Terms and Definitions
Privileged Access
Privileged access refers to abilities and permissions that go above and beyond what is considered “standard”, allowing users (with privileged access) more control and reach in the system and network.
The following table describes several common privileged access terms.
|
Term |
Definition |
|---|---|
|
The opposite of a pre-approved list. A list of blocked programs or applications that are denied access in an IT environment (i.e., they are denied the ability to run) when everything is allowed by default. All items are checked against the list and granted access unless they appear on the list. Might also be known as a “blacklist” – a term no longer used. See also Pre-Approved List. |
|
|
An application that has been given greater privileges than what is considered standard, which enables the application user to have more control over its operation, and the app itself to have more abilities and access within the computer. |
|
|
Also known as “privileged access”. Elevated privileges provide the ability to do more than what is considered standard; for example, install and uninstall software, add and edit users, manage Group Policy, and modify permissions. Elevated privileges are sought after by attackers, who can use them to propagate through a network, remain undetected, and gain a strong foothold from which to launch further attacks. |
|
|
A physical device that is capable of connecting to and exchanging information with a computer network. Endpoints include mobile devices, desktop computers, virtual machines, embedded devices, servers, and Internet-of-Things (IoT) devices. |
|
|
An holistic approach to securing a network that goes beyond traditional anti-malware and aims to protect every endpoint from potential threats. See also EDR in the glossary. |
|
|
Also known as “account takeover”. Occurs when access to an account of a certain level (e.g., Standard User) is obtained from an account at that same level. Usually occurs when a malicious actor compromises a lower-level account and propagates through the network by compromising other lower-level accounts. See also Vertical Privilege Escalation. |
|
|
A way of enforcing the Principle of Least Privilege (POLP) by allowing access to privileged accounts and resources only when it is needed, rather than allowing “always on” access (also known as “standing access”). This reduces an organization’s attack surface by minimizing the amount of time an internal or external threat has access to privileged data and capability. |
|
|
