Windows Browser Extension
Overview
Admin By Request (ABR) for Windows Version 8.6 introduced a new Browser Extension designed to streamline the elevation process for downloaded installers.
When a non-administrator downloads an executable from Chrome, Edge, or Firefox, the extension triggers a system tray toast notification, allowing the file to be elevated and run directly - without navigating to the Downloads folder.
This feature is enabled by default upon installing Version 8.6 and installs a lightweight browser extension that does not collect data or interfere with other extensions; it simply subscribes to browser file download events.
From release 8.6.3, the registry is checked to see where ABR registry keys should be installed: HKLM or HKCU (the default).
Refer to Registry Keys for more information.
This technical note is available in PDF format:
About the Browser Extension
A few FAQs about this extension:
-
What does the browser extension do?
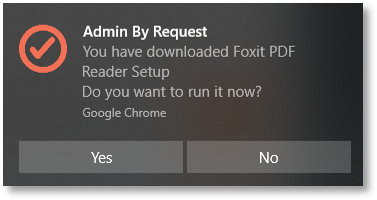
Basically, the browser extension listens for the “download finished” event in the browser. Once the event triggers, it uses Native Messaging to communicate with the ABR client and shows a toast notification with info about the downloaded file:
Once the user clicks the notification, the extension once again uses Native Messaging to communicate with the ABR client – telling it to trigger the flow just as if the user had opened the file via Explorer.
-
Which browsers are supported?
The extension is built for Chrome and Chromium-based browsers and Firefox:
-
For Google Chrome, the extension is fetched from the Chrome Web Store.
-
For Mozilla Firefox, the extension is fetched from the Firefox browser add-ons site.
-
For Microsoft Edge, the extension is fetched from the Edge add-ons site
-
-
How is the extension installed?
The extension is installed and configured via registry keys specific to the individual browser. This ensures that the user does not need to do anything to use the functionality of the extension.
Refer also to Registry Keys.
Portal Setting
We recommend leaving the Browser Extension feature enabled to improve the user experience. However, if you do not wish to use the browser extension, you can remove it by disabling the browser notification setting in the portal at menu:
Endpoint Privilege Management > Settings > Windows Settings > Lockdown > RUN AS ADMIN
These settings control whether or not:
-
Users are able to run individual system files with elevated permissions
-
PIN Code unlock is available on endpoints
-
Browser toast notifications are enabled for downloaded files (requires version 8.6+ on endpoints)
|
Setting |
Type |
Description |
|---|---|---|
|
Deny elevating system files |
Toggle Default: Off |
On - Prevent the user from starting any file from the System32 directory with administrative privileges, such as cmd.exe or regedit.exe. Define exceptions under App Control > PRE-APPROVE. Off - Allow user to run system files with admin privileges. |
|
Deny system file subprocesses |
Toggle Default: Off |
On - Prevent spawning any sub-processes of system files. Requires endpoint client version 8.3+. Off - Do not prevent spawning of sub-processes. |
|
Deny PIN code unlock |
Toggle Default: Off |
On - Remove the option to use a PIN code to unlock a blocked application. Off - Allow access to the PIN Code unlock option. |
|
Disable browser notifications |
Toggle Default: Off |
On - The browser extension is removed and no pop-up notification appears after files are downloaded, meaning that running a downloaded file requires users to go the Downloads folder to execute. Requires endpoint client version 8.6+. Off - Toast notifications are enabled for Edge, Chrome and Firefox. This means that files downloaded in these browsers display a pop-up notification at the end of the download, allowing users to execute the downloaded file. |
|
Save |
Button |
Saves customization and changes to any fields. Note that reloading any defaults does not take effect until Save is clicked. |
Registry Keys
The browser extension does not interact with any pages - its sole purpose is to register for download events. Unless disabled in the portal (Endpoint Privilege Management > Settings > Windows Settings > Lockdown > RUN AS ADMIN), it sets the following registry keys for the current user, which effectively installs the extension.
-
By default, keys are installed in HKCU. However, if other browser extensions are found installed via HKLM, the ABR keys are installed here instead as browsers won’t look in HKCU if a force list install exists under HKLM.
-
The ABR keys are not created if the CURRENT_USER is an administrator on the endpoint.
Edge
-
com.abr.startapp points to the Admin By Request native messaging manifest file for Edge.
-
ExtensionInstallForcelist creates a string value with the data set to the unique identifier of the extension.
Copy
Key: HKEY_CURRENT_USER\Software\Microsoft\Edge\NativeMessagingHosts\com.abr.startapp
Data: C:\ProgramData\FastTrack Software\Admin By Request\edge.json
Key: HKEY_CURRENT_USER\Software\Policies\Microsoft\Edge\ExtensionInstallForcelist
Data: epedcemobfdkplllcmmillfgcommghhi
Chrome
-
com.abr.startapp points to the Admin By Request native messaging manifest file for Chrome.
-
ExtensionInstallForcelist creates a string value with the data set to the unique identifier of the extension.
Copy
Key: HKEY_CURRENT_USER\Software\Google\Chrome\NativeMessagingHosts\com.abr.startapp
Data: C:\ProgramData\FastTrack Software\Admin By Request\chromium.json
Key: HKEY_CURRENT_USER\Software\Policies\Google\Chrome\ExtensionInstallForcelist
Data: plpgadlcmhefelnckjaaggemagdpoeen
Firefox
-
com.abr.startapp points to the Admin By Request native messaging manifest file for Firefox.
-
Under unique ID com.abr.startapp@adminbyrequest.com, we create the following keys:
-
install_url - points to the URL from where to fetch the extension
-
installation_mode - instructs the operating system on how to handle the extension. Can be either force_installed (for install) or blocked (for uninstall).
Copy
Key: HKEY_CURRENT_USER\Software\Mozilla\NativeMessagingHosts\com.abr.startapp
Data: C:\ProgramData\FastTrack Software\Admin By Request\firefox.json
Key: HKEY_CURRENT_USER\Software\Policies\Mozilla\Firefox\ExtensionSettings\com.abr.startapp@adminbyrequest.com
Data: install_url: https://addons.mozilla.org/firefox/downloads/latest/admin-by-request/latest.xpi
Data: installation_mode: force_installed or blocked -
Unique IDs Summary
-
Edge: epedcemobfdkplllcmmillfgcommghhi
-
Chrome: plpgadlcmhefelnckjaaggemagdpoeen
-
Firefox: com.abr.startapp@adminbyrequest.com