Single Sign-on Setup
Introduction
If your company uses Microsoft Active Directory (on-prem), or Entra ID (cloud-based), or any other identity provider (IdP), whether on-prem or cloud-based, you can enhance security and make life easier for yourself and your portal users with our single sign-on (SSO) support. We support all common identity providers either directly or through generic SAML 2.0.
When you add a portal user and assign them a single sign-on option, there is no password to worry about – and if your identify provider supports IdP-initiated login, they will not even need to know their username.
We currently support:
-
Microsoft 365 / Entra ID (formerly Azure AD)
-
Active Directory Federation Services (AD FS)
-
Okta
-
SAML 2.0 (any other identity provider using our generic SAML integration)
The procedures in this section work well for a small number of users entered manually. If you need to assign a large number of users using SCIM, refer to SCIM.
Microsoft 365 / Entra ID
Microsoft 365 supports integration with your in-house Active Directory, enabling users to access Microsoft 365 services using their standard AD login credentials. This connection is established through SAML authentication.
To add a Microsoft 365 login, you simply pick it as the sign-on method in the portal when adding a new user without any further configuration. The portal menu option to add a new user is Logins > User Logins.
Microsoft 365 login requires that users are allowed to consent to apps. You can enable this under Users and groups / User settings in the Azure Active Directory (Entra ID) Admin Center. Once all portal users have logged into the portal, the option to consent to apps can be disabled without affecting future logins.
Refer to Entra ID Support for more information.
Entra ID without Microsoft 365
It is possible to login using Entra ID without using Office 365.
Prerequisites
-
A user account in the ABR portal, with sufficient rights to configure SSO:
-
Read-only view: OFF
-
Manage Settings: ON
-
Manage portal users: ON
-
-
A valid account for the Entra ID portal as well as the ABR portal. Make sure you are logged-in to both portals - you will switch between them during the configuration procedure.
-
All your users who intend to login using Entra ID SSO must have their accounts and/or email addresses entered into your Entra ID portal. This makes them available to be assigned to the Admin By Request app once it is configured.
Procedure
The tasks below are labeled the same as the sections in the ABR portal. Each task comprises a number of steps.
-
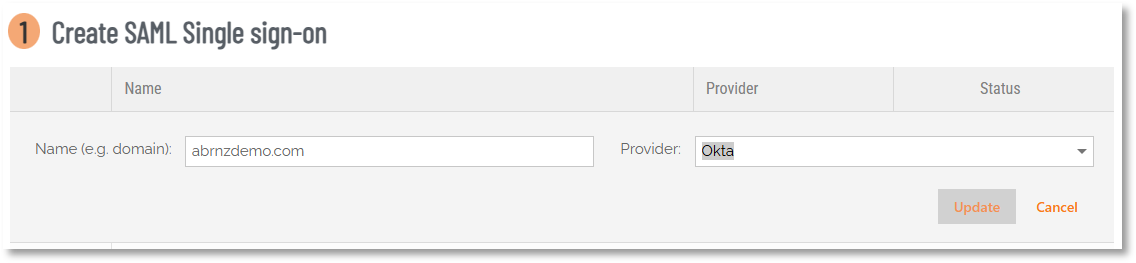
In the ABR portal, go to Logins > Single Sign-on Setup.
-
Click New entry.
-
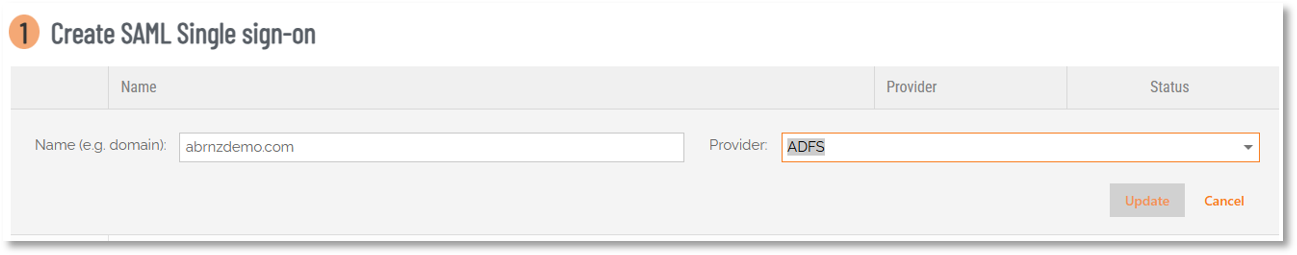
In field Name (e.g. domain):, enter the domain you want to use (usually your Active Directory or company domain name), select ADFS as Provider: and click Update:
The entry will be created and Status will be "Waiting for IDP metadata". Move to your ADFS server - we'll come back to the ABR portal later.