A common technique used by malicious actors, in which they spread from the initial entry point further into the network, while evading detection, retaining access, and gaining elevated privileges using a combination of tactics. The purpose is generally to compromise as many accounts as possible, access high-value assets, and/or locate a specific target or payload. |
|
|
A type of social engineering attack in which the victim is tricked into clicking a malicious link that can lead to malware installation or further duping of the victim into providing sensitive information such as credentials or credit card details. |
|
|
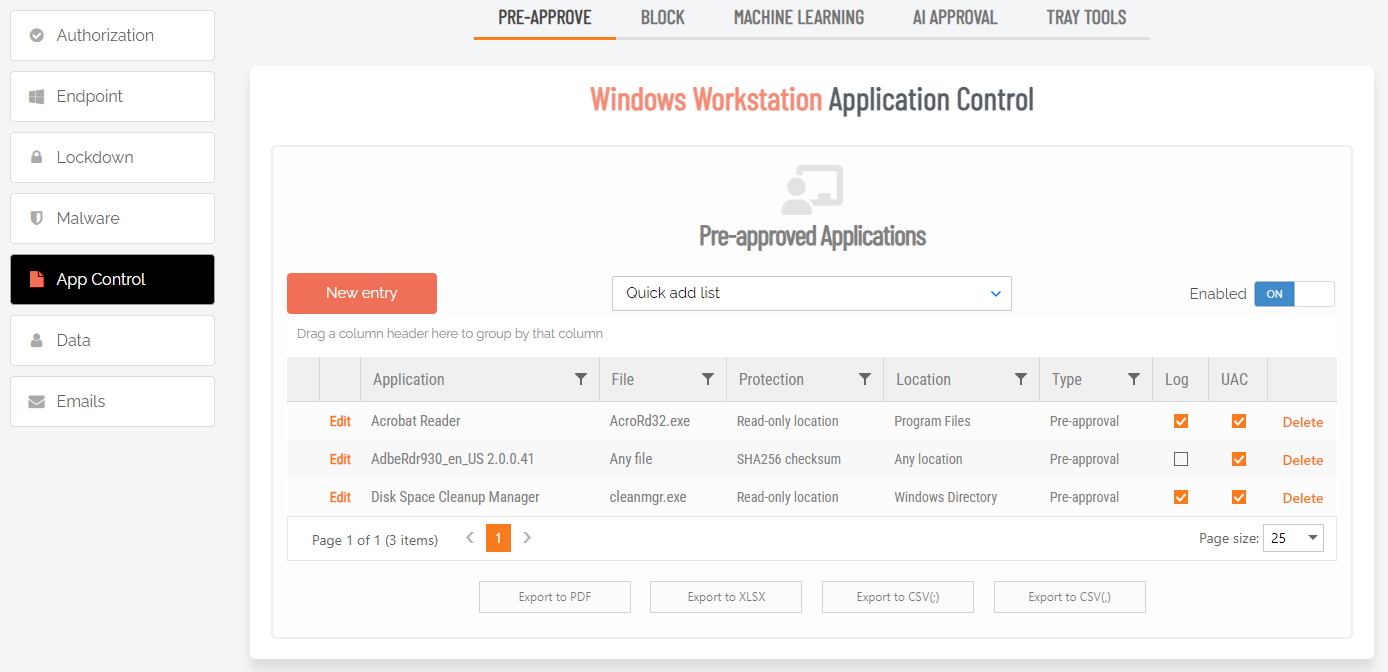
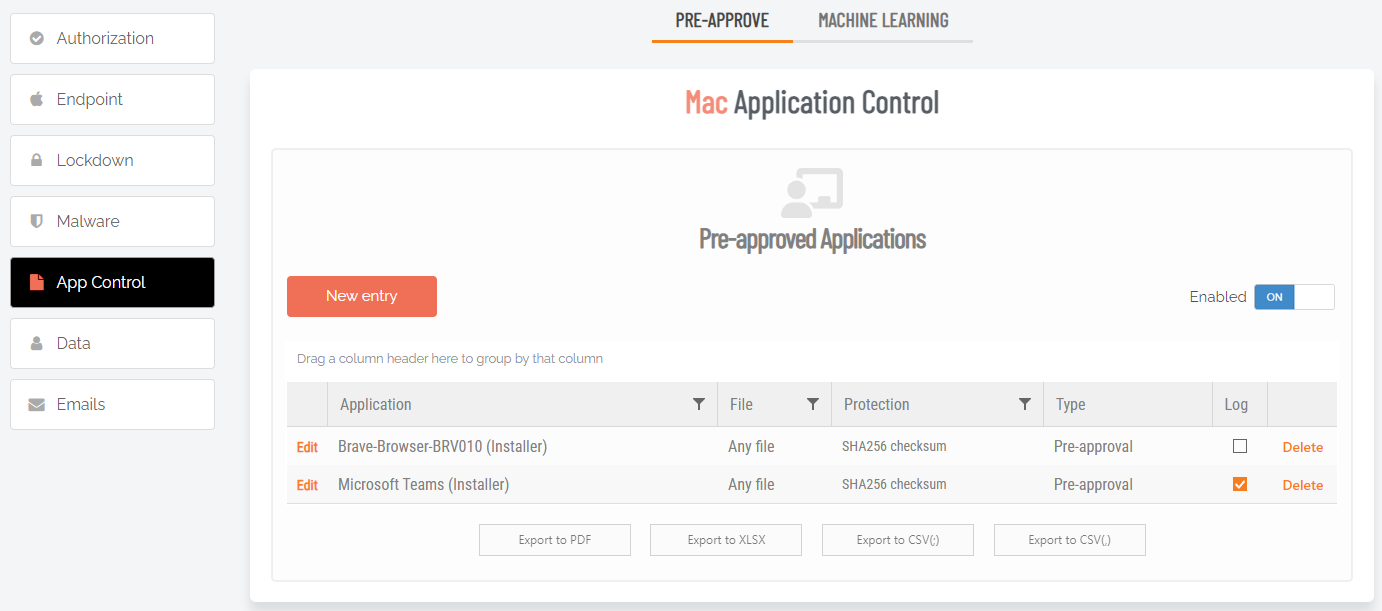
The opposite of a blocklist. A list of approved programs or applications that are trusted (considered safe) when everything is denied by default. Items are checked against the already approved list and are only able to run if they are included in that list. Might also be known as a “whitelist” – a term no longer used. See also Blocklist . |
|
|
An account that has been granted access and privileges beyond those granted to non-privileged accounts. More sought after by attackers because, if compromised, they provide a better vantage point from which to launch an attack. |
|
|
A trusted user who is authorized to leverage privileged access, such as through a privileged account, to perform high-value functions for which standard users are not authorized. |
|
|
A basic account for undertaking day-to-day tasks, for users who is not authorized or required to perform activities that require elevated privileges. These accounts are typically safer than those with higher access and permissions, as they do not provide the capability to perform administrative tasks, such as change system settings, install new software, manage the domain, and change local user credentials. |
|
|
Occurs when a lower-privileged account gains privileged access beyond what it is intended to have. Usually occurs when a malicious actor compromises an account (e.g., a “Standard User” account) and then exploits system flaws or overrides privilege controls to escalate that account to one with higher privileges (e.g., a “Local Administrator” account). See also Horizontal Privilege Escalation. |
Glossary
The following table lists the meanings of many acronyms used when discussing privileged access management and endpoint protection.
|
Term |
Short for |
Definition |
|---|---|---|
|
Administrative Template |
A group policy template in Windows. Group policy tools use Administrative Templates to populate policy settings in the user interface. They have the extension .admx. |
