Windows Settings
Authorization
 Authorization tab
Authorization tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Authorization > AUTHORIZATION
Run As Admin
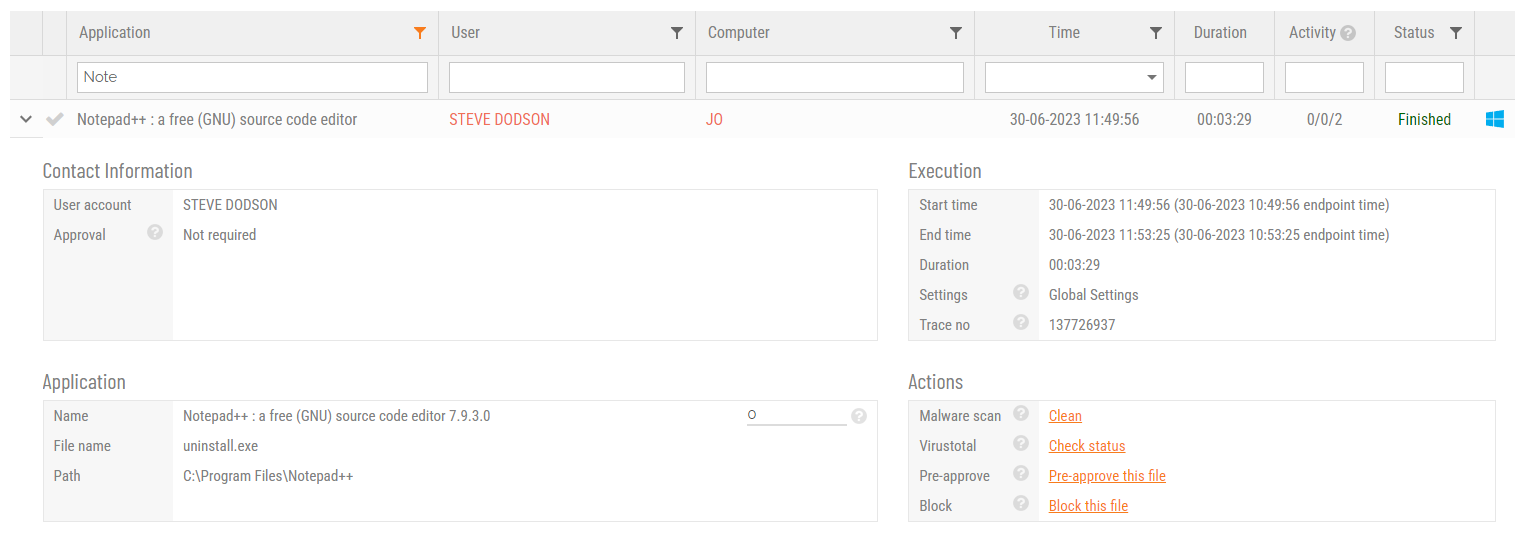
Run As Admin (also known as Application Elevation) elevates privileges for only the file or application selected.
It is invoked when a user runs a file that triggers User Account Control (UAC). The user is able to run the program sandboxed, without being local administrator. Only the process (not the user) has administrator rights. When enabled, the Explorer right-click icon is replaced by an Admin By Request icon.
|
Setting |
Type |
Description |
|---|---|---|
|
Allow Run As Admin |
Toggle Default: On |
On - Allows users to elevate privileges for a selected file. Enables Require approval and Require reason. Disables Block Run As Admin. Off - Denies users the ability to elevate privileges for a selected file. Enables Block Run As Admin, which is how users with admin credentials can still elevate privileges. |
|
Block Run As Admin (enabled only if Allow Run As Admin is OFF) |
Toggle Default: Off |
On - Denies users the ability to execute Run As Admin even if administrator credentials are available (i.e. no Off - Allows users with administrator credentials to execute Run As Admin (i.e. |
|
Require approval (hidden if Allow Run As Admin is OFF) |
Toggle Default: Off |
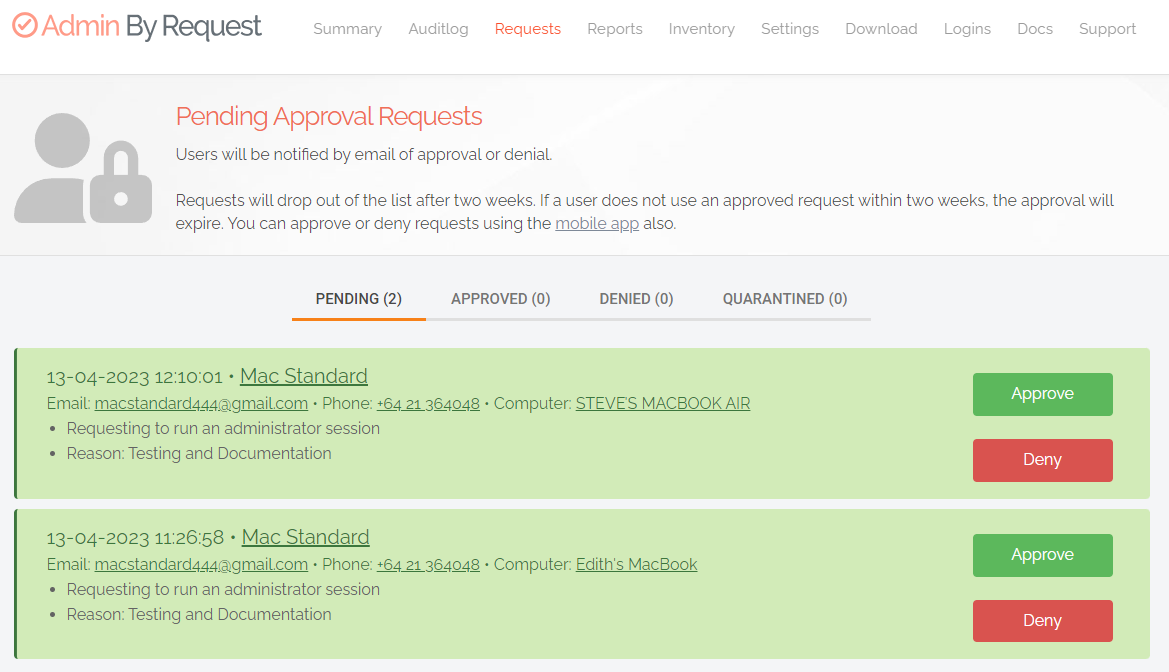
On - Sends a request to the IT team, which must be approved before elevation is granted. Makes Require reason mandatory (i.e. must be On). Off - Allows the user to elevate file privileges (and thus perform the action) as soon as the action is selected. For example, selecting "Run as administrator" to execute a program occurs immediately, without requiring approval. Makes Require reason optional (i.e. can be either On or Off). IMPORTANT
The Free Plan default for this setting is Off, which means that users simply have to request elevated access and it will be automatically granted. We recommend changing this setting to On. Note that the default setting may be changed in a future release. |
|
Require reason (hidden if Allow Run As Admin is OFF) |
Toggle Default: On |
On - Extends the Off - No reason is required by the user, but details of the actions performed are stored in the Auditlog. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Admin Session
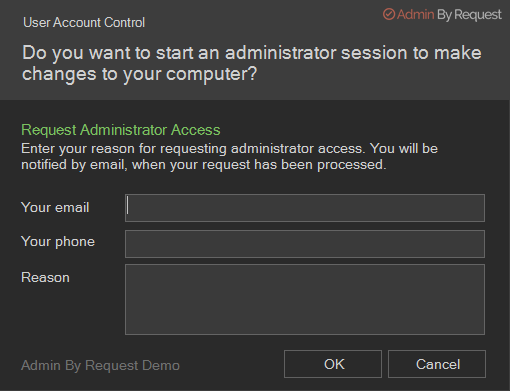
Admin Session (also known as User Elevation) elevates the current user's privileges across the endpoint for the duration of the session.