-
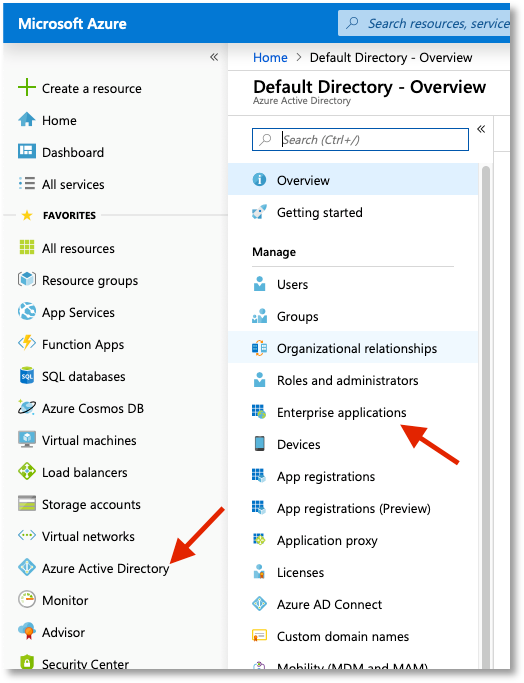
In the Microsoft Azure Portal go to Azure Active Directory / Enterprise Applications:
-
Select New Application (Non-gallery application) and enter Admin By Request as the name.
-
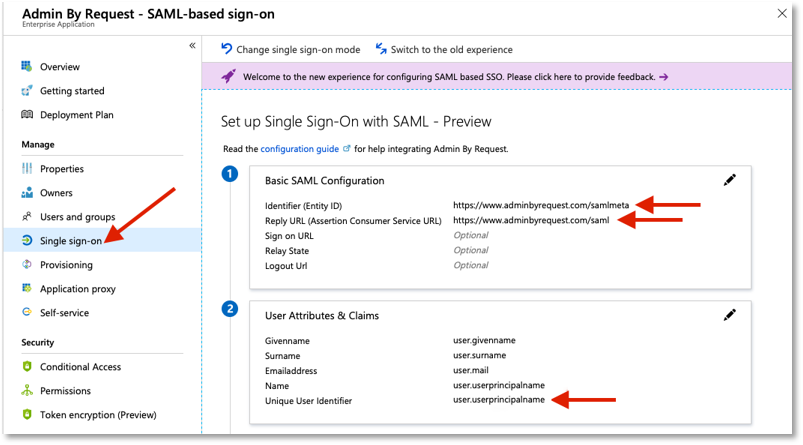
Go to Single sign-on and select SAML. Enter the following values under Basic SAML Configuration:
-
Identifier (Entity ID): https://www.adminbyrequest.com/samlmeta
-
Reply URL (Assertion Consumer Service URL): https://www.adminbyrequest.com/saml
-
-
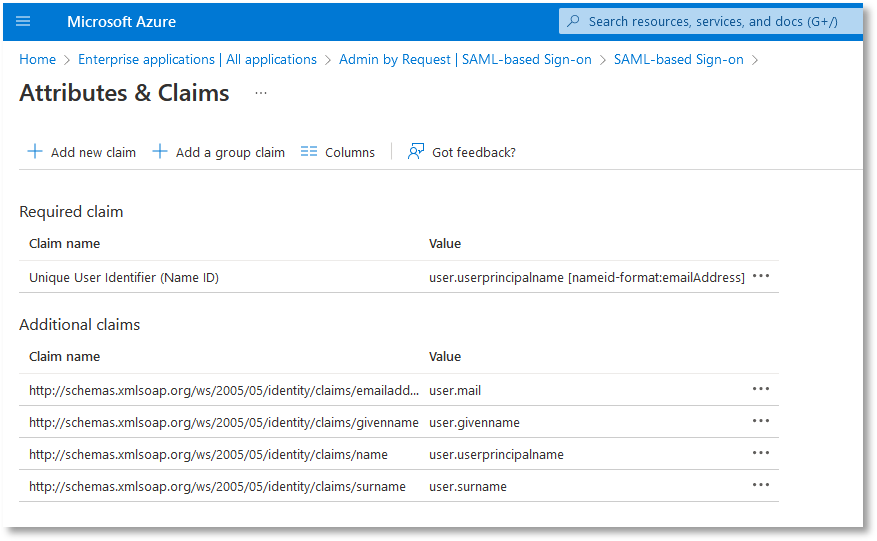
Now edit User Attributes & Claims to set Unique User identifier value to user.mail:
-
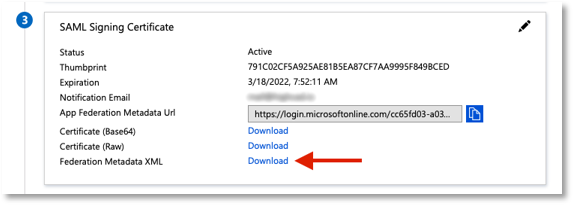
Now download your Federation Metadata XML and add it to Admin By Request under the Add Identity Provider (IDP) Metadata section:
-
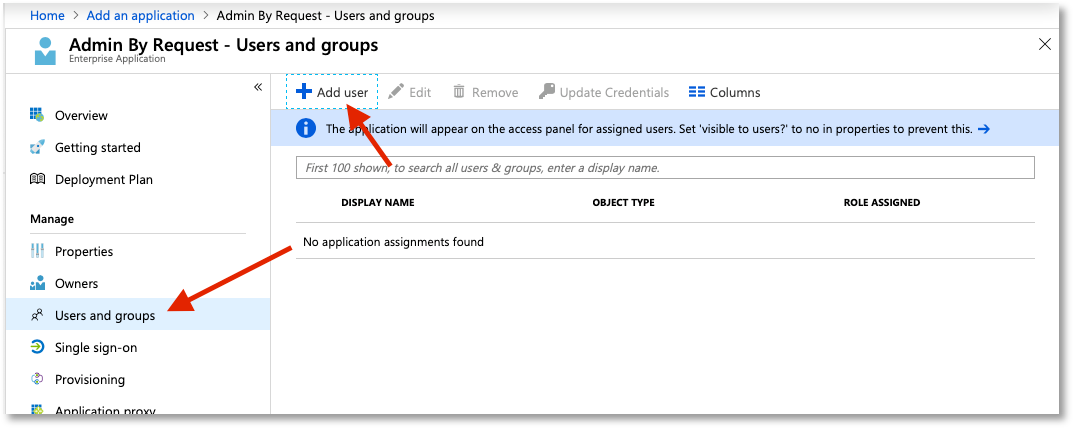
Finally, assign users that need access to the application. This is done in the ABR portal User Logins page. Simply add a user and select ADFS Single sign-on for [domain name] as Sign-on method.
-
In Microsoft Azure, you need add the same user under Users and Groups for the Admin By Request application:
Test your SSO configuration by logging-in as several users and verify that they can login successfully.
Active Directory Federation Services (ADFS)
Active Directory Federation Services (ADFS) is a Windows Server feature that enables your in-house Active Directory users to authenticate with external web applications via SAML, allowing them to log in using their regular AD credentials.
Prerequisites
-
A user account in the ABR portal, with sufficient rights to configure SSO:
-
Read-only view: OFF
-
Manage Settings: ON
-
Manage portal users: ON
-
-
A functional ADFS setup within your Windows server environment, including administrative access to the ADFS server.
Make sure you are logged-in to both the ADFS server and the ABR portal - you will switch between them during the configuration procedure.
Procedure
The tasks below are labeled the same as the sections in the ABR portal. Each task comprises a number of steps.
-
 Portal - create a new SSO entry
Portal - create a new SSO entry
-
In the ABR portal, go to Logins > Single Sign-on Setup.
-
Click New entry.
-
In field Name (e.g. domain):, enter the domain you want to use (usually your Active Directory or company domain name), select ADFS as Provider: and click Update:
The entry will be created and Status will be "Waiting for IDP metadata". Move to your ADFS server - we'll come back to the ABR portal later.
