Policies for Windows
About Policies
Settings in the Admin By Request client application are controlled in the portal under “Windows Settings” (Portal > Settings > Windows Settings). You can also define sub settings based on Computer or User Groups and/or OU.
It is highly recommended that you configure settings in the portal instead of using Group Policy Objects. If, for what-ever reason, you still want to overrule settings wholly or in part, you can set Policy keys either by using an ADMX file or by setting registry keys using GPO or by other means. Policy settings always overrule web settings.
Please note we do not recommend that you use
If you have any questions about portal settings or would like a demo of these, please feel free to contact us.
Using an ADMX File
To use a custom Admin By Request ADMX group policy file, download the file below. On the server on which you edit group policies, unpack the zip file to C:\Windows\PolicyDefinitions (or PolicyDefinitions under SYSVOL for central store). The settings will then appear under Computer Configuration.
Alternative without using a custom ADMX file
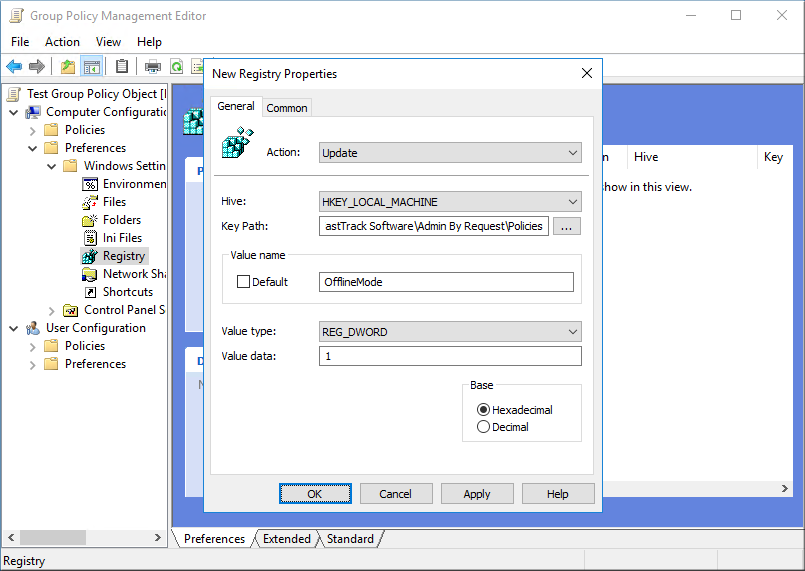
If you prefer, you can set the policy keys without using the custom ADMX file. Note that all these registry values are snapshotted during administrator sessions to avoid tampering by users. Policies are set under the registry key HKEY_LOCAL_MACHINE\Software\FastTrack Software\Admin By Request\Policies and must be set using the Group Policy editor. KeyPath must be Software\FastTrack Software\Admin By Request\Policies.
Overruling Portal Settings
| Key | Type | Workstation Default |
Server Default |
|---|---|---|---|
| AdminMinutes
|
REG_DWORD | 15 | 30 |
|
Number of minutes the user is administrator. This can also be set in your portal settings. |
|||
| AppInstructions
|
REG_SZ | ||
|
Body text for instructions (Code of Conduct) screen for app elevation (“Run As Administrator”). |
|||
| AppInstructionHeader
|
REG_SZ | ||
|
Header line for instructions (Code of Conduct) screen for app elevation (“Run As Administrator”). |
|||
| AppInstructionsShowInterval
|
REG_DWORD | ||
|
Interval in days to show the instructions (Code of Conduct). |
|||
| AllowBlacklistPIN
|
REG_SZ | 1 | 1 |
|
Allow unlocking with a PIN code when an application is blocked. |
|||
| AutoApprove
|
REG_DWORD | 1 | 0 |
|
Enables automatic session approval, if this setting is 1. If not configured or value is 0, cloud settings are used. |
|||
| AutoApproveApps
|
REG_DWORD | 1 | 0 |
|
Enables automatic app elevation approval, if this setting is 1. If not configured or value is 0, cloud settings are used. |
|||
| CleanAdminsGroup
|
REG_DWORD | 1 | 0 |
|
This setting removes users from the administrator’s group at login time, unless the user is administrator based on a domain group membership or is logging on using the built in administrator account. Refer to the FAQ for more information. |
|||
| CompanyName
|
REG_SZ | ||
|
Overrules the company name that appears on user interfaces, which is by default the licensed company name. |
|||
| ComputerGroups
|
REG_SZ | ||
|
If defined, the computer must be member of at least one of these groups. |
|||
| ComputerOUs
|
REG_SZ | ||
|
If defined, the computer must be located in one of these organizational units, or an OU under it. |