Invoked when the user clicks the
|
Setting |
Type |
Description |
|---|---|---|
|
Allow Admin Sessions |
Toggle Default: On |
On - Allows users to effectively become a local administrator for the number of minutes specified in Access time (minutes). Enables Require approval, Require reason and Access time (minutes). Off - Denies users the ability to become a local administrator. Hides all other options under Admin Session. |
|
Require approval |
Toggle Default: Off |
On - Sends a request to the IT team, which must be approved before the request is granted. Makes Require reason mandatory (i.e. must be On). Off - Allows the user to become a local administrator as soon as the request is made. Makes Require reason optional (i.e. can be either On or Off). IMPORTANT
The Free Plan default for this setting is Off, which means that users simply have to request elevated access and it will be automatically granted. We recommend changing this setting to On. Note that the default setting may be changed in a future release. |
|
Require reason |
Toggle Default: Off |
On - Extends the Off - No further information is required by the user, but user and computer details are stored in the Auditlog. |
|
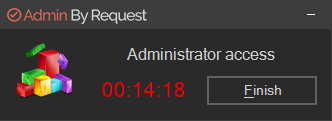
Access time (minutes) |
Integer Default: 15 (minutes) |
The maximum duration in minutes an Admin Session may last. This time must be sufficient for the user to install software or perform any other tasks that require elevation. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Notification tab
Notification tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Authorization > NOTIFICATION
Email notification to administrators is available when Require approval is checked under Authorization.
Notifications can be sent for the following scenarios:
-
Each new request for approval (Run As Admin) or admin session access (Admin Session)
-
When malware is detected (Workstation Settings > [OS] Settings > Malware)
-
When unattended remote access is requested (Unattended Access)
-
When either an end user or portal admin initiates a Remote Support session.
As with other request types, new requests for approval always appear under Requests > Pending in the Portal top menu. This is the case for both Endpoint Privilege Management and Secure Remote Access.
The Notification setting enables and configures additional email notification for new requests. If multiple email addresses are specified, they must be on separate lines.
Phone notification is separate and happens automatically via push notifications to phones with the mobile app installed.
|
Setting |
Type |
Description |
|---|---|---|
|
Send email notifications |
Toggle Default: Off |
On - Additional email notifications are sent to the email addresses listed in Email addresses. Off - Email notifications are not sent. |
|
Email addresses |
Text |
Standard email address format. Use a new line for each address. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Scope tab
Scope tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Authorization > SCOPE
Global scope excludes specific users and/or computers from using the endpoint software. Both Run As Admin and Admin Session are denied if the user or computer fall outside the global scope.
The user is presented with a PIN code option in case elevation is denied. The PIN code is found in the computer's inventory and can be used as an exception to the rule.
-
Local users cannot elevate when scope is used.
-
If using Entra ID / Azure AD groups for global scope, the Entra ID tab must be configured.
In the portal text fields, multiple groups or OUs (Organizational Units) must be specified on separate lines. OUs can be specified as either:
-
The bottom name, e.g. Sales. Any OU named Sales will match.
-
Path from root using backslashes, e.g. \US\Florida\Sales.
-
The fully distinguished name, e.g. C=US,ST=Florida,OU=Sales.
|
Setting |
Type |
Description |
|---|---|---|
|
User must be in group |
Text |
A list of groups into which users are placed, with multiple groups on separate lines. |
|
Computer in group |
Text |
A list of groups into which computers are placed, with multiple groups on separate lines. |
|
User must be in OU |
Text |
A list of organizational units into which users are placed, with multiple OUs on separate lines. |
|
Computer in OU |
Text |
A list of organizational units into which computers are placed, with multiple OUs on separate lines. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Endpoint
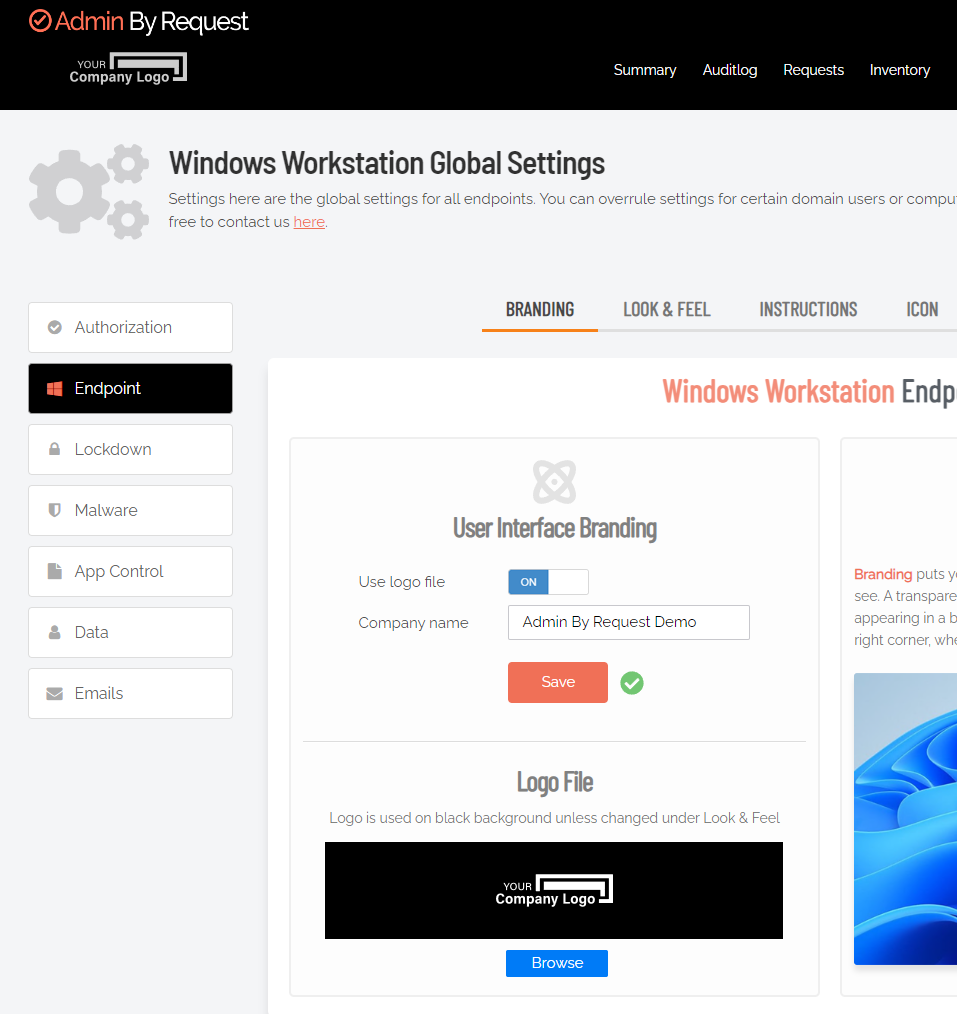
 Branding tab
Branding tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Endpoint > BRANDING
Branding puts your company name and logo on all user interfaces that users see.