|
|
Azure Active Directory |
Azure Active Directory is part of Microsoft Entra, which is an enterprise identity service that provides single sign on, multi-factor authentication, and conditional access to guard against security threats. |
|
|
Microsoft Entra |
Microsft Entra is a family of multi-cloud identity and access solutions that includes Azure AD. The term "Entra ID" replaces the term "Azure AD". |
|
|
Endpoint Detection and Response |
A method of securing endpoints that focuses on detecting and responding to threats that are present. Works in conjunction with EPP. |
|
|
Endpoint Protection Platform |
A method of securing endpoints that focuses on preventing threats from arriving. Combines analysis, monitoring & management, anti-malware software, EDR capabilities and other security features into a comprehensive endpoint security platform. |
|
|
Fast Identity Online |
With FIDO Authentication, users sign in with phishing-resistant credentials, called Passkey. Passkeys can be synced across devices or bound to a platform or security key and enable password-only logins to be replaced with secure and fast login experiences across websites and apps. |
|
|
Microsoft Intune |
Microsoft Intune is a cloud-based UEM solution. It manages user access and simplifies device and application management for multiple platforms, including mobile devices, desktop computers, and virtual endpoints. |
|
|
Mobile Application Management |
Software and processes that secure and enable IT control over enterprise applications on end users' corporate and personal devices. |
|
|
Mobile Device Management |
A methodology and toolset used to provide a workforce with mobile productivity tools and applications, while keeping corporate data secure. |
|
|
Privileged Access Management |
A set of cybersecurity technologies and strategies that allow organizations to secure their infrastructure and applications by managing privileged access and permissions for all users across the IT environment. |
|
|
Passkey |
Passkeys are a replacement for passwords that provide faster, easier, and more secure sign-ins to websites and apps across a user’s devices. Unlike passwords, passkeys are always strong and phishing-resistant. |
|
|
Principle of Least Privilege |
The idea that users, applications, programs, and processes should be allowed only the bare minimum privileges necessary to perform their respective functions. |
|
|
Unified Endpoint Management |
A way to securely manage all the endpoints in an enterprise or an organization from a central location. |