Active Directory
Introduction
This section provides information regarding Admin By Request's integration with Active Directory. For an overview of integration functionality, including descriptions of other integrations, please refer to the Integration Hub.
The Local Administrator’s Group
Upon installation in domain environments, the Domain Users group is immediately removed from the local administrator’s group. Subsequently, when a user logs in, they are removed from the local administrator’s group unless one of the following conditions is met:
-
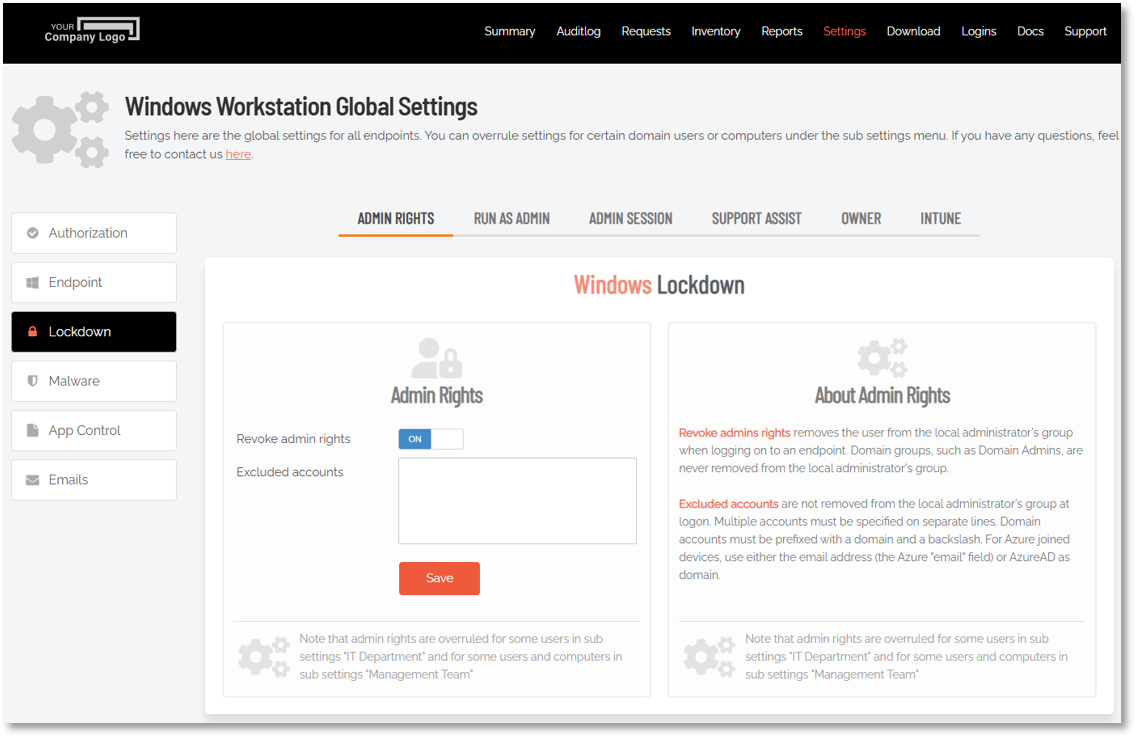
The “Revoke admins rights” option is unchecked in the portal settings.
-
The user is listed in the "Excluded accounts" list in the portal settings.
-
The user belongs to a group that is part of the local administrator’s group (e.g., Domain Admins).
This selective removal ensures that only interactive user accounts are affected, preventing the inadvertent removal of service accounts used for software deployment.
The portal settings that apply to local admin rights for Windows endpoints are found in the portal at Endpoint Privilege Management > Settings > Windows Settings > Lockdown > ADMIN RIGHTS:
Domain groups (excluding Domain Users) are not removed from the local administrator’s group. Consequently, if a user is part of a domain group included in the local administrator’s group (e.g., a Help Desk domain group), they retain local administrator rights. In such cases, the tray icon turns red, and hovering over it displays a tool tip stating “You are logged on as administrator.”
Azure AD and Computers Outside Domains
The software operates identically on non-domain computers and those joined to Azure AD. For Azure AD integration, a connector can be set up in the portal settings. This setup is necessary only if sub-settings based on Azure AD groups are required.