|||
| DenySessionSystemFileElevation
|
REG_DWORD | 0 | 1 |
|
Prevents the user from elevating any file in the system folder during an administrator session. |
|||
| DenySystemFileElevation
|
REG_DWORD | 0 | 1 |
|
Prevents the user from elevating any file in the system folder. |
|||
| EnableSessions
|
REG_DWORD | 1 | 1 |
|
Allow requesting admin sessions. |
|||
| EnableAppElevations
|
REG_DWORD | 1 | 1 |
|
Allow app elevation |
|||
| EmailFieldBehavior
|
REG_SZ | 1 | 1 |
|
Sets mode for the email request form field. Value values are “Mandatory”, “Optional” or “Hidden”. |
|||
| DesktopIcon
|
REG_DWORD | 1 | 1 |
|
Create desktop icon to elevate. |
|||
| EnableUAC
|
REG_DWORD | 1 | 1 |
|
Enables UAC, if it is not enabled. |
|||
| ExcludeUsers
|
REG_SZ | ||
|
Comma separated list of users to not revoke admin rights from. Domain users must be prefixed with domain and backslash. |
|||
| IconName
|
REG_SZ | ||
|
Overrules the default name of the desktop and programs icon. Note that the default icon name is localized. |
|||
| Instructions
|
REG_SZ | ||
|
Body text for instructions (Code of Conduct) screen for Admin Sessions. |
|||
| InstructionHeader
|
REG_SZ | ||
|
Header line for instructions (Code of Conduct) screen for Admin Sessions. |
|||
| InstructionsShowInterval
|
REG_DWORD | ||
|
Interval in days to show the instructions (Code of Conduct) |
|||
| InternetUpdate
|
REG_DWORD | 0 | 0 |
|
Allow automatic updating of the software over the internet. |
|||
| KillProcessesAtEnd
|
REG_SZ | 0 | 1 |
|
Kill UAC elevated processes, when session ends. |
|||
| MaxMalwareScanFileSize
|
REG_SZ | 250 | 250 |
|
Maximum file size allowed to upload to malware scanning (MB). |
|||
| LANUpdatePath
|
REG_SZ | ||
|
Automatically update the software from this UNC path. |
|||
| Language
|
REG_SZ | Auto | Auto |
|
User interface language. Default is to use the Windows user preference language. Forced language codes are English (EN), German (DE), Spanish (ES), French (FR), Danish (DA), Swedish (SV) or Norwegian (NN). |
|||
| LogFile
|
REG_SZ | ||
|
Optional log file. Every time a user elevates, it will be logged to this file. |
|||
| PhoneNoFieldBehavior
|
REG_SZ | 1 | 1 |
|
Sets mode for the phone no request form field. Value values are “Mandatory”, “Optional” or “Hidden”. |
|||
| RemoveUsersFromMMC
|
REG_DWORD | 1 | 1 |
|
Remove the ability to modify users and groups in Computer Management. |
|||
| ShowAppInstructions
|
REG_DWORD | 0 | 0 |
|
Show instructions (Code of Conduct) message when starting an app elevation (“Run As Administrator”). |
|||
| ShowInstructions
|
REG_DWORD | 0 | 0 |
|
Show instructions (Code of Conduct) message when starting an administrator session. |
|||
| ShowRunAsGfx
|
REG_DWORD | 0 | 0 |
|
Show the “Run As Administrator” graphics on the instructions (Code of Conduct) screen. |
|||
| RequireReason
|
REG_DWORD | 1 | 1 |
|
Enables requiring reason for admin sessions. If AutoApprove is 1, the reason is always required and this setting has no effect. |
|||
| RequireAppReason
|
REG_DWORD | 1 | 1 |
|
Enables requiring reason app elevations. If AutoApprove is 1, the reason is always required and this setting has no effect. |
|||
| UploadInventory
|
REG_DWORD | 1 | 1 |
|
Allow collection of inventory. |