Add the logo in the portal before turning on Use logo file and before downloading or otherwise deploying the installation file. Doing so makes sure your logo is included correctly.
There is no set logo size, although for best results, use a logo with the following attributes:
-
A transparent PNG file (recommended to avoid having the logo appearing in a box)
-
Less than 5 KB
-
Width: approximately 120 px
-
Height: approximately 40 px
The "Your Company Logo" example below is 1.84 KB, width 117 px, height 33 px.
Once entered in the portal, the logo appears at the top left, under "Admin By Request" as the example shows:
Your company logo also appears under "Admin By Request" in the Instructions window (Code of Conduct).
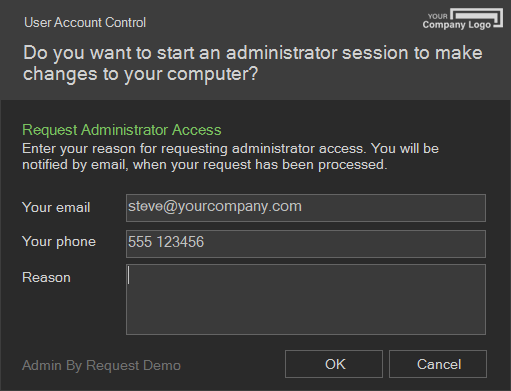
When users request an admin session, the logo replaces the "Admin By Request" logo in the top right of the UAC window:
|
Setting |
Type |
Description |
|---|---|---|
|
Use logo file |
Toggle Default: On |
On - Use the logo file selected under Logo file. Add the file before turning this setting on. Off - Do not use a logo file. |
|
Company name |
Text |
The name of the organization as it will appear in the portal and in Admin By Request dialog boxes on endpoints. |
|
Logo file |
Selection |
Use the Browse button to open an operating system File open dialog box. Locate and select a logo file. Add a file here before turning on the Use logo file setting. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Look & Feel tab
Look & Feel tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Endpoint > LOOK & FEEL
Email and phone settings control the behavior of the fields in the request form.
Skin determines if user interfaces are light or dark. Active skin choice can be used as an easy way to determine if sub-settings are in effect.
|
Setting |
Type |
Description |
|---|---|---|
|
Language |
Selection Default: Auto-detect |
Auto-detect - The language used is the same as that used by the operating system. Force <Language> - The language used is the one chosen from this selection list. |
|
Skin |
Selection Default: Auto-detect |
Auto-detect - The skin (light or dark) depends on what is currently being used by the operating system. Light - Uses a light skin for Admin By Request dialog boxes. Dark - Uses a dark skin for Admin By Request dialog boxes. Follow Operating System - The skin (light or dark) depends on what is currently being used by the operating system. |
|
Email field |
Selection Default: Mandatory |
Mandatory - Field appears in dialog boxes and must be filled-in. Optional - Field appears in dialog boxes, but does not have to be filled-in. Hide - Field does not appear in dialog boxes. |
|
Phone no field |
Selection Default: Mandatory |
Mandatory - Field appears in dialog boxes and must be filled-in. Optional - Field appears in dialog boxes, but does not have to be filled-in. Hide - Field does not appear in dialog boxes. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Instructions tab
Instructions tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Endpoint > INSTRUCTIONS
Run As Admin instructions
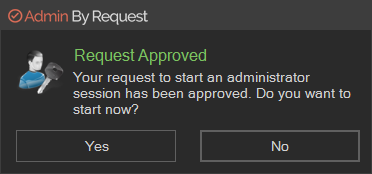
Instructions for Run As Admin are shown after the user invokes "Run As Administrator" and after the optional reason screen.
Instructions can be used as a Code of Conduct to inform the user of the consequences of abuse, what is logged or it could be used to show contact information for your help desk in case of problems. URLs are automatically detected and will appear as clickable links.
|
Setting |
Type |
Description |
|---|---|---|
|
Show instructions before start |
Toggle Default: Off |
On - Instructions are shown to the user per the period selected below via the drop-down. User clicks OK to close the instructions window. Off - Instructions are not shown. |
|
<Code of Conduct> <Instructions> <Display Frequency> |
Text Text (multiline) Selection |
A title for the instructions window. The instructions displayed to the user. A frequency indicating when instructions are to be displayed:
|
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
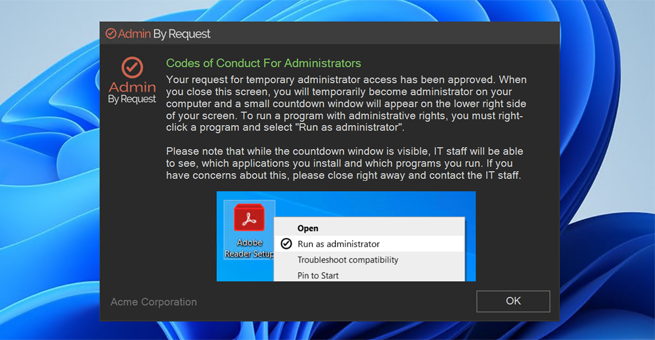
Admin Session instructions
Instructions for Admin Session are shown after the user invokes "Request Administrator Access" and after the optional reason screen.
Instructions can be used as a Code of Conduct to inform the user of the consequences of abuse, what is logged or could be used to show contact information for your help desk in case of problems. URLs are automatically detected and will appear as clickable links.
Setting Show "Run As" graphics under text can be used to inform users that User Account Control (UAC) is still enforced during a session. If this setting is enabled, it should be explained in the text.
How this appears to the user is shown below. If you added your own logo, it will appear at top left, where the "Admin By Request" logo is.
|
Setting |
Type |
Description |
|---|---|---|
|
Show instructions before start |
Toggle Default: Off |
On - Instructions are shown to the user per the period selected below via the drop-down selection field. User clicks OK to close the instructions window. Off - Instructions are not shown. |
|
<Code of Conduct> <Instructions> <Display Frequency> |
Text Text (multiline) Selection |
A title for the instructions window. The instructions displayed to the user. A frequency indicating when instructions are to be displayed:
|
|
Show "Run As" graphics under text |
Toggle Default: Off |
On - Includes an image with the illustrating how to select a program to "Run as administrator". Off - No image is shown with instructions. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Shortcuts tab
Shortcuts tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Endpoint > SHORTCUTS
An Admin By Request icon always appears in the system tray. By default, a shortcut is also placed on the user's desktop. This setting allows you to optionally turn the setting off, so that no shortcut is placed on the user's desktop.