-
-
 ADFS server - add a Relying Party Trust
ADFS server - add a Relying Party Trust
-
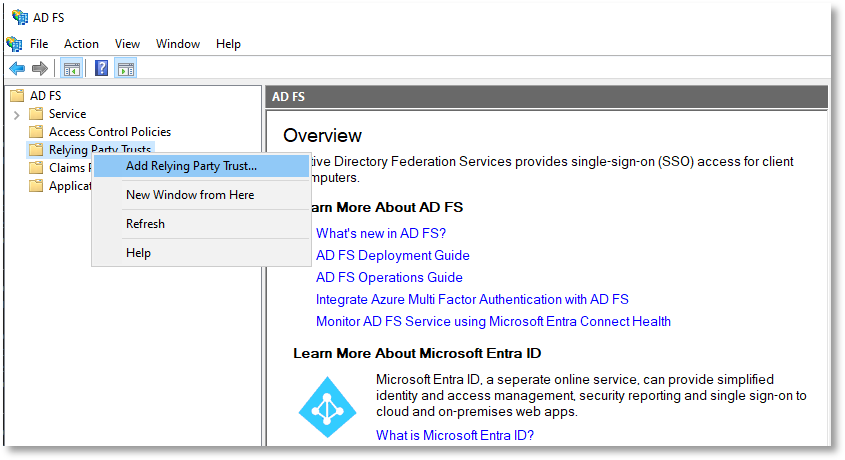
In the ADFS server, start AD FS Management and add a Relying Part Trust:
-
At the Welcome step, select Claims aware and click Start.
-
At the Select Data Source step, choose either of the first two options and click Next:
-
For the top option, enter the Admin By Request SAML metadata URL:
https://www.adminbyrequest.com/samlmeta -
For the second option, save the contents of this URL to a file (e.g. abrsaml.xml) and select the file using the Browse button.
You can obtain the contents by pasting the URL into the address bar of a browser and pressing Enter. The contents will appear in the page body.
-
-
At the Specify Display Name step, enter a name and click Next.
-
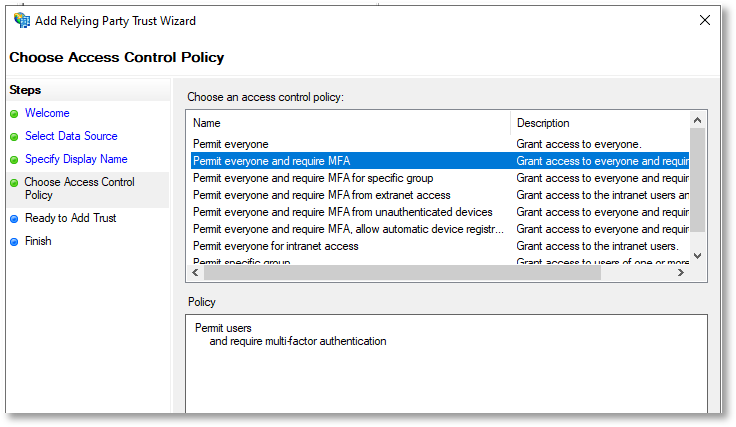
At the Choose Access Control Policy step, select the type of access control required and click Next.
The following example requires users to sign-in with MFA:
-
At the Ready to Add Trust step, review settings under each of the tabs and click Next, then Close.
-
-
 ADFS server - edit Claim Issuance Policy
ADFS server - edit Claim Issuance Policy
-
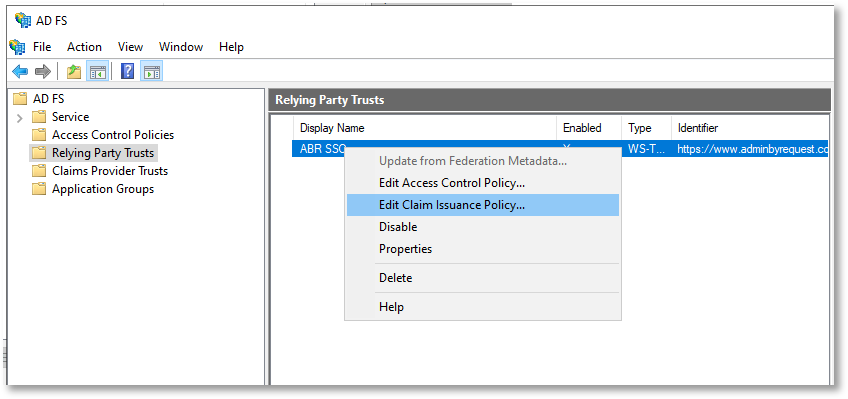
Right-click the newly created Relying Party Trust and select Edit Claim Issuance Policy...:
-
On the Issuance Transform Rules dialog, click button Add Rule....