Preventing Abuse
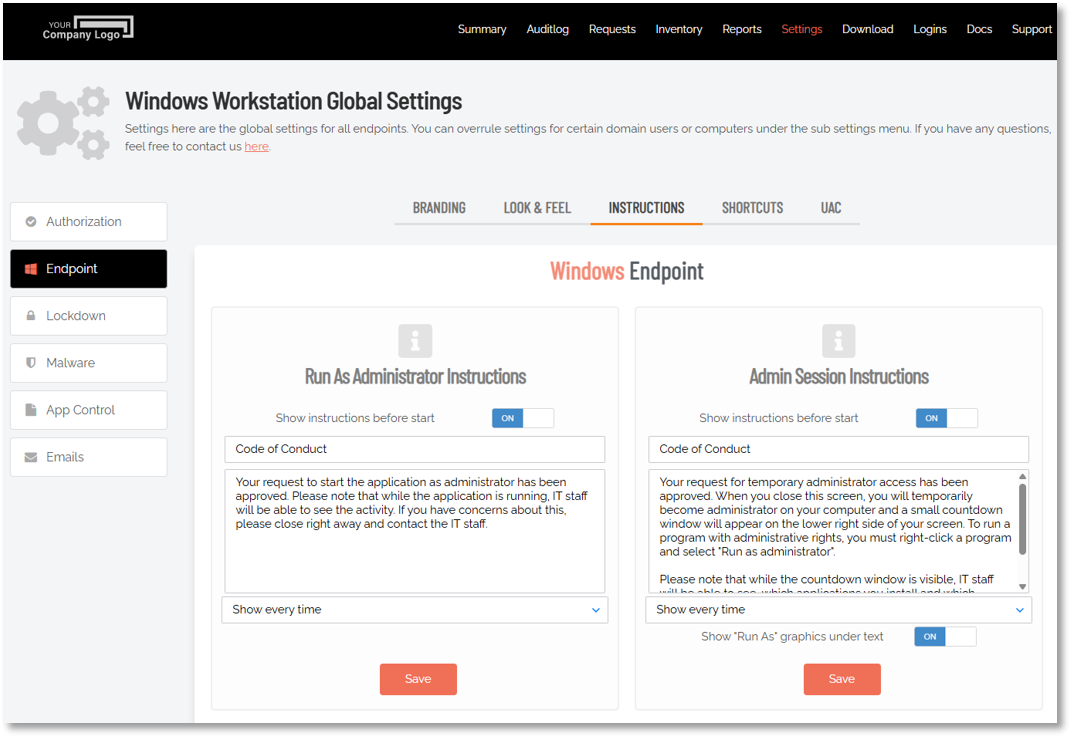
To mitigate the risk of abuse during an Admin Session, users must request access from IT. Additionally, a customizable Code of Conduct page can be configured, outlining company policies and potential penalties for misuse. This page is displayed before the administrative session begins, reinforcing the message with the company name and logo.
The portal settings that apply to Code of Conduct for Windows endpoints are found in the portal at Endpoint Privilege Management > Settings > Windows Settings > Endpoint > INSTRUCTIONS:
Offline Computers
Admin By Request maintains functionality regardless of the computer’s online status. Portal settings, domain groups, and OUs are cached on the client, and any outbound data is queued. This ensures a consistent user experience even when the computer is offline.