If you enable the desktop shortcut, but do not specify a desktop shortcut name, the default "Administrator Access" text will be used in a localized version (at the time of writing, languages are English, German, French, Spanish, Danish, Swedish and Norwegian).
|
Setting |
Type |
Description |
|---|---|---|
|
Desktop shortcut |
Toggle Default: On |
On - An Admin By Request shortcut is placed on the user's desktop during installation. Off - No shortcut is placed on the desktop. |
|
Start menu shortcut |
Toggle Default: On |
On - An Admin By Request icon is placed on the user's desktop during installation. Off - No shortcut is placed on the desktop. |
|
Shortcut name |
Text |
The text to be used as a label for the shortcut. Leave this field blank to use the default text "Administrator Access". |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 UAC tab
UAC tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Endpoint > UAC
The
|
Setting |
Type |
Description |
|---|---|---|
|
|
Choice:
Default: Confirm |
Confirm - User must confirm with Yes or No (or via the reason screen) to perform the operation.. Multi-factor Authentication - User must validate identity using MFA through Single Sign-on. Choosing this option reveals Multi-factor Configuration (see table below). Authenticate - User must validate with credentials, face recognition, fingerprint, smartcard or similar.. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Multi-factor Configuration
Appears when Multi-factor Authentication is chosen as the
|
Setting |
Type |
Description |
|---|---|---|
|
Sign-on method |
Selection:
Default: |
Microsoft 365 / Entra ID - Use this as the SSO method. -- ADD NEW METHOD -- - Create a new method. Choosing this option takes you to the portal's Single Sign-on (SSO) Setup page. Note the following:
|
|
Email match |
Selection:
Default: |
No matching - If using Entra ID and this option is selected for Email match, the Entra ID Connector must be configured. This ensures that only users within the same Azure tenant can authenticate. Email match - MFA authentication must match the email address or User Principal Name (UPN) from Entra ID or Active Directory. Account separation - MFA authentication must be done via a secondary account. This is a requirement for those organizations wishing to maintain compliance with Cyber Essentials Plus. |
|
MFA on pre-approvals |
Toggle Default: Off |
On - Force multi-factor authentication on pre-approved applications. Off - Multi-factor authentication is not required on pre-approved applications |
Lockdown
 Admin Rights tab
Admin Rights tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Lockdown > ADMIN RIGHTS
Revoke admin rights at logon means that all user accounts will be downgraded from an Admin role to a User role, unless the account appears in the Excluded accounts list.
Excluded accounts are not removed at logon.
|
Setting |
Type |
Description |
|---|---|---|
|
Revoke admin rights |
Toggle Default: On |
On - Admin privileges are removed for all users except those appearing in the Excluded accounts list.. Off - Admin privileges are not removed for users configured locally as administrators. |
|
Excluded accounts |
Text |
The account name(s) to retain local admin privileges. Multiple accounts must be specified on separate lines. Domain accounts must be prefixed with domain and backslash. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Run As Admin tab
Run As Admin tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Lockdown > RUN AS ADMIN
These settings control whether or not:
-
Users are able to run individual system files with elevated permissions
-
PIN Code unlock is available on endpoints
-
Browser toast notifications are enabled for downloaded files (requires version 8.6+ on endpoints)
|
Setting |
Type |
Description |
|---|---|---|
|
Deny elevating system files |
Toggle Default: Off |
On - Prevent the user from starting any file from the System32 directory with administrative privileges, such as cmd.exe or regedit.exe. Define exceptions under App Control > PRE-APPROVE. Off - Allow user to run system files with admin privileges. |
|
Deny system file subprocesses |
Toggle Default: Off |
On - Prevent spawning any sub-processes of system files. Requires endpoint client version 8.3+. Off - Do not prevent spawning of sub-processes. |
|
Deny PIN code unlock |
Toggle Default: Off |
On - Remove the option to use a PIN code to unlock a blocked application. Off - Allow access to the PIN Code unlock option. |
|
Disable browser notifications |
Toggle Default: Off |
On - The browser extension is removed and no pop-up notification appears after files are downloaded, meaning that running a downloaded file requires users to go the Downloads folder to execute. Requires endpoint client version 8.6+. Off - Toast notifications are enabled for Edge, Chrome and Firefox. This means that files downloaded in these browsers display a pop-up notification at the end of the download, allowing users to execute the downloaded file. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Browser extension registry values
The browser extension does not interact with any pages - its sole purpose is to register for download events. Unless disabled in the portal (Endpoint Privilege Management > Settings > Windows Settings > Lockdown > RUN AS ADMIN), it sets the following registry keys for the current user, which effectively installs the extension.
-
By default, keys are installed in HKCU. However, if other browser extensions are found installed via HKLM, the ABR keys are installed here instead as browsers won’t look in HKCU if a force list install exists under HKLM.
-
The ABR keys are not created if the CURRENT_USER is an administrator on the endpoint.
Edge
-
com.abr.startapp points to the Admin By Request native messaging manifest file for Edge.
-
ExtensionInstallForcelist creates a string value with the data set to the unique identifier of the extension.
Copy
Key: HKEY_CURRENT_USER\Software\Microsoft\Edge\NativeMessagingHosts\com.abr.startapp
Data: C:\ProgramData\FastTrack Software\Admin By Request\edge.json
Key: HKEY_CURRENT_USER\Software\Policies\Microsoft\Edge\ExtensionInstallForcelist
Data: epedcemobfdkplllcmmillfgcommghhi
Chrome
-
com.abr.startapp points to the Admin By Request native messaging manifest file for Chrome.
-
ExtensionInstallForcelist creates a string value with the data set to the unique identifier of the extension.
Copy
Key: HKEY_CURRENT_USER\Software\Google\Chrome\NativeMessagingHosts\com.abr.startapp
Data: C:\ProgramData\FastTrack Software\Admin By Request\chromium.json
Key: HKEY_CURRENT_USER\Software\Policies\Google\Chrome\ExtensionInstallForcelist
Data: plpgadlcmhefelnckjaaggemagdpoeen
Firefox
-
com.abr.startapp points to the Admin By Request native messaging manifest file for Firefox.
-
Under unique ID com.abr.startapp@adminbyrequest.com, we create the following keys:
-
install_url - points to the URL from where to fetch the extension
-
installation_mode - instructs the operating system on how to handle the extension. Can be either force_installed (for install) or blocked (for uninstall).
Copy
Key: HKEY_CURRENT_USER\Software\Mozilla\NativeMessagingHosts\com.abr.startapp
Data: C:\ProgramData\FastTrack Software\Admin By Request\firefox.json
Key: HKEY_CURRENT_USER\Software\Policies\Mozilla\Firefox\ExtensionSettings\com.abr.startapp@adminbyrequest.com
Data: install_url: https://addons.mozilla.org/firefox/downloads/latest/admin-by-request/latest.xpi
Data: installation_mode: force_installed or blocked -
Unique IDs Summary
-
Edge: epedcemobfdkplllcmmillfgcommghhi
-
Chrome: plpgadlcmhefelnckjaaggemagdpoeen
-
Firefox: com.abr.startapp@adminbyrequest.com
 Admin Session tab
Admin Session tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Lockdown > ADMIN SESSION
These settings control whether or not users are able to run key system files, such as cmd.exe or regedit.exe, during an Admin Session.
|
Setting |
Type |
Description |
|---|---|---|
|
Deny elevating system files |
Toggle Default: Off |
On - Prevent the user from starting any file from the System32 directory with administrative privileges, such as cmd.exe or regedit.exe. Define exceptions under App Control > PRE-APPROVE. Off - Allow user to run system files with admin privileges. |
|
Deny system file subprocesses |
Toggle Default: Off |
On - Prevent spawning any sub-processes of system files. Requires endpoint software version 8.3+. Off - Do not prevent spawning of sub-processes. |
|
Deny PIN code unlock |
Toggle Default: Off |
On - Remove the option to use a PIN Code to unlock an admin session or unlock a blocked application. If this option is Off and admin sessions are disabled, the system tray menu item to start an admin session will be removed. Off - Allow access to the PIN Code unlock option (unless Allow Admin Sessions is Off under Authorization > AUTHORIZATION). |
|
Force applications close at end |
Toggle Default: Off |
On - Forcibly close any application that runs UAC-elevated at the end of the admin session. This prevents users from keeping a permanently elevated process running as administrator. Note that long-running installations that run past the allowed admin time will also be forcibly closed. To avoid this, make sure the access time is sufficient to install software. Off - Do not force closure of applications that run UAC-elevated. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Support Assist tab
Support Assist tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Lockdown > SUPPORT ASSIST
This setting determines if Support Assist is enabled or not.