|||
| UserGroups
|
REG_SZ | ||
|
If defined, the user must be member of at least one of these groups. Multiple groups are split by | (see notes below). This setting and the next three, can also be set in your cloud settings on this web site. Policies overrule cloud settings. |
|||
| UserOUs
|
REG_SZ | ||
|
If defined, the user must be located in one of these organizational units, or an OU under it. Multiple OUs are split by | (see next section). |
|||
Additional Server Edition Settings
| Key | Type | Default | Description |
|---|---|---|---|
| AccessRequestGroup | REG_SZ | Admin By Request Users | When not specified, the Admin By Request app will start. If the setting is set and the user is not a member, the Admin By Request app will not start. This setting is inteded to prevent the application from starting for Remote Desktop users on servers. Group and OU checks still applies. |
| LogAdminLogins | REG_DWORD | 1 | Logs the session log on and log off to the “Admin Logins” tab, when an administrator (the build-in administrator account or an account that is administrator through a group) logs on. |
Group and OU Delimiter
Multiple groups or OUs must be split by a vertical pipe, such as “Domain Admins|Customer Relations”. This is because commas may naturally appear in groups or OU names and always appear in full distinguished names for OUs. An OU can be specified as a full distinguished name or simply the OU name itself.
-
If an OU name is not unique, the check will happen on either. In a list, the user/computer must be a member of one (not all) to allow administrator elevation.
-
Local users (except Administrator) cannot elevate when domain groups or OUs are in place. Users can always request a PIN code for elevation, in case of an exception.
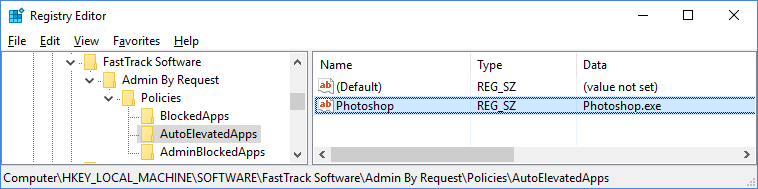
Auto-Elevated Applications
Some applications may always need to run as administrator. A list of applications can be set using policies. For example, if Photoshop always needs to run as administrator (regardless of other settings), a name/data entry can be set under the subkey “AutoElevatedApps”. Only the value is used and it can be a full path to an exe file or just the exe file.
This feature requires UAC enabled to function and the user will be prompted for credentials on application start and must enter user name and password. This "credentials prompt" is a UAC limitation that cannot be bypassed. But the application will run as elevated administrator without the user being administrator:
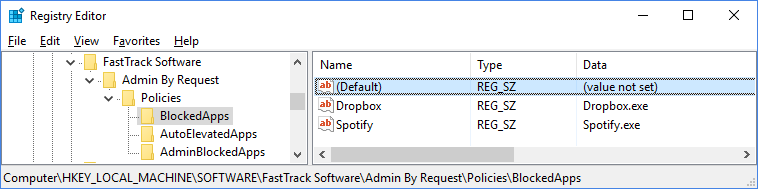
Blocked Applications
Applications that are never allowed to run, can be set using the “BlockedApps” subkey. These are applications that will always be blocked from execution, regardless of being elevated or not:
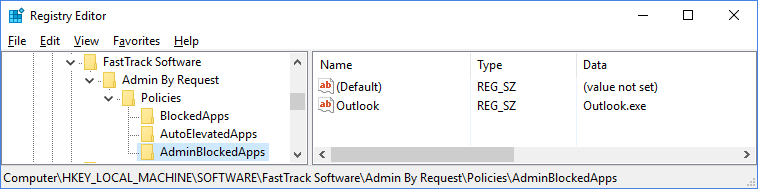
Admin Blocked Applications
Applications can be blocked, only when the user is elevated by Admin By Request and only when user runs the application as administrator. For example, if the user elevates to administrator, it would make sense to block Outlook.exe, so the user does not start Outlook and click dangerous links. Browsers could also be blocked, if the policy is that users must download software before elevation, to try to sandbox the installation as much as possible.