-
At the Choose Rule Type step, select Send LDAP Attributes as Claims for the Claim rule template (this should be the default) and click Next.
-
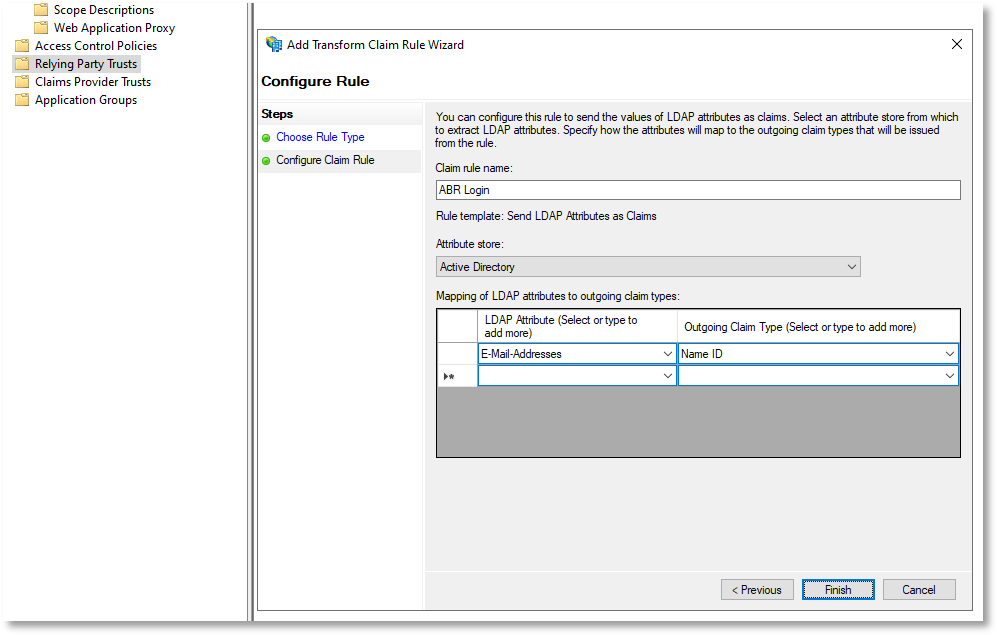
At the Configure Claim Rule step, enter the following:
-
Claim rule name: ABR Login (example only - type any name here)
-
Attribute store: select Active Directory
-
LDAP Attribute: select E-Mail-Addresses
-
Outgoing Claim Type: select Name ID
For the last two, the LDAP Attribute is mapped to the Outgoing Claim Type. This means that email addresses in Active Directory are matched to email addresses in the ABR portal (User Logins). If you do not have email addresses for your users in Active Directory, you will need to choose another LDAP attribute for the mapping.
The completed dialog should look like this:
-
-
Click Finish, followed by OK.
-
-
On your ADFS server, enter the following URL into a browser (substituting your ADFS server's fully qualified domain name):
https://<your.adfs.server>/FederationMetadata/2007-06/FederationMetadata.xmlThis downloads the file FederationMetadata.xml to your Downloads folder.
-
Open the file in notepad.exe or a similar text file editor.
-
Select and copy all the XML code.