Support Assist is a feature whereby another user can remotely connect to assist the currently logged-on user with tasks requiring admin rights. The assisting user can be a Help Desk person, an IT Administrator, or simply a regular user who knows what to do and has the required privilege levels.
Section Requesting Assistance (Support Assist) provides an example of how Support Assist might be used.
Support Assist is initiated by invoking the About screen in the system tray and selecting the left menu button Assistance. The Auditlog will clearly show who is requesting assistance and who is providing it.
Support Assist can also be used to completely remove admin rights for end users that are unlikely to ever need them, thus ensuring the principle of least privilege. In the exceptional case that admin rights are needed, a supporting person can perform Support Assist on behalf of the end user to perform the task.
Leaving Support Assist ON is no more dangerous than turning it OFF, because any assisting user that connects remotely can always perform the same actions by logging on to the endpoint directly.
Support Assist lockdown settings require endpoint version 8.5 or newer.
|
Setting |
Type |
Description |
|---|---|---|
|
Allow Support Assist |
Toggle Default: On |
On - Support Assist is enabled. Off - Support Assist is disabled. |
|
Force applications close at end |
Toggle Default: On |
On - At the end of the Support Assist session, forcibly close any elevated processes that were started when the session started. This ensures that the end user does not have ongoing access to an elevated process. Off - Do not forcibly close other elevated processes when the session ends.. |
|
Force close time (minutes) |
Integer Default: 240 (minutes) |
The maximum duration in minutes a Support Assist session may last. This time must be sufficient for the assisting user to install software or perform any other tasks that require elevation. If still running, Support Assist will be forcibly closed after this time, to make sure a session is not unintentionally left on-going. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Owner tab
Owner tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Lockdown > OWNER
Upon installation of Admin By Request on an endpoint, the first non-administrator who logs in after a 24-hour stand-down period becomes the Device Owner. The stand-down period is to avoid an incorrect user being set as the Device Owner (such as an IT Admin assisting with setup post-installation).
After the 24-hour window, the Device Owner is set, although an administrator can change the Device Owner in the inventory.
Lock device to owner means that only the owner of the endpoint will be able to use Run As Admin or start an Admin Session.
|
Setting |
Type |
Description |
|---|---|---|
|
Lock device to owner |
Toggle Default: Off |
On - Set the owner of the endpoint to the first person logging-in after the 24-hour stand-down period. Once set, only the Device Owner will be able to use Run As Admin or start an Admin Session. Off - Device Owner will not be set regardless of who logs in. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
If you want to record device owners for endpoints, Collect inventory must be ON.
This is because there is no way to identify the device owner if no inventory data is collected. Therefore, if Collect inventory is OFF (portal menu Settings > Tenant Settings > Data > PRIVACY), setting Lock device to owner (portal menu Endpoint Privilege Management > Settings > [OS] Settings > Lockdown > OWNER) has no effect.
 Intune tab
Intune tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Lockdown > INTUNE
Device must be compliant means that the endpoint must comply with Intune requirements to be able to use Run as Admin or start an Admin Session.
You need to configure the Entra ID Connector for this feature to work.
|
Setting |
Type |
Description |
|---|---|---|
|
Device must be compliant |
Toggle Default: Off |
On - The endpoint must be Intune-compliant to use Run as Admin or start an Admin Session. Off - The endpoint is not required to be Intune-compliant. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Malware
 Detection tab
Detection tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Malware > DETECT
Admin By Request uses OPSWAT's MetaDefender for malware scanning. If a file is malicious, execution is blocked on the endpoint before it runs with administrative privileges.
When a user attempts to run a file with administrative privileges using the Run as Admin feature, the file is scanned on MetaDefender Cloud and, if flagged as malicious, the endpoint blocks the file and stops the process. An entry is added in the auditlog that the file was blocked, and which engines flagged it.
If unchecking Cloud scan unknown files but leaving Real-time detection on, only checksum look-up for the known 75% is performed and the rest must be handled by the local endpoint anti-virus product. If a file is flagged as malicious, the administrators decide what happens next, in the Action setting.
|
Setting |
Type |
Description |
|---|---|---|
|
Real-time detection |
Toggle Default: On |
On - When a user requests Run As Admin, the checksum of the file is evaluated. If the checksum is flagged, endpoint execution is blocked. Off - The file's checksum is not evaluated prior to execution. |
|
Cloud scan unknown files |
Toggle Default: On |
On - Unknown files will be uploaded to the OPSWAT cloud service for multi-engine malware scanning. Off - Unknown files will not be uploaded. |
|
Action |
Selection:
Default: |
IT Administrators have two options:
|
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Notification tab
Notification tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Malware > NOTIFICATION
Email notification to administrators is available when Require approval is checked under Authorization. This setting enables additional notifications to be sent when malware is detected.
Denied or quarantined requests will always appear under "Requests" or "Detected Malware" in the Settings menu, but this setting allows you to add a real-time email notification when the request occurs.
As well as malware, notifications can be sent for the following scenarios:
-
Each new request for approval via Run As Admin or Admin Session
-
When unattended remote access is requested (Unattended Access)
-
When either an end user or portal admin initiates a Remote Support session.
As with other request types, new requests always appear under Requests > Pending in the portal main menu. This is the case for both Endpoint Privilege Management and Secure Remote Access.
Phone notification is separate and happens automatically via push notifications to phones with the mobile app installed.