PIN Code
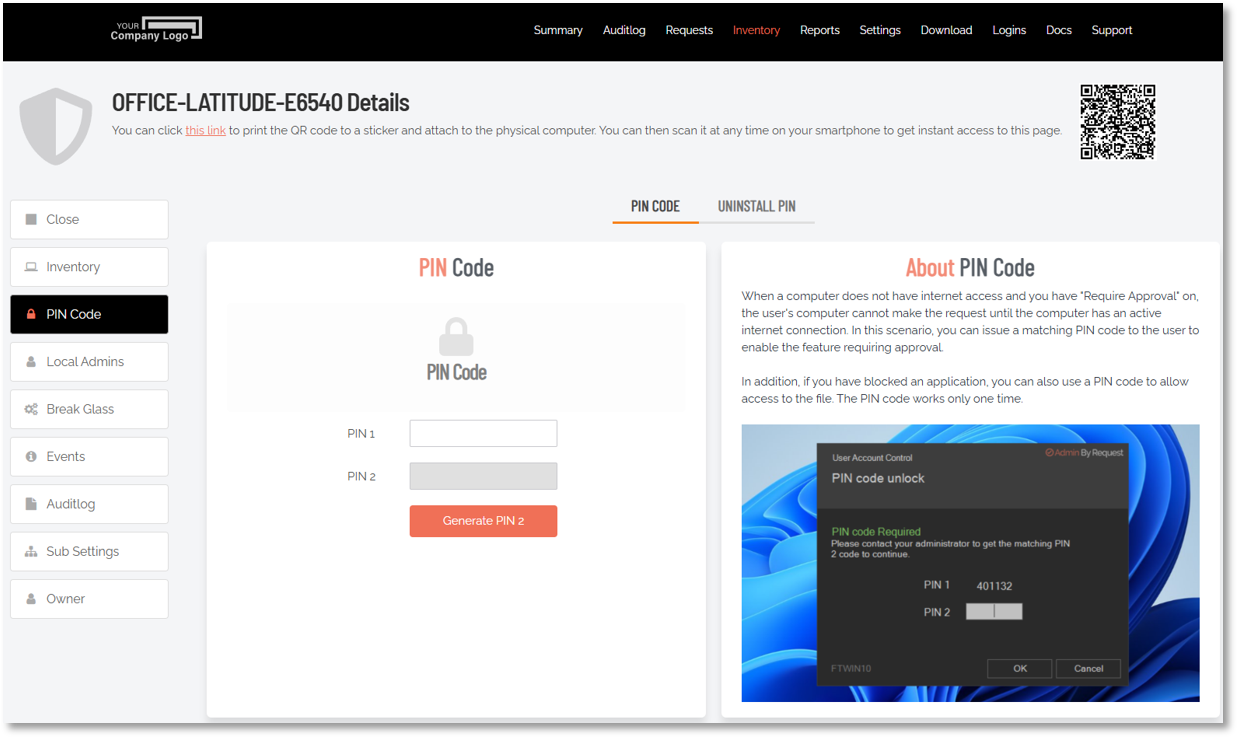
The software operates the same way online and offline, with the exception of approval requirements when the computer is offline. In such scenarios, pending requests are queued until an internet connection is available. For urgent cases where internet access is impossible, users can request a one-time PIN code. This involves the user generating a “PIN 1” code and contacting the Help Desk to receive the corresponding “PIN 2” code, which is uniquely hashed from PIN 1, customer ID, and computer name.
The portal settings that apply to PIN Code for a Windows computer are found in the portal at Inventory > [Computer] > PIN Code > PIN CODE:
Tampering Prevention
To prevent users from gaining permanent administrative rights, the software removes user and group administration from Computer Management during an admin session. Any changes to the local administrator’s group are "snapshot" before the session and restored afterward. Attempts to uninstall Admin By Request or tamper with policy keys during a session will result in error messages or automatic restoration post-session.
User Account Control
User Account Control (UAC) remains enforced, providing an additional security layer. Users must still use “Run as administrator” and enter their credentials to run applications during an Admin Session. Admin By Request does not replace or interfere with UAC, as altering system files or components can lead to issues, especially with Windows Updates. The software leverages existing Windows functionality without replacing system components, ensuring stability and resource efficiency.
As a rule, Admin By Request users who are administrators (i.e., red icon) typically do not receive ABR-style pop-ups when executing tasks that require elevated privileges. This is because the ABR client does not interfere if the logged-on user is an administrator - it simply defers to the Windows UAC pop-up. However, Admin By Request will still log everything that is done with elevated privileges.
Application Blocking
Admin By Request allows blocking of specific applications (e.g., Spotify, certain browsers) and prevents elevation of Windows system files (e.g., cmd.exe, regedit.exe, mmc.exe) as administrator.
Sub-settings
In the portal, default settings exist for Workstations and Servers. These can be overridden based on computer or user groups and Organizational Units (OUs). A common configuration might require approval for all users except those in the IT department, who can elevate without permission.
Proxy Servers
Admin By Request transparently supports proxy servers. The endpoint executable (AdminByRequest.exe) detects proxy settings for IP addresses used by the cloud service. This proxy information is passed to the underlying service, which uses the proxy for cloud communications without requiring user credentials. Proxy usage can be verified via the Admin By Request user interface, button About -> Connectivity.
For more information
Refer to Tenant Settings > Identity > Entra ID tab for more information about integrating your Active Directory or Entra ID environment with Admin By Request.