-
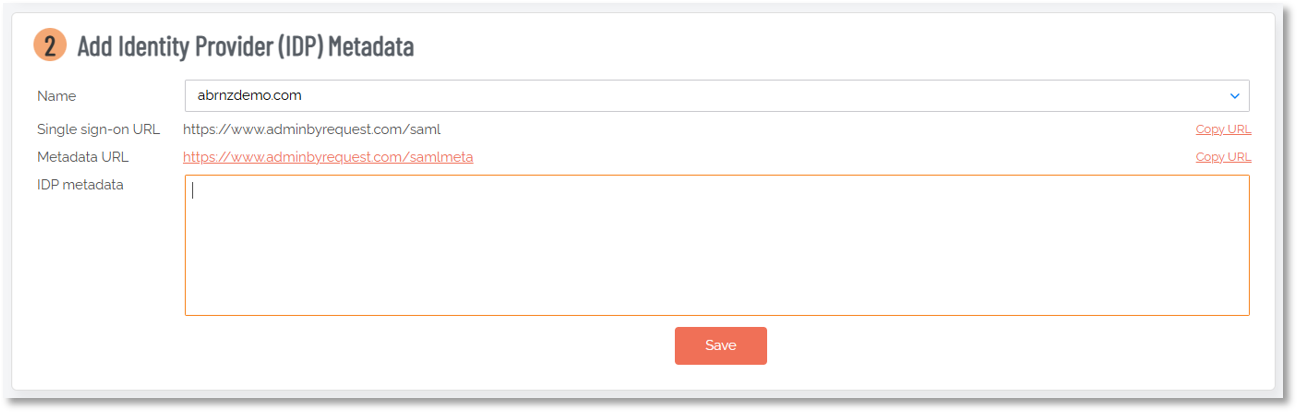
In the ABR portal, scroll down to section 2 Add Identity Provider (IDP) Metadata:
-
Make sure the correct Name is selected and paste the XML code into field IDP metadata.
-
Finally, click Save.
The Status of your entry should now be "Single sign-on enabled".
-
In the ABR portal, select Logins > User Logins.
-
For each user that will login to the ABR portal via ADFS:
-
Click EDIT.
-
Change the Sign-on Method to ADFS Single sign-on for <Name>, where <Name> is your Active Directory or company domain name entered earlier.
-
Click Save.
-
Test your SSO configuration by logging-in as several users and verify that they can login successfully.
Okta
Okta is an identity management platform that can connect your in-house Active Directory to external web applications using SAML. This integration allows users to authenticate with their usual AD credentials when accessing the portal.
Prerequisites
-
A user account in the ABR portal, with sufficient rights to configure SSO:
-
Read-only view: OFF
-
Manage Settings: ON
-
Manage portal users: ON
-
-
A valid account for the Okta portal as well as the ABR portal. Make sure you are logged-in to both portals - you will switch between them during the configuration procedure.
-
All your users who intend to login using Okta SSO must have their accounts and/or email addresses entered into your Okta portal. This makes them available to be assigned to the Admin By Request app once it is configured.
Procedure
The tasks below are labeled the same as the sections in the ABR portal. Each task comprises a number of steps.
-
In the ABR portal, go to Logins > Single Sign-on Setup.
-
Click New entry.
-
In field Name (e.g. domain):, enter the domain you want to use (usually your Active Directory or company domain name), select Okta as Provider: and click Update:
The entry will be created and Status will be "Waiting for IDP metadata". Move to your Okta portal - we'll come back to the ABR portal later.
-
In the Okta portal, go to Admin Console > Applications > Applications and click Browse App Catalog:
-
Search for Admin By Request, select it and click Add Integration:
-
Under General Settings, change the Application label if necessary and click Done:
-
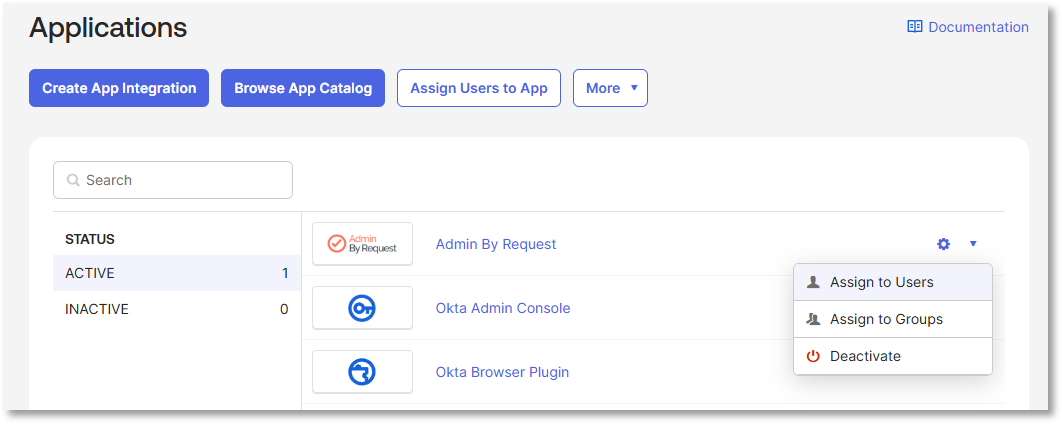
Click <- Back to Applications and then either click Assign Users to App or select Assign to Users from the settings drop-down menu:
-
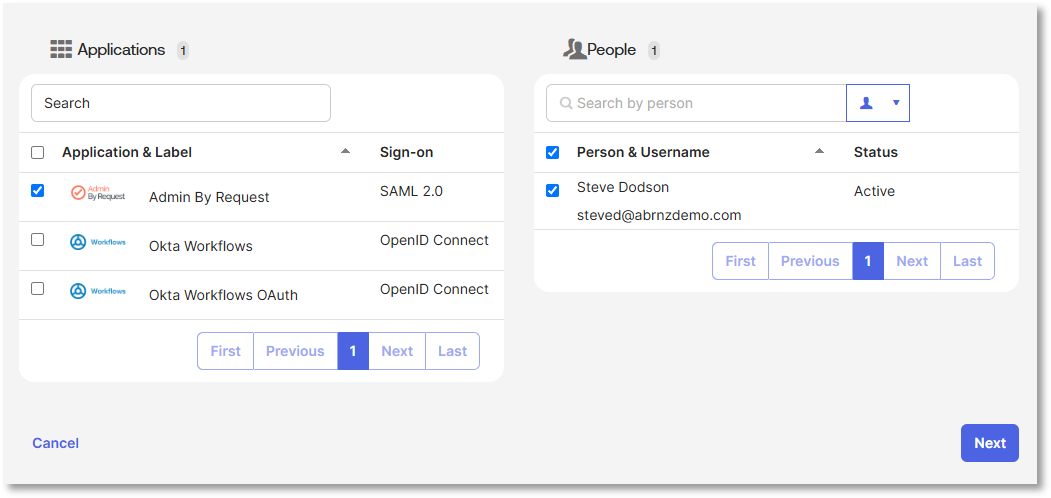
Select Admin By Request as the application in the left-hand column, and then select as many users as required in the right-hand column (People):
-
Click Next, then review and confirm the assignments.
Under the Assignments tab, you can now see a list of users assigned to the Admin By Request application.
-
In the Okta portal, go to the Sign On tab and, under heading Metadata details, copy the Metadata URL.
-
In a new browser tab, post the Metadata URL in the URL address bar and press Enter - the full XML should appear in the body of the page.
-
Select and copy all the XML code.
-
In the ABR portal, scroll down to section 2 Add Identity Provider (IDP) Metadata:
-
Make sure the correct Name is selected and paste the XML code into field IDP metadata.
-
Finally, click Save.
The Status of your entry should now be "Single sign-on enabled".
-
In the ABR portal, select Logins > User Logins.
-
For each user that will login to the ABR portal via Okta:
-
Click EDIT.
-
Change the Sign-on Method to Okta Single sign-on for <Name>, where <Name> is your Active Directory or company domain name entered earlier.
-
Click Save.
-
Test your SSO configuration by logging-in as several users and verify that they can login successfully.
Generic SAML
Security Assertion Markup Language (SAML) is an open standard that allows your in-house Active Directory to authenticate users with external web applications. This enables users to log in to the portal using their standard AD credentials.
If you are not using O365, Azure AD, AD FS or Okta, we do support SSO with any SAML identity provider. This means you can easily integrate with any SAML single sign-on provider, such as DUO, F5, Netscaler, One login, Idaptive or RSA.
Prerequisites
-
You need valid accounts for both the ABR portal and the SAML portal you intend to use. Make sure you are logged-in to both portals - you will switch between them during the configuration procedure.
-
Check login requirements for users - it's likely that all your users who intend to login using SAML must have their accounts and/or email addresses already entered into that system and available to be assigned to the Admin By Request app once it is configured.
Procedure
-
To set up generic SAML SSO, you simply create a SAML single sign-on domain with Generic SAML as the provider in the Single Sign-on Setup page in your ABR portal.
-
If your IdP supports automatic configuration, download our metadata at https://www.adminbyrequest.com/samlmeta.
If not, then use the following settings:-
Consumer URI: https://www.adminbyrequest.com/saml
-
Service Provider Entity ID: https://www.adminbyrequest.com/samlmeta
-
NameID format: E-mail address
-
-
After setting up the service provider, download the IdP / Federation metadata as XML and upload it to on the Single Sign-on Setup page and assign the login to users.
Questions?
If you have questions not answered on this page, please contact us using the chat or the contact menu at the top.