|
Setting |
Type |
Description |
|---|---|---|
|
Send email notifications |
Toggle Default: Off |
On - When malware is detected, additional email notifications are sent to the email addresses listed in Email addresses. Off - Email notifications are not sent. |
|
Email addresses |
Text |
Standard email address format. Use a new line for each address. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
App Control
 Pre-Approve tab
Pre-Approve tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > App Control > PRE-APPROVE
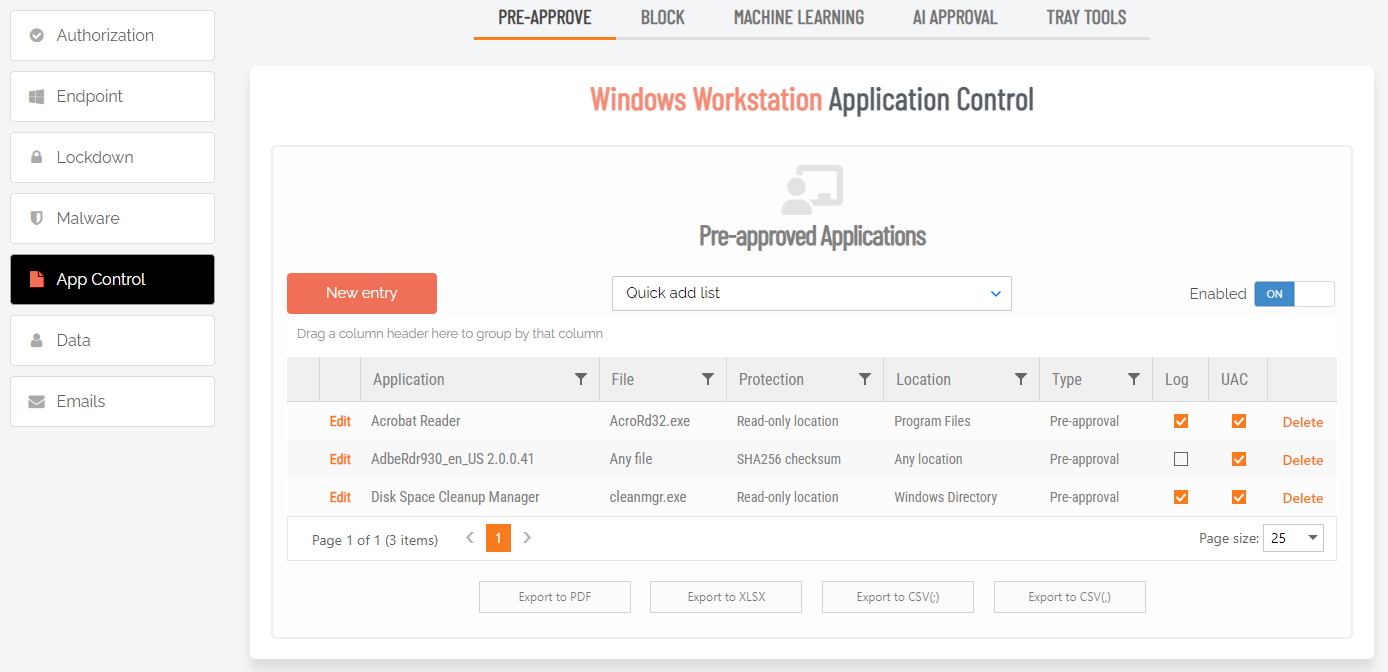
Pre-approval allows users to run some applications without approval, typically used to define exceptions when approval is required.
Pre-approved applications are
When an application is on the pre-aproval list, the difference is:
-
The application is auto-approved, so the approval flow is bypassed
-
A reason is not required
-
You have the option to not log to the Auditlog (e.g. for trivial data)
-
If Run As Admin is disabled, a pre-approved application will still run
-
A pre-approved application will overrule Deny elevating system files
-
You can force applications to always run elevated (legacy applications)
Enabled toggle
A global setting that indicates whether pre-approved applications are allowed at all (On) or not at all (Off).
New entry (APPLICATION tab)
Click button New entry to create a new pre-approved application.
|
Setting |
Type |
Description |
|---|---|---|
|
Type |
Selection Default: Run As Admin application pre-approval |
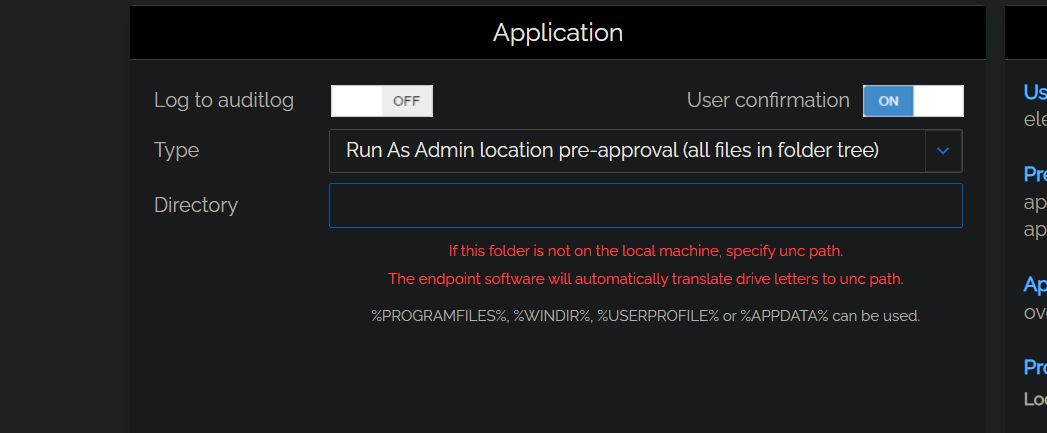
Run As Admin application pre-approval - Pre-approve this application for Run As Admin. Run As Admin vendor pre-approval (digital certificate) - Pre-approve all applications based on the specifiedVendor digital certificate. Selecting this option enables the Vendor field and hides all other fields. Run As Admin location pre-approval (all files in folder tree) - Pre-approve all applications in the specified folder, including any sub-folders. Selecting this option enables the Directory field and hides all other fields. Force running application elevated (legacy application) - Pre-approve this application to run elevated regardless of any other conditions. |
|
Vendor (enabled when Run As Admin vendor pre-approval |
Read-only selection (via Button) |
Use the Browse button to select a valid Vendor certificate file. |
|
Protection |
Selection Default: File must be located in read-only directory |
Prevent users from bypassing pre-approval by file renaming. File must be located in read-only directory - The recommended method. File must be in a read-only location. You only need to know the name and location and you are not bound to a specific file version. File must match digital certificate and application name - Vendor digital certificate of a file AND the exact name of the application. File must match digital certificate and file name - Vendor digital certificate of a file AND the exact name of the file. Recommended if you have a copy of the file. File must match checksum - A checksum of a specific file version. If the file is updated, the checksum no longer matches and a new one must be collected. No protection (not recommended) - Not recommended for anything except testing. The file can be located anywhere and is a file renaming vulnerability, in case a user is aware of (or can guess) the file name. |
|
File location |
Selection Default: Program Files or subfolder |
Program Files or subfolder - The Program Files folder, typically either C:\Program Files or C:\Program Files (x86). Windows directory or subfolder - The Windows system folder, typically C:\Windows\System32. Custom read-only location - Shows an additional field labeled Directory if selected. |
|
Directory (enabled when other selections are in effect):
|
Text |
A read-only location where the application to be added is stored. Can include the following environment variables:
If the directory entered is not on the local machine, a UNC path can be used. The endpoint software will automatically translate drive letters to UNC path. |
|
Application name |
Text |
The name of the application. Mandatory, although used for convenience only to help identify applications in the list. |
|
File name |
|
Use the Browse button to open an operating system File open dialog box. Locate and select a file with one of the following extensions:
Note that adding the app via the Auditlog will auto-populate this field. |
|
Internal comments (optional) |
Text |
Notes about this pre-approval. |
|
Version (optional) |
Text (Min. version) Text (Max. version) |
Version works as starting with, meaning Min. version can be specified as 14, 14.1 or full 14.1.34.4555. Max. version is less than, meaning that 15 means less than 15.0.0.0.. |
|
Parameters (optional) |
Text |
Parameters entered on the command line after the application name. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
|
Cancel |
Button |
Cancels all work done in this setting and returns to the |
New entry (ADVANCED tab)
Additional toggle settings that apply to the pre-approval entry being created.
|
Setting |
Type |
Description |
|---|---|---|
|
User confirmation |
Toggle Default: On |
On - The user must confirm elevation on the endpoint before the application can be run. This is the typical Off - The user does not need to confirm elevation on the endpoint before execution. Hides the Log to auditlog field. |
|
Log to auditlog (hidden if User confirmation is Off) |
Toggle Default: On |
On - Relevant details about the application are logged. Off - No logging is performed for this application. |
|
Block subprocesses |
Toggle Default: Off |
On - Any subprocesses spawned by this application that require elevated privileges will not be pre-approved for execution. Off - Subprocesses spawned by this application that require elevated privileges will be allowed to execute. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
|
Cancel |
Button |
Cancels all work done in this setting and returns to the |
Quick add list
The Quick add list is a preset list of common applications. It is a selection list, accessed by clicking the drop-down arrow at the right of the field.
