, this is by default readable to computer accounts.
|
Setting |
Type |
Description |
|---|---|---|
|
Update over LAN |
Toggle Default: On |
On - Updates to Admin By Request on endpoints will happen over the local network. Off - Updates will not be done over the local network. They may still be done over the Internet. |
|
UNC path |
Text |
Path to a shared location on the local network where endpoint client software is stored. If file name is included, that file will be installed. If file name is not included (i.e. path only), the latest version of client software will be used. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Mac tab
Mac tab
Portal menu: Settings > Tenant Settings > Auto-Update > MAC
Internet Auto-update
Auto-update over the Internet pushes endpoint software updates to clients in the same way as
Admin By Request endpoint software updates are less than 3 megabytes in size and will typically be pushed in bulk four to eight weeks after general availability.
You can freely update clients while having internet updates on. Only clients with a lesser version than the current internet push version will be hit by the bulk endpoint software updates.
|
Setting |
Type |
Description |
|---|---|---|
|
Auto-update over the Internet |
Toggle Default: On |
On - Updates to Admin By Request on endpoints will happen over the Internet independently of anything else. Off - Updates will not be done over the Internet. They may still be done manually. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Linux tab
Linux tab
Portal menu: Settings > Tenant Settings > Auto-Update > LINUX
Linux Auto-Update
Linux endpoints are automatically updated through the Admin By Request package tree.
Email Domain
 Email Domain tab
Email Domain tab
Portal menu: Settings > Tenant Settings > Email Domain > EMAIL DOMAIN
Sender email address is an email address in your own domain that sends our all email notifications to users. You can only have one account for all notifications.
DNS records are required for us to be able to send emails on your behalf. We use Twilio SendGrid to send your notification emails. We will not attempt to send emails from your own domain until the DNS entries are verified.
|
Setting |
Type |
Description |
|---|---|---|
|
Use custom email |
Toggle Default: Off |
On - Use the custom email address entered into Sender email address. Off - Do not use a custom email address - all notifications to users will come from noreply@adminbyrequest.com. |
|
Sender email address |
Text |
The email address to be used as the sender for all user notifications. Has no effect if Use custom email is Off, in which case all notifications to users will come from noreply@adminbyrequest.com. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
|
Custom DNS Records |
Read-only Table |
A list of DNS records that need to be added to your DNS configuration for your domain so that emails are not marked as spam. |
|
Re-test DNS |
Button |
Check that the DNS records entered are working. |
Tenant
 Inactivity tab
Inactivity tab
Portal menu: Settings > Tenant Settings > Tenant > INACTIVITY
Inactivity block means that portal users that have not logged on for the selected period of time will be blocked from logging in to the portal for security reasons.
The portal user has to be unblocked by a different portal user in the portal user properties.
|
Setting |
Type |
Description |
|---|---|---|
|
Inactivity block |
Selection Default: No policy |
The length of time a portal user remains inactive for the block to take effect. Values:
No policy means users are never blocked. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Incidents tab
Incidents tab
Portal menu: Settings > Tenant Settings > Tenant > INCIDENTS
The email addresses listed here enable customers to be notified about events and incidents that are related to data protection and security. The addresses can be the same, or they can be different. They can even be left blank.
If these fields are left blank and an incident occurs, we will attempt to contact you via your subscriber e-mail address and/or through your designated sales channel.
|
Setting |
Type |
Description |
|---|---|---|
|
Privacy email |
Text (email address) |
The email address where customers wish to receive formal notices related to data protection. These notices include personal data breaches, updates to sub-processors, and other obligations as described in the Data Processing Agreement. |
|
Security email |
Text (email address) |
The email address where customers wish to receive security communications, These include incident alerts, vulnerability disclosures, and other information security notifications. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Delete tab
Delete tab
Portal menu: Settings > Tenant Settings > Tenant > DELETE
The DELETE tab under Tenant Settings allows a customer to remove their tenant entirely.
This action is irreversible and cannot be undone. Your data will be permanently lost and you will be logged out after deletion.
Deleting the tenant requires the following steps:
-
System settings rights (i.e. full admin access)
-
Uninstall all endpoints
-
Delete all copies of installer files
-
Type in your tenant name from the Summary page
-
Type in a verification code by email
|
Setting |
Type |
Description |
|---|---|---|
|
Tenant Name |
Text |
The name of your tenant. |
|
Email code |
Text |
A unique and one-time-use code sent to a designated email address. |
|
Send email code |
Button |
Send a one-time-use code to your designated email address. Enabled once the first four steps above are completed. |
|
Delete |
Button |
Final action to entirely remove your tenant. Enabled once the verification code at step five is entered. |