If all entries in the Quick add list have already been added and are visible in the list of applications, the Quick add list field does not appear at all.
Export buttons
Four export buttons are also provided:
-
Export to PDF
-
Export to XLSX
-
Export to CSV (;)
-
Export to CSV (,)
These buttons export all entries in the list.
 Block tab
Block tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > App Control > BLOCK
Blocked applications are effectively the opposite of pre-approved applications - the feature allows you to point to a file name that will be blocked from executing rather than pre-approved for execution. Wildcards can be specified in the file name, such as *.msi.
As with other activity, attempts to run blocked applications are recorded in the auditlog.
Please contact us using the Contact menu, if you have questions about blocking.
Enabled toggle
A global setting that indicates whether blocked applications are allowed at all (On) or not (Off).
New entry
Click button New entry to add a blocked application.
|
Setting |
Type |
Description |
|---|---|---|
|
Type |
Selection Default: Block file from running as administrator |
Block file from running as administrator - Block this application for Run As Admin. Block vendor files from running as admin (digital certificate) - Block all applications based on the specifiedVendor digital certificate. Selecting this option enables the Vendor field and hides all other fields. Block location from running as admin (all files in folder tree) - Block all applications in the specified folder, including any sub-folders. Selecting this option enables the Directory field and hides all fields except the optional fields. Block always - Block this application regardless of any other conditions. |
|
Condition |
Selection Default: No condition (block always) |
Condition applies only when a file is blocked. No condition (block always) - The default (and recommended) method. Block if located in directory - File must be located in this folder or directory to be blocked. File must match digital certificate - Vendor digital certificate of a file. Recommended if you have a copy of the file. Block if matching checksum - A checksum of a specific file version. If the file is updated, the checksum no longer matches and a new one must be collected. |
|
File location (enabled when other selections are in effect):
|
Selection Default: Program Files or subfolder |
Program Files or subfolder - The Program Files folder, typically either C:\Program Files or C:\Program Files (x86). Windows directory or subfolder - The Windows system folder, typically C:\Windows\System32. In user profile - A folder that appears in the user's profile. Custom location - Shows an additional field labeled Directory if selected. |
|
Directory (enabled when other selections are in effect):
|
Text |
File must be located in this directory or a sub-folder. A read-only location where the application is stored. Can include the following environment variables:
If the directory entered is not on the local machine, a UNC path can be used. The endpoint software will automatically translate drive letters to UNC path. |
|
Application name |
Text |
The name of the application. Mandatory, although used for convenience only to help identify applications in the list. |
|
File name |
|
Use the Browse button to open an operating system File open dialog box. Locate and select a file with one of the following extensions:
Note that blocking the app via the Auditlog will auto-populate this field. |
|
SHA256 checksum (enabled when other selections are in effect):
|
Text |
A checksum of a specific file version. |
|
Blocking message (optional) |
Text |
A message that appears as a rejection to the user, when the application is attempted to be executed. |
|
Internal comments (optional) |
Text |
Optional comments that IT admins might wish to add about the blocked application. |
|
Version (optional) |
Text (Min. version) Text (Max. version) |
Version works as starting with, meaning Min. version can be specified as 14, 14.1 or full 14.1.34.4555. Max. version is less than, meaning that 15 means less than 15.0.0.0.. |
|
Parameters (optional) |
Text |
Parameters entered on the command line after the application name. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
|
Cancel |
Button |
Cancels all work done in this setting and returns to the |
Export buttons
Four export buttons are also provided:
-
Export to PDF
-
Export to XLSX
-
Export to CSV (;)
-
Export to CSV (,)
These buttons export all entries in the list.
 Machine Learning tab
Machine Learning tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > App Control > MACHINE LEARNING
Machine Learning auto-approval can automatically approve trivial Run As Admin requests for applications you have previously approved manually.
Approvals is the number of times an application must be manually approved in order to be auto-approved in the future. You can check report Reports > Settings Reports > Machine Learning for the current counts in your tenant of manual approvals (Count column), as well as App and Vendor scores for AI auto-approval.
For example, if Approvals is 2 and the first and second users get manual approval to run application X, it will be auto-approved for all future requests. This way, you can avoid building a pre-approvals list ahead of time and simply build a list by approving requests as they come in.
|
Setting |
Type |
Description |
|---|---|---|
|
Enabled |
Toggle Default: On |
On - Machine learning auto-approval is enabled. A Run As Admin request will be automatically approved for apps that have been previously approved, provided the required number of Approvals has been met. Off - Machine learning auto-approval is not enabled. |
|
Approvals |
Sliding scale Default: 0 |
A "click and drag" scale that can take any value from 0 to 10. The required number of times an application must be manually approved in order to be auto-approved in the future. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 AI Approval tab
AI Approval tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > App Control > AI APPROVAL
AI Approval allows our AI scoring system to auto-approve trivial Run As Admin requests for common applications.
At the time of writing, our app database comprises more than 12 million known applications. Each of these is scored by our AI engine in real-time based on popularity, reputation and trends. If, for example, the App score is enabled at 20, it means that any request is auto-approved if the App score is 20 or above.
There is a sample list in the portal to help you get a rough understanding of which threshold you could be comfortable with. You can also expand lines in your Auditlog to see the scores for your own elevations.
Note that there are two scores - AI App Auto-Approval and AI Vendor Auto-Approval. If both are enabled and an app exists in the database that has a score higher than either of the two values set here, it will automatically be approved when users request elevated access.
AI App Auto-Approval
|
Setting |
Type |
Description |
|---|---|---|
|
Enabled |
Toggle Default: Off |
On - AI auto-approval for applications is enabled. An app will be automatically approved if it's score is higher than the value set for App score. Off - AI auto-approval for apps is not enabled. |
|
App score |
Sliding scale Default: 10 |
A "click and drag" scale that can take any value from 0 to 100. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
AI Vendor Auto-Approval
|
Setting |
Type |
Description |
|---|---|---|
|
Enabled |
Toggle Default: Off |
On - AI auto-approval for vendors is enabled. An app will be automatically approved if it's score is higher than the value set for Vendor score. Off - AI auto-approval for vendors is not enabled. |
|
Vendor score |
Sliding scale Default: 10 |
A "click and drag" scale that can take any value from 0 to 100. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Both App and Vendor auto-approval can be overruled by sub-settings for users matching the sub-setting criteria.
 Tray Tools tab
Tray Tools tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > App Control > TRAY TOOLS
Tray Tools are items that appear when users click the Admin By Request system tray icon. As well as executable files, these tools could be web links with instructions, Control Panel applets or program shortcuts.
Minimum requirements
Tray Tools require Admin By Request version 7.1 or newer. Control Panel tools require Windows 10 version 2004 (build 19041) or newer.
New Tray Tool
Click button New Tray Tool to create a new entry in the tray tools menu.
|
Setting |
Type |
Description |
|---|---|---|
|
Application |
Text |
The caption used for the system tray menu item. Enter the text to be used for the name or caption. Does not have to match the executable File name. Note that any webhooks you have created appear in a selection list when you click this field. The list is for convenience only and simply "pastes" the webhook caption into the field - no other fields are populated. |
|
File |
Text |
The name of the executable file, including it's full path. You can also specify a web address (i.e. URL) in this field, in which case the Run As Admin toggle should be Off for security reasons. |
|
Parameters |
Text |
Text values entered here are appended to the File as parameters during execution. |
|
Run As Admin |
Toggle Default: On |
On - Allows the executable file named in File to be Run As Admin (i.e. run as an administrator). Off - Does not allow the executable file named in File to be Run As Admin. This should be the option selected if the entry in File is a web address. |
|
Pre-approve |
Toggle Default: Off |
On - Pre-approves the file specified for elevated execution, by-passing normal approval flow. Off - Approval flow is not by-passed for this file. If approval is required, users must still submit a request to run even though the file is added as a tray tool item. |
|
Menu Separator |
Toggle Default: Off |
On - Inserts a line above this menu item. Allows tray tool menu items to be grouped. Off - No line is inserted. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
|
Cancel |
Button |
Cancels all work done in this setting and returns to the |
Quick add list
The Quick add list is a preset list of common Control Panel applets. It is a selection list, accessed by clicking the drop-down arrow at the right of the field. You can add other Control Panel applets by creating a tool that runs control.exe followed by a .cpl file.
If all entries in the Quick add list have already been added as tray tools, the Quick add list field does not appear at all.
Data
 Privacy tab
Privacy tab
Privacy has been moved to Settings > Tenant Settings > Data > PRIVACY in the Portal. Refer to Tenant Settings for more information.
Emails
 Request Emails tab
Request Emails tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Emails > REQUEST EMAILS
Emails go out when Require approval is turned On under Authorization. You can create your own email templates here with information specific to your company, such as a Help Desk phone number and custom instructions.
|
Setting |
Type |
Description |
|---|---|---|
|
Email template |
Selection Default: Run As Admin: Approved email |
Run As Admin | Admin Session: Approved email - Loads a template that advises the user (i.e. requester) that the request for access has been approved. Run As Admin | Admin Session: Denied email - Loads a template that advises the request for access has been denied without giving a reason. Run As Admin | Admin Session: Denied with reason - Loads a template that advises the request for access has been denied and provides the reason. Admin notify: New request - Loads a template that advises the administrator (i.e. person who approves or denies) that a request for access is waiting for attention. Admin notify: Malware detected - Loads a template that advises the administrator that malware has been detected, including a link to the Auditlog. |
|
Email sender |
Text Default: Admin By Request Team |
The email address to be used as the sender for the email. Can be used with custom domains. Use the Email address button to set up custom domains. Refer to Email Domain for more information on configuring an email address to be used as the sender for all user notifications. |
|
Email subject |
Text Default: Admin By Request |
Text that will appear in the subject line of emails. |
|
Get default |
Button |
Loads the default Email template for the option selected. NOTE:
|
|
Email address |
Button |
Switches to Email Domain in Tenant Settings in the portal, allowing you to use a custom domain as the sender. This allows sending email from domains other than @adminbyrequest.com. NOTE: This is optional, but you cannot add an email sender field of e.g. "tom@mydomain.com" unless you have first set up the custom email domain "mydomain.com" via the Email Domain setting in the portal (Settings > Tenant Settings > Email Domain). |
|
Template body |
Formatted text |
The body of the email to be sent. Includes three views:
Dynamic content tagsTags can be used in the body, which are place holders in curly braces. These are replaced with actual request values when emails are sent. The following tags are available:
|
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
 Ticketing System tab
Ticketing System tab
Portal menu: Endpoint Privilege Management > Settings > Windows Settings > Emails > TICKETING SYSTEM
You can set up an email notification to your ticketing system and embed the tags below for dynamic content.
|
Setting |
Type |
Description |
|---|---|---|
|
Ticket system email |
Text |
The email address to which emails intended for your ticket system will be sent. For example: itsupport@mycompany.com |
|
Email sender |
Text Default: Admin By Request Team {ID} |
The email address to be used as the sender for the email. Can be used with custom domains. Use the Email address button to set up custom domains. |
|
Email subject |
Text Default: Admin By Request |
Text that will appear in the subject line of emails. |
|
Get default |
Button |
Loads the default Email template for the option selected. NOTE:
|
|
Email address |
Button |
Switches to Email Domain in Tenant Settings in the portal, allowing you to use a custom domain as the sender. This allows sending email from domains other than @adminbyrequest.com. NOTE: This is optional, but you cannot add an email sender field of e.g. "tom@mydomain.com" unless you have first set up the custom email domain "mydomain.com" via the Email Domain setting in the portal (Settings > Tenant Settings > Email Domain). |
|
Template body |
Formatted text |
The body of the email to be sent to the ticketing system. Includes three views:
Dynamic content tagsTags can be used in the body, which are place holders in curly braces. These are replaced with actual request values when emails are sent. The following tags are available:
Ticket IDYou can find a ticket by its ticket ID using the Search button in the Auditlog. Voided textIf a line has one or more tags and all tags in the line are empty, the entire line is automatically removed. |
Run As Admin notification events
|
Setting |
Type |
Description |
|---|---|---|
|
User requests Run As Admin approval |
Toggle Default: On |
On - Sends a notification for User requests Run As Admin approval. Off - Does not send a notification. |
|
Admin approves Run As Admin request |
Toggle Default: Off |
On - Sends a notification for Admin approves Run As Admin request. Off - Does not send a notification. |
|
Admin denies Run As Admin request |
Toggle Default: Off |
On - Sends a notification for Admin denies Run As Admin request. Off - Does not send a notification. |
|
User starts Run As Admin |
Toggle Default: Off |
On - Sends a notification for User starts Run As Admin. Off - Does not send a notification. |
|
User finishes Run As Admin |
Toggle Default: Off |
On - Sends a notification for User finishes Run As Admin Off - Does not send a notification. |
Admin Session notification events
|
Setting |
Type |
Description |
|---|---|---|
|
User requests Admin Session approval |
Toggle Default: On |
On - Sends a notification for User requests Admin Session approval. Off - Does not send a notification. |
|
Admin approves Admin Session request |
Toggle Default: Off |
On - Sends a notification for Admin approves Admin Session request. Off - Does not send a notification. |
|
Admin denies Admin Session request |
Toggle Default: Off |
On - Sends a notification for Admin denies Admin Session request. Off - Does not send a notification. |
|
User starts Admin Session |
Toggle Default: Off |
On - Sends a notification for User starts Admin Session. Off - Does not send a notification. |
|
User finishes Admin Session |
Toggle Default: Off |
On - Sends a notification for User finishes Admin Session Off - Does not send a notification. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |