Compliance Mapping
Introduction
The tables under the compliance standards below outline how Admin By Request helps your organization comply with each framework.
A PDF is available for each table - expand the relevant framework to view and download.
GDPR
 Relevant articles, requirements and how ABR helps
Relevant articles, requirements and how ABR helps
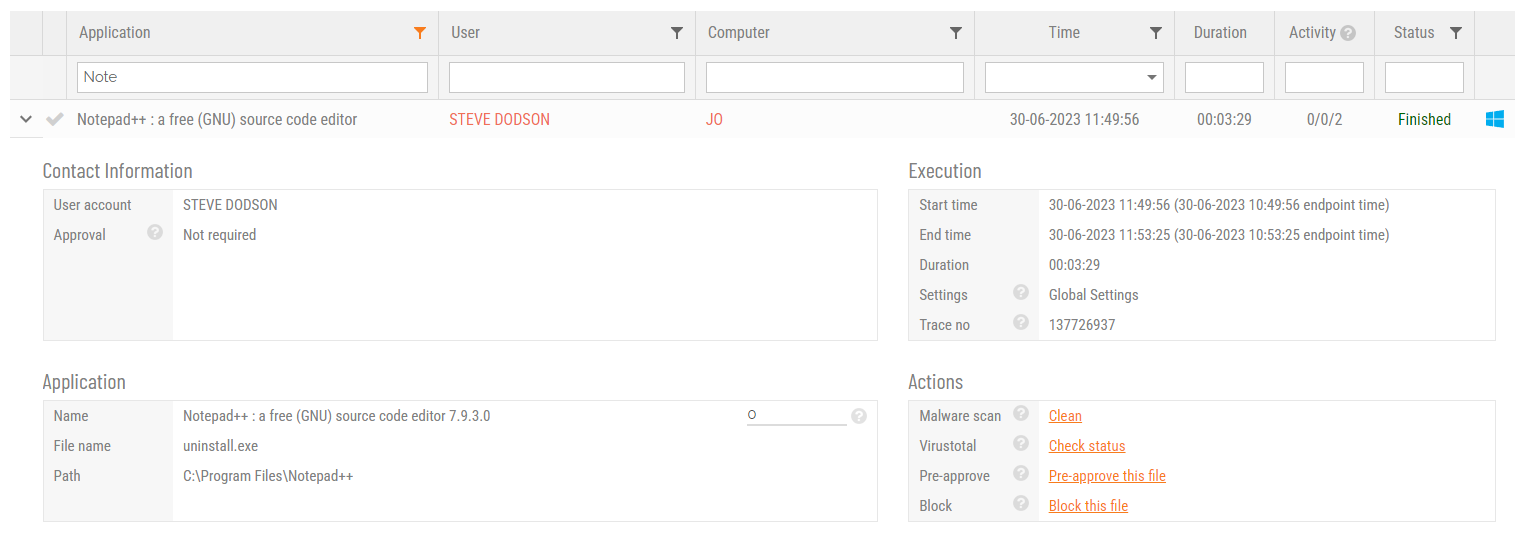
![]() GDPR - How Admin By Request Helps
GDPR - How Admin By Request Helps
|
Article |
Requirement |
How ABR helps to ensure compliance |
|---|---|---|
|
Article 25 Data Protection by Design and by Default
|
Article 25(1) Taking into account the state of the art, the cost of implementation and the nature, scope, context and purposes of processing, as well as the risks of varying likelihood and severity for rights and freedoms of natural persons posed by the processing, the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organizational measures, such as:
in order to meet the requirements of this Regulation and protect the rights of data subjects. |
By enforcing a least privilege approach to manage privileged access, your organization will be able to demonstrate that you, by default, grant access to personal data for a specific purpose and limit the access to those as much as possible. Besides that, as Admin By Request is used within your organization, and therefore collecting and processing your personal data from your employees, the product's capability to disable/limit collection and processing of certain personal data ensures that you process only what is necessary for the purpose of Admin By Request. |
|
Article 25(2) The controller shall implement appropriate technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed. That obligation applies to the amount of personal data collected, the extent of their processing, the period of their storage and their accessibility. In particular, such measures shall ensure that by default personal data are not made accessible without the individual's intervention to an indefinite number of natural persons. |
Admin By Request, as a processor, holds ISO 27001 certification, SOC 2 Type 2 report, Cyber Essentials Plus certificate, and other attestations. These certifications and reports serve as sufficient guarantees that Admin By Request implements appropriate technical and organizational measures in accordance with GDPR requirements, ensuring the protection of the rights of data subjects when processing data on behalf of controllers. |
|
|
Article 28 Processor |
Article 28(1) Where processing is to be carried out on behalf of a controller, the controller shall use only processors providing sufficient guarantees to implement appropriate technical and organizational measures in such a manner that processing will meet the requirements of this Regulation and ensure the protection of the rights of the data subject. |
Admin By Request, as a processor, holds ISO 27001 certification, SOC 2 Type 2 report, Cyber Essentials Plus certificate, and other attestations. These certifications and reports serve as sufficient guarantees that Admin By Request implements appropriate technical and organizational measures in accordance with GDPR requirements, ensuring the protection of the rights of data subjects when processing data on behalf of controllers. |
|
Article 32 Security of Processing |
Article 32(1) [...] the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including inter-alia as appropriate:
|
Admin By Request enhances Article 32 compliance by:
It strengthens security of processing by mitigating the risk of unauthorized access, ensuring accountability, and facilitating proactive measures to safeguard personal data. |
|
Article 5 Principles relating to the processing of personal data |
Accountability |
Admin By Request strengthens accountability by documenting and logging privileged access and reduces the risk of GDPR fines and litigation by ensuring transparency in privileged access logs. |
ISO 27001
 Relevant controls, objectives and how ABR helps
Relevant controls, objectives and how ABR helps
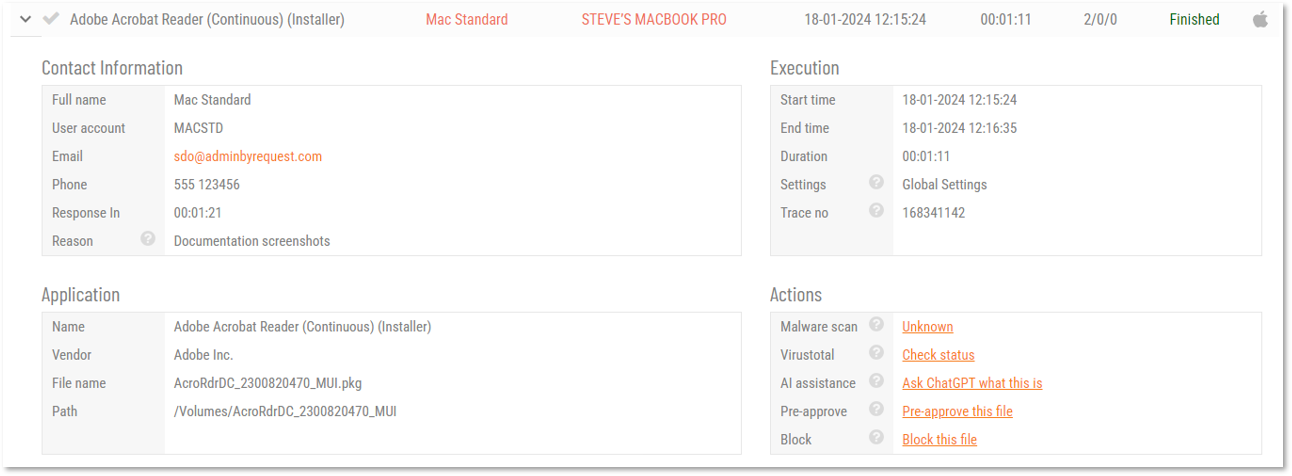
![]() ISO 27001 - How Admin By Request Helps
ISO 27001 - How Admin By Request Helps
|
ISO 27001 Control |
Control Objective |
How ABR helps with compliance |
|---|---|---|
|
Requirements of the Information Management System |
||
|
9.1 Monitoring, measurement, analysis and evaluation |
|
Admin By Request includes monitoring and auditing features that allow you to track and review elevation requests, system activities, and user behavior. This aligns with the ISO 27001 requirement for regular monitoring and analysis of user access to identify any unauthorized or inappropriate activities. Any evaluation effort for the part of your ISMS concerning privileged access will be easy and effective with the auditlog in the Admin By Request portal. |
|
9.2 Internal audit |
|
When performing internal audits, it is important that your auditor is able to review relevant information and export data. The auditlog in Admin By Request ensures full auditability with correct and tamper-proof records. |
|
9.3 Management review |
|
Auditlogs and traceability are essential to provide transparent and efficient reports to the management. This enables management and other stakeholders to take important decisions and evaluate the need for a more strict or loose approach towards management of privileged access. Admin By Request strengthens accountability by documenting and logging privileged access and reduces the risk of GDPR fines and litigation by ensuring transparency in privileged access logs. |
|
10 Improvement |
|
|
|
Annex A Controls |
||
|
A.8.1.3 Acceptable use of assets |
Assets associated with information and information processing facilities shall be identified and an inventory of these assets shall be drawn up. |
An automated solution with secure work flows for elevating applications on the users' endpoints will remove the need for manual procedures, the effectiveness of which is dependent on the user's willingness to comply. When using Admin By Request, you will know that the user elevates applications only when they are allowed to do so. |
|
A.9.1.1 Access Control Policy |
An access control policy shall be established, documented and reviewed based on business and information security requirements. |
Policies on management of privileged access are essential to any access control policy. To manage these with a tool such as Admin By Request will ensure positive feedback from your auditors. |
|
A.9.2.3 Management of privileged access rights |
The allocation and use of privileged access rights shall be restricted and controlled. |
Admin By Request is a Privileged Access Management solution. By definition, the answer to this control objective. |
|
A.9.4.4 Use of privileged utility programs |
The use of utility programs that might be capable of overriding system and application controls shall be restricted and tightly controlled. |
As utility programmes can be downloaded from the internet, users must be restricted in their ability to install such software. Elevation of such programmes should be logged and monitored/reviewed periodically as well. All of this can be enforced using Admin By Request. |
|
A.12.4.1 Event logging |
Event logs recording user activities, exceptions, faults and information security events shall be produced, kept and regularly reviewed. |
The Admin By Request auditlog provides for a full record of all privileged access user activity including installs, uninstalls, elevated processes, duration, time, dates etc. |
|
A12.4.2 Protection of log information |
Logging facilities and log information shall be protected against tampering and unauthorized access. |
The Admin By Request auditlog can only be accessed in the Admin By Request portal by portal users. You can enforce access to the portal with SSO and MFA to further ensure only authorized access. Further, the auditlog cannot be changed or deleted and is therefore fully tamper-proof. |
|
A.12.4.3 |
System administrator and system operator activities shall be logged and the logs protected and regularly reviewed. |
The auditlog provides information on all users with Admin By Request on their endpoint. Furthermore, the Settings Change log also provides information on which portal users have changed settings and when. |
|
A.12.6.2 |
Rules governing the installation of software by users shall be established and implemented. |
Admin By Requests enables your organization to restrict software installations in a proportional manner that fits into your risk assessments. The flexibility of the many different configuration options allows both a strict approach as well as a less strict approach - all while maintaining full productivity for your employees. |
|
A.12.7.1 |
Audit requirements and activities involving verification of operational systems shall be carefully planned and agreed to minimize disruptions to business processes. |
Access and review of auditlogs does not interfere with the usage of Admin By Request or disrupt any other service in the organization. |
|
A.14.2.1 |
Rules for the development of software and systems shall be established and applied to developments within the organization. |
Your developers may fear that they need to request approval to elevate all applications. However, for certain groups of users, you can ensure auditlogs of their elevations by using Admin Sessions which allows them to act as admin for a limited period of time. In this way, you can add control to your SDLC while maintaining efficiency and seamless work procedures in your development team. |
|
A.16.1.6 Learning from information security incidents |
Knowledge gained from analyzing and resolving information security incidents shall be used to reduce the likelihood or impact of future incidents. |
Collection of evidence is crucial to be able to learn from and to recover from a security incident. A comprehensive log such as the Admin By Request auditlog will be useful to gather potential evidence.
|
|
A.16.1.7 Collection of evidence |
The organization shall define and apply procedures for the identification, collection, acquisition and preservation of information, which can serve as evidence. |
|
SOC 2
 Relevant criteria, requirements and how ABR helps
Relevant criteria, requirements and how ABR helps
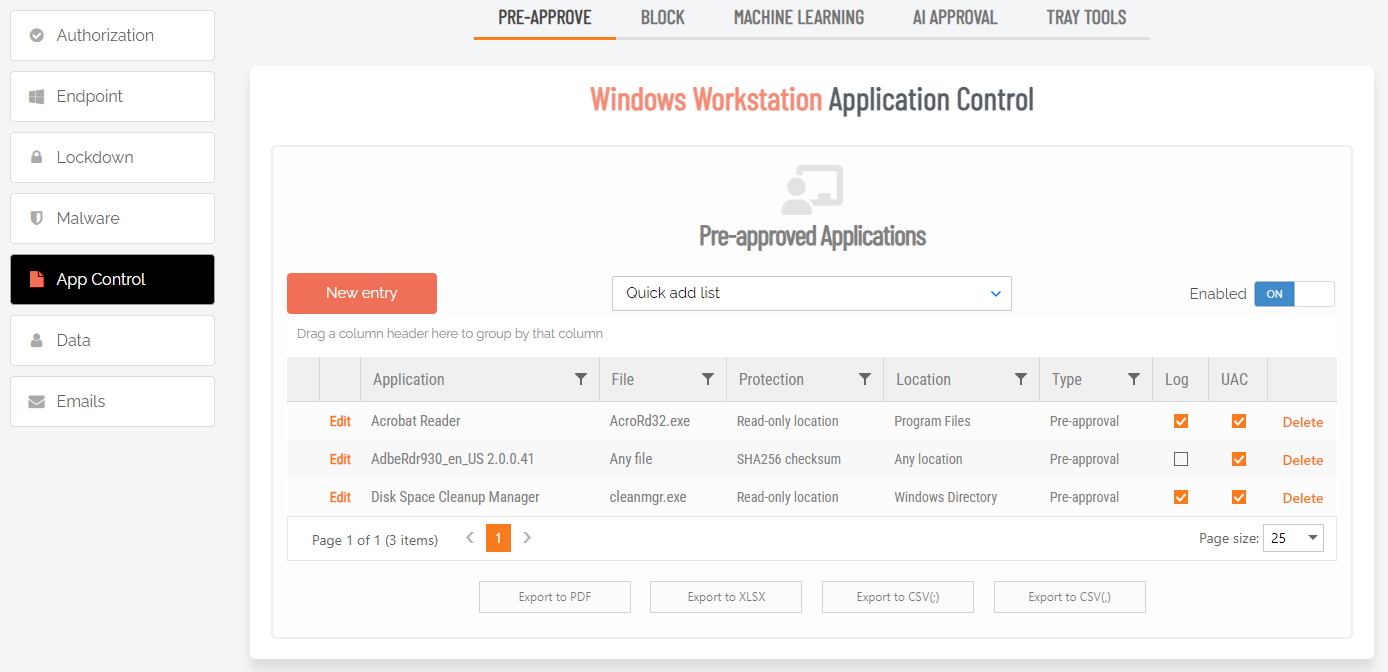
![]() SOC 2 - How Admin By Request Helps
SOC 2 - How Admin By Request Helps
|
Trust Service |
Requirement |
How ABR helps to ensure compliance |
|---|---|---|
|
CC4.1 |
COSO Principle 16: The entity selects, develops, and performs ongoing and/or separate evaluations to ascertain whether the components of internal control are present and functioning. |
By using Admin By Request, you will ease the burden on your internal access reviews as privileged accounts do not exist. |
|
CC5.2 |
COSO Principle 11: The entity also selects and develops general control activities over technology to support the achievement of objectives. |
Admin By Request ensures preventive, detective and automated privileged access controls throughout the entire organization, which is a mandatory control to meet the SOC 2 requirements. |
|
CC6.1 |
The entity implements logical access security software, infrastructure, and architectures over protected information assets to protect them from security events to meet the entity's objective. |
Admin By Request ensures that privileged access to sensitive resources is restricted to authorized personnel on a per application basis or for a limited period of time. This eases the burden on IT resources and meets the requirements on implementation of logical access security software. Features such as Remote Access in Admin By Request Server Edition also help you to connect securely to servers and establish and maintain inventory of assets in your network. |
|
CC6.3 |
The entity authorized, modifies, or removes access to data, software, functions, and other protected information assets based on roles, responsibilities, or the system design and changes, giving consideration to the concepts of least privilege and segregation of duties, to meet the entity's objectives. |
|
|
CC6.6 |
The entity implements logical access security measures to protect against threats from outside its systems' boundaries. |
Access to sensitive resources within your environment is made easy and secure is made very easy with the Remote Access functionality in Admin By Request Server Edition, which leverages familiar Admin By Request approval flows and features to enable secure, browser-based connections to servers and network endpoints. This solution revolutionizes the way IT administrators manage and access critical systems by eliminating reliance on traditional VPNs and jump servers, while maintaining a secure and segregated setup, with all features and configurations accessible from the intuitive and familiar Admin By Request Portal. Furthermore, by using Admin By Request, you can demonstrate compliance with the protection of each endpoint in your organization.
|
|
CC6.7 |
The entity resticts the transmission, movement, and removal of information to authorized internal and external users and processes, and protects it during transmission, movement, or removal to meet the entity's objectives. |
|
|
CC6.8 |
The entity implements controls to prevent or detect and act upon the introduction of unauthorized or malicious software to meet the entity's objective. |
The integration between Admin By Request and OPSWAT MetaDefender enables your organization to prevent malicious software from entering your environment through its endpoints. When a user requests to run a file with administrative privileges, the file can be scanned in real-time to block malware using several anti-virus engines. This happens without any performance or waiting penalty and it doesn’t conflict with any security software you may have on your endpoints, because it happens in the cloud. If the file is flagged as malicious, it is blocked before it can do any damage |
NIST SP 800-53
 Relevant identifiers, controls and how ABR helps
Relevant identifiers, controls and how ABR helps
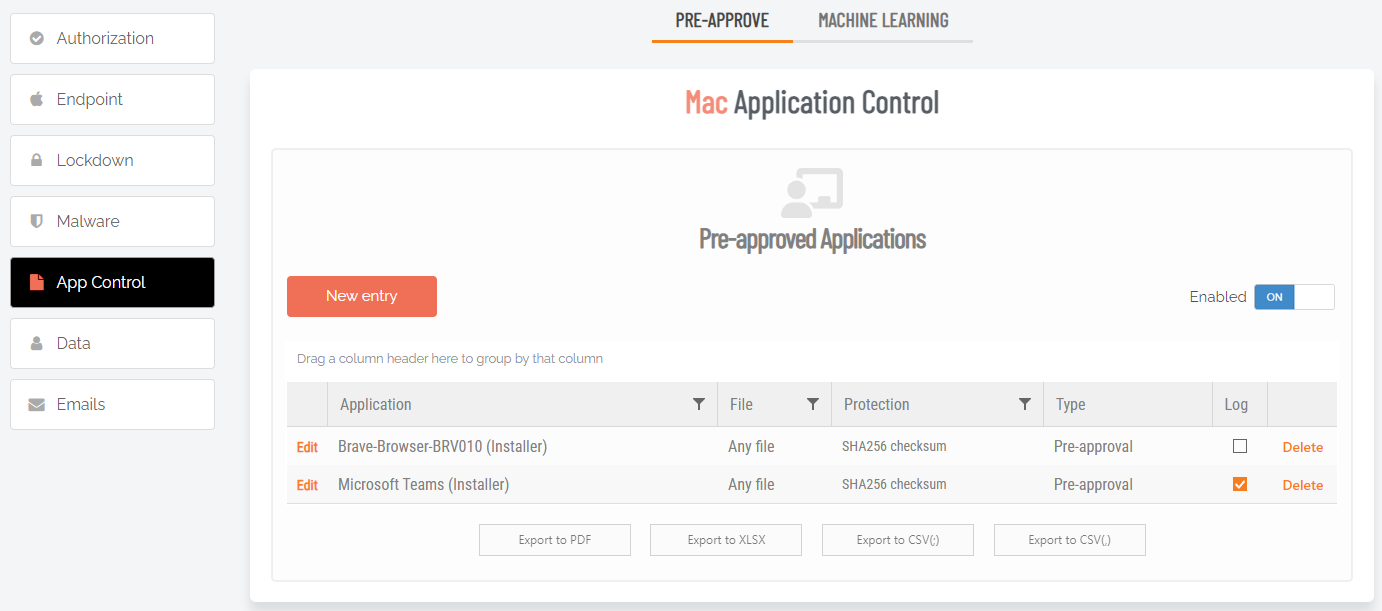
![]() NIST SP 800-53 - How Admin By Request Helps
NIST SP 800-53 - How Admin By Request Helps
|
Control (ID, Name) |
Control (Discussion) |
How ABR helps with compliance |
|---|---|---|
|
AC-1 Policy and Procedures
|
Access control policy and procedures address the controls in the AC family that are implemented within systems and organizations. The risk management strategy is an important factor in establishing such policies and procedures. Policies and procedures contribute to security and privacy assurance. Therefore, it is important that security and privacy programs collaborate on the development of access control policy and procedures. Security and privacy program policies and procedures at the organization level are preferable, in general, and may obviate the need for mission- or system-specific policies and procedures. The policy can be included as part of the general security and privacy policy, or be represented by multiple policies reflecting the complex nature of organizations. Procedures:
Events that may precipitate an update to access control policy and procedures include assessment or audit findings, security incidents or breaches, or changes in laws, executive orders, directives, regulations, policies, standards, and guidelines. Simply restating controls does not constitute an organizational policy or procedure. |
Admin By Request aids in implementing robust policies and procedures by providing privileged access management capabilities. It allows organizations to enforce the principle of least privilege, ensuring that users only have elevated privileges when necessary. This aligns with SOC 2 criteria related to access controls and authorization. |
|
AC-2 Account Management
|
Examples of system account types include individual, shared, group, system, guest, anonymous, emergency, developer, temporary, and service. Identification of authorized system users and the specification of access privileges reflect the requirements in other controls in the security plan. Users requiring administrative privileges on system accounts receive additional scrutiny by organizational personnel responsible for approving such accounts and privileged access, including system owner, mission or business owner, senior agency information security officer, or senior agency official for privacy. Types of accounts that organizations may wish to prohibit due to increased risk include shared, group, emergency, anonymous, temporary, and guest accounts. Where access involves personally identifiable information, security programs collaborate with the senior agency official for privacy to establish the specific conditions for group and role membership; specify authorized users, group and role membership, and access authorizations for each account; and create, adjust, or remove system accounts in accordance with organizational policies. Policies can include such information as account expiration dates or other factors that trigger the disabling of accounts. Organizations may choose to define access privileges or other attributes by account, type of account, or a combination of the two. Examples of other attributes required for authorizing access include restrictions on time of day, day of week, and point of origin. In defining other system account attributes, organizations consider system-related requirements and mission/business requirements. Failure to consider these factors could affect system availability. |
Admin By Request aids in implementing robust account management by providing privileged access management capabilities. It allows organizations to enforce the principle of least privilege, ensuring that users only have elevated privileges when necessary. This aligns with SOC 2 criteria related to access controls and authorization. |
|
AC-2 (2) Account Management: Automated Temporary and Emergency Account Management Automatically remove and/or disable temporary and emergency accounts after a set time period for each type of account. |
Temporary and emergency accounts are intended for short-term use. Organizations establish temporary accounts as part of normal account activation procedures when there is a need for short-term accounts without the demand for immediacy in account activation. Organizations establish emergency accounts in response to crisis situations and with the need for rapid account activation. Therefore, emergency account activation may bypass normal account authorization processes. Emergency and temporary accounts are not to be confused with infrequently used accounts, including local logon accounts used for special tasks or when network resources are unavailable (may also be known as accounts of last resort). Such accounts remain available and are not subject to automatic disabling or removal dates. Conditions for disabling or deactivating accounts include when shared/group, emergency, or temporary accounts are no longer required and when individuals are transferred or terminated. Changing shared/group authenticators when members leave the group is intended to ensure that former group members do not retain access to the shared or group account. Some types of system accounts may require specialized training. Management of temporary and emergency accounts includes the removal or disabling of such accounts automatically after a predefined time period rather than at the convenience of the system administrator. Automatic removal or disabling of accounts provides a more consistent implementation. |
A feature of Admin By Request is its Break Glass capability, which allows administrators to create a new, temporary, one-time-use Administrator account that works on domains, Azure AD and stand-alone endpoints. This account audits all elevated activity while in use and terminates within a predefined amount of time or on log out.
Break Glass security elements
|
|
AC-2 (6) Account Management: Dynamic Privilege Management Implement organization-defined dynamic privilege management capabilities. |
In contrast to access control approaches that employ static accounts and predefined user privileges, dynamic access control approaches rely on run-time access control decisions facilitated by dynamic privilege management, such as attribute-based access control. While user identities remain relatively constant over time, user privileges typically change more frequently based on ongoing mission or business requirements and the operational needs of organizations. An example of dynamic privilege management is the immediate revocation of privileges from users as opposed to requiring that users terminate and restart their sessions to reflect changes in privileges. Dynamic privilege management can also include mechanisms that change user privileges based on dynamic rules as opposed to editing specific user profiles. Examples include automatic adjustments of user privileges if they are operating out of their normal work times, if their job function or assignment changes, or if systems are under duress or in emergency situations. Dynamic privilege management includes the effects of privilege changes, for example, when there are changes to encryption keys used for communications. |
Admin By Request addresses this requirement as it allows your organization to grant privileged access on a per application basis or in a restricted time window. |
|
AC-2 (7) Account Management: Privileged User Accounts
|
Privileged roles are organization-defined roles assigned to individuals that allow those individuals to perform certain security-relevant functions that ordinary users are not authorized to perform. Privileged roles include key management, account management, database administration, system and network administration, and web administration. A role-based access scheme organizes permitted system access and privileges into roles. In contrast, an attribute-based access scheme specifies allowed system access and privileges based on attributes. |
You can set up different user groups with different sub-settings in Admin By Request to require approval for some, while not requiring approval for others. All activities can be audited in the auditlog. |
|
AC-3 (2) Access Enforcement: Dual Authorization Enforce dual authorization for organization-defined privileged commands and/or other organization-defined actions. |
Dual authorization, also known as two-person control, reduces risk related to insider threats. Dual authorization mechanisms require the approval of two authorized individuals to execute. To reduce the risk of collusion, organizations consider rotating dual authorization duties. Organizations consider the risk associated with implementing dual authorization mechanisms when immediate responses are necessary to ensure public and environmental safety. |
Through integrations, you can setup dual authorization work flows in, e.g. Jira, to ensure dual authorization. |
|
AC-3 (7) Access Enforcement: Role-based Access Control Enforce a role-based access control policy over defined subjects and objects and control access based upon organization-defined roles and users authorized to assume such roles. |
Role-based access control (RBAC) is an access control policy that enforces access to objects and system functions based on the defined role (i.e., job function) of the subject. Organizations can create specific roles based on job functions and the authorizations (i.e., privileges) to perform needed operations on the systems associated with the organization-defined roles. When users are assigned to specific roles, they inherit the authorizations or privileges defined for those roles. RBAC simplifies privilege administration for organizations because privileges are not assigned directly to every user (which can be a large number of individuals) but are instead acquired through role assignments. RBAC can also increase privacy and security risk if individuals assigned to a role are given access to information beyond what they need to support organizational missions or business functions. RBAC can be implemented as a mandatory or discretionary form of access control. For organizations implementing RBAC with mandatory access controls, the requirements in AC-3 (3) define the scope of the subjects and objects covered by the policy. |
You can set up different user groups with different sub-settings in ABR to ensure that users with different roles have the access they need. |
|
AC-5 Separation of Duties
|
Separation of duties addresses the potential for abuse of authorized privileges and helps to reduce the risk of malevolent activity without collusion. Separation of duties includes dividing mission or business functions and support functions among different individuals or roles, conducting system support functions with different individuals, and ensuring that security personnel who administer access control functions do not also administer audit functions. Because separation of duty violations can span systems and application domains, organizations consider the entirety of systems and system components when developing policy on separation of duties. |
By enabling "Require approval" in Admin By Request, another person will need to approve a user's privileged access before it is granted. In this way, duties are separated. |
|
AC-6 Least Privilege Employ the principle of least privilege, allowing only authorized accesses for users (or processes acting on behalf of users) that are necessary to accomplish assigned organizational tasks. |
Organizations employ least privilege for specific duties and systems. The principle of least privilege is also applied to system processes, ensuring that the processes have access to systems and operate at privilege levels no higher than necessary to accomplish organizational missions or business functions. Organizations consider the creation of additional processes, roles, and accounts as necessary to achieve least privilege. Organizations apply least privilege to the development, implementation, and operation of organizational systems. |
By removing admin rights from all users and granting privileges on a per-application basis or for a limited time, you will be able to demonstrate enforcement of the least privilege principle.
|
|
AC-6 (1) Least Privilege: Authorized Access to Security Functions Authorize access for authorized personnel to carry out itemized security functions, with security-relevant information. |
Security functions include establishing system accounts, configuring access authorizations (i.e., permissions, privileges), configuring settings for events to be audited, and establishing intrusion detection parameters. Security-relevant information includes filtering rules for routers or firewalls, configuration parameters for security services, cryptographic key management information, and access control lists. Authorized personnel include named individuals or roles such as security administrators, system administrators, system security officers, system programmers, and other privileged users. |
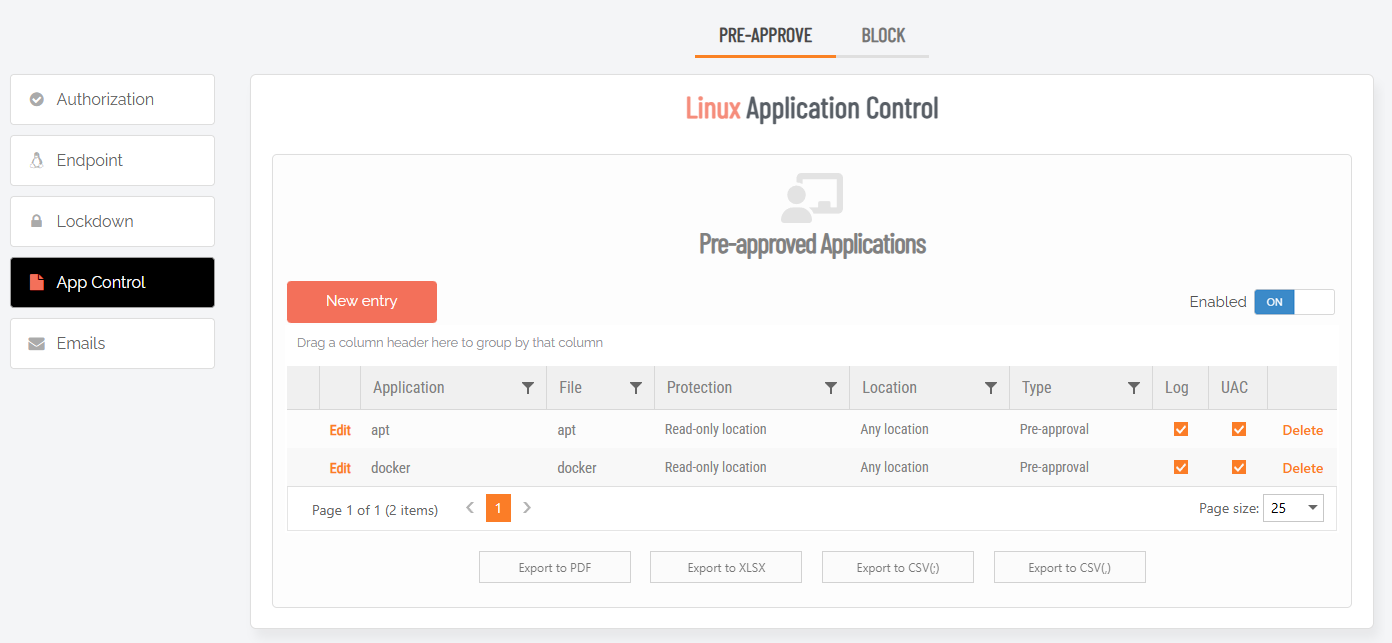
By pre-approving applications and/or requesting a reason for elevation requests, you can ensure all elevated privileges are fully considered prior to granting access. |
|
AC-6 (2) Least Privilege: Non-privileged Access for Non-security Functions Require that users of system accounts (or roles) with access to itemized security functions and/or security-relevant information use non-privileged accounts or roles, when accessing non-security functions. |
Requiring the use of non-privileged accounts when accessing non-security functions limits exposure when operating from within privileged accounts or roles. The inclusion of roles addresses situations where organizations implement access control policies, such as role-based access control, and where a change of role provides the same degree of assurance in the change of access authorizations for the user and the processes acting on behalf of the user as would be provided by a change between a privileged and non-privileged account. |
The setting MFA Account Separation requires the use of a different account for carrying out privileged operations. This option meets the requirements for Cyber Essentials Plus. |
|
AC-6 (5) Least Privilege: Privileged Accounts Restrict privileged accounts on the system to organization-defined personnel or roles. |
Privileged accounts, including super user accounts, are typically described as system administrator for various types of commercial off-the-shelf operating systems. Restricting privileged accounts to specific personnel or roles prevents day-to-day users from accessing privileged information or privileged functions. Organizations may differentiate in the application of restricting privileged accounts between allowed privileges for local accounts and for domain accounts, provided that they retain the ability to control system configurations for key parameters and as otherwise necessary to sufficiently mitigate risk. |
Privileged user logins can be grouped and assigned privileges for creating or updating any combination of the following:
|
|
AC-6 (6) Least Privilege: Privileged Access by Non-organizational Users Prohibit privileged access to the system by non-organizational users. |
An organizational user is an employee or an individual considered by the organization to have the equivalent status of an employee. Organizational users include contractors, guest researchers, or individuals detailed from other organizations. A non-organizational user is a user who is not an organizational user. Policies and procedures for granting equivalent status of employees to individuals include a need-to-know, citizenship, and the relationship to the organization. |
In addition to full integration with an organization's single sign-on (SSO) implementation, Vendor Access is a remote access feature that allows specific, limited access via web portal to external parties. All logins and operations carried out are fully audited. |
|
AC-6 (7) Least Privilege: Review of User Privileges
|
The need for certain assigned user privileges may change over time to reflect changes in organizational mission and business functions, environments of operation, technologies, or threats. A periodic review of assigned user privileges is necessary to determine if the rationale for assigning such privileges remains valid. If the need cannot be re-validated, organizations take appropriate corrective actions. |
By removing admin rights, Admin By Request eliminates the need for review in most cases and facilitates the review of special cases (exclusions, Domain Admins, Break Glass accounts etc.) via a full audit trail and reporting. |
|
AC-6 (8) Least Privilege: Privilege Levels for Code Execution Prevent the listed software from executing at higher privilege levels than the logged-in users executing the software. |
In certain situations, software applications or programs need to execute with elevated privileges to perform required functions. However, depending on the software functionality and configuration, if the privileges required for execution are at a higher level than the privileges assigned to organizational users invoking such applications or programs, those users may indirectly be provided with greater privileges than assigned. |
Since Admin By Request is a privileged access management solution, by definition, it focuses on minimizing the risks associated with granting administrative privileges to users. Any software that tries to execute with elevated privileges will be intercepted, asking for one of the following, depending on settings specified in the Admin Portal:
Code Execution security elements: Application Control Policies: Admin By Request can enforce application control settings that restrict which applications can run on endpoints. By configuring these settings, including the ability to pre-approve "good apps" and block "bad apps", administrators can prevent unauthorized software from executing with elevated privileges. Least Privilege Principle: The solution adheres to the principle of least privilege, which means that users are only granted the permissions necessary to perform their tasks. This helps mitigate the risk of software running with unnecessary elevated privileges. Privilege Elevation: Admin By Request provides a controlled mechanism for elevating privileges on an as-needed basis. Instead of granting permanent administrative rights to users, it allows them to request elevated privileges for specific tasks, which are then subject to approval by administrators. Auditing and Logging: The solution includes auditing and logging capabilities to track software execution and privilege elevation activities. Integration with Security Tools: Admin By Request can integrate with other security tools and solutions, such as antivirus software and endpoint detection and response (EDR) systems. This integration enhances the overall security posture by providing additional layers of protection against malware and unauthorized software execution. |
|
AC-6 (9) Least Privilege: Log Use of Privileged Functions Log the execution of privileged functions. |
The misuse of privileged functions, either intentionally or unintentionally by authorized users or by unauthorized external entities that have compromised system accounts, is a serious and ongoing concern and can have significant adverse impacts on organizations. Logging and analyzing the use of privileged functions is one way to detect such misuse and, in doing so, help mitigate the risk from insider threats and the advanced persistent threat. |
Admin By Request's auditlog provides full auditability with a tamper-proof record of privileged activities carried out by users. |
|
AC-6 (10) Least Privilege: Prohibit Non-privileged Users from Executing Privileged Functions Prevent non-privileged users from executing privileged functions. |
Privileged functions include disabling, circumventing, or altering implemented security or privacy controls, establishing system accounts, performing system integrity checks, and administering cryptographic key management activities. Privileged functions that require protection from non-privileged users include circumventing intrusion detection and prevention mechanisms or malicious code protection mechanisms. Non-privileged users are individuals who do not possess appropriate authorizations. Preventing non-privileged users from executing privileged functions is enforced by AC-3. |
Admin rights are revoked from all users and you can configure Admin By Request to require approval for each elevation. |
|
AC-17 Remote Access
|
Remote access is access to organizational systems (or processes acting on behalf of users) that communicate through external networks such as the Internet. Types of remote access include dial-up, broadband, and wireless. Organizations use encrypted virtual private networks (VPNs) to enhance confidentiality and integrity for remote connections. The use of encrypted VPNs provides sufficient assurance to the organization that it can effectively treat such connections as internal networks if the cryptographic mechanisms used are implemented in accordance with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines. Still, VPN connections traverse external networks, and the encrypted VPN does not enhance the availability of remote connections. VPNs with encrypted tunnels can also affect the ability to adequately monitor network communications traffic for malicious code. Remote access controls apply to systems other than public web servers or systems designed for public access. Authorization of each remote access type addresses authorization prior to allowing remote access without specifying the specific formats for such authorization. While organizations may use information exchange and system connection security agreements to manage remote access connections to other systems, such agreements are addressed as part of CA-3. Enforcing access restrictions for remote access is addressed via AC-3. |
Admin By Request includes a feature called Secure Remote Access (also known as Remote Access): Unattended Access is a feature of Secure Remote Access that allows you to connect remotely to your servers and network endpoints directly from your browser, using a lot of the well-known Admin By Request features like: inventory, auditlog, settings and sub-settings, approval flows, integrations etc.The implementation of Unattended Access can use either a "Cloud" or an "On-premise" gateway, eliminating the need for VPN and jump servers, while still maintaining a secure and segregated setup. Using Remote Access does not restrict any of Admin By Request's functionality. In particular, the following apply:
Remote Access security elements: The elements described below illustrate how Admin By Request's Secure Remote Access product can assist with monitoring and control of remote access.
|
|
AC-17 (1) Remote Access: Monitoring and Control Employ automated mechanisms to monitor and control remote access methods. |
Monitoring and control of remote access methods allows organizations to detect attacks and help ensure compliance with remote access policies by auditing the connection activities of remote users on a variety of system components, including servers, notebook computers, workstations, smart phones, and tablets. Audit logging for remote access is enforced by AU-2. Audit events are defined in AU-2a. |
Session recording and auditing: Remote Access includes the ability to record sessions for auditing and compliance purposes. This allows administrators to review activities performed during remote sessions and identify any unauthorized or suspicious behavior. Session timeout and idle session management: To mitigate the risk of unauthorized access in case of session abandonment or inactivity, Remote Access includes session timeout and idle session management features. These automatically terminate inactive sessions after a predefined period of time. |
|
AC-17 (2) Remote Access: Protection of Confidentiality and Integrity Using Encryption Implement cryptographic mechanisms to protect the confidentiality and integrity of remote access sessions. |
Virtual private networks can be used to protect the confidentiality and integrity of remote access sessions. Transport Layer Security (TLS) is an example of a cryptographic protocol that provides end-to-end communications security over networks and is used for Internet communications and online transactions. |
Encryption: Data transmitted over the network is encrypted and remains confidential, ensuring it cannot be intercepted or tampered with by unauthorized parties. |
|
AC-17 (3) Remote Access: Managed Access Control Points Route remote accesses through authorized and managed network access control points. |
Organizations consider the Trusted Internet Connections (TIC) initiative DHS TIC requirements for external network connections, since limiting the number of access control points for remote access reduces attack surfaces. |
Role-based access control (RBAC): Remote Access participates in RBAC via Admin By Request's global settings and sub-settings, ensuring that only authorized users have access to specific features and functionalities based on their roles within the organization. This helps in limiting access to sensitive systems and data. Access control sub-settings: Administrators can define granular access control sub-settings to restrict the actions that remote users can perform on the target systems. This helps in enforcing security best practices and minimizing the risk of unauthorized changes or data breaches. |
|
AC-17 (4) Remote Access: Privileged Commands and Access
|
Remote access to systems represents a significant potential vulnerability that can be exploited by adversaries. As such, restricting the execution of privileged commands and access to security-relevant information via remote access reduces the exposure of the organization and the susceptibility to threats by adversaries to the remote access capability. |
Multi-factor authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before gaining access to the remote system. |
|
AC-17 (6) Remote Access: Authenticate Remote Commands Implement appropriate organization-defined mechanisms to authenticate relevant organization-defined remote commands. |
Authenticating remote commands protects against unauthorized commands and the replay of authorized commands. The ability to authenticate remote commands is important for remote systems for which loss, malfunction, misdirection, or exploitation would have immediate or serious consequences, such as injury, death, property damage, loss of high value assets, failure of mission or business functions, or compromise of classified or controlled unclassified information. Authentication mechanisms for remote commands ensure that systems accept and execute commands in the order intended, execute only authorized commands, and reject unauthorized commands. Cryptographic mechanisms can be used, for example, to authenticate remote commands. |
Integration with existing security infrastructure: Remote Access is an integral part of Admin By Request, which integrates with existing security infrastructure such as firewalls, anti-virus software, and SIEM (Security Information and Event Management) systems to provide comprehensive protection against security threats. Regular software updates and patches: Remote Access is part of Admin By Request's Software Development Life Cycle (SDLC), meaning regular software updates and patches are applied. These are crucial for addressing security vulnerabilities and ensuring that the remote access solution remains resilient against emerging threats.
Refer to Secure Remote Access for more information. |
DORA
 Relevant articles, requirements and how ABR helps
Relevant articles, requirements and how ABR helps
![]() DORA - How Admin By Request Helps
DORA - How Admin By Request Helps
|
Article |
Requirement |
How ABR helps to ensure compliance |
|---|---|---|
|
Article 9 (3) (a) |
In order to achieve the objectives referred to in paragraph 2, financial entities shall use ICT solutions and processes that are appropriate in accordance with Article 4. Those ICT solutions and processes shall:
|
Admin By Request enables Just-In-Time Privileged Access by granting temporary administrative privileges, aligning with DORA’s Article 9 (3) (a) and Article 9 (3) (b) by limiting unnecessary access and reducing the risk of unauthorized actions, aligning with DORA's principle of least privilege. |
|
Article 9 (3) (b) |
In order to achieve the objectives referred to in paragraph 2, financial entities shall use ICT solutions and processes that are appropriate in accordance with Article 4. Those ICT solutions and processes shall:
|
|
|
Article 17 |
Full article |
Through comprehensive logging and tracking functionality, Admin By Request ensures traceability and accountability via a detailed audit trail of all privileged access activities, aiding in compliance with DORA's reporting requirements (DORA Article 17). |
|
Article 10 |
Full article |
Continuous Monitoring and Control:
|
|
Article 9 (4) (c) |
As part of the ICT risk management framework referred to in Article 6 (1), financial entities shall:
|
Automated Work flows and Compliance Reporting:
|
NIS2
 Relevant paragraphs, objectives and how ABR helps
Relevant paragraphs, objectives and how ABR helps
![]() NIS2 - How Admin By Request Helps
NIS2 - How Admin By Request Helps
|
Paragraph |
Objective |
How ABR helps to ensure compliance |
|---|---|---|
|
Paragraph 49
|
Cyber hygiene policies provide the foundations for protecting network and information system infrastructures, hardware, software and online application security, and business or end-user data upon which entities rely. Cyber hygiene policies comprising a common baseline set of practices, including software and hardware updates, password changes, the management of new installs, the limitation of administrator-level access accounts, and the backing-up of data, enable a proactive framework of preparedness and overall safety and security in the event of incidents or cyber threats. ENISA should monitor and analyze Member States’ cyber hygiene policies. |
Admin By Request can help your organization to securely manage software installs. It enables you to ensure that only authorized personnel are allowed to initiate and oversee new installs. This controlled access, complemented by monitoring features, provides an added safeguard, shielding the company's infrastructure from potential threats associated with the introduction of new software. |
|
Paragraph 54 |
In recent years, the Union has faced an exponential increase in ransomware attacks, in which malware encrypts data and systems and demands a ransom payment for release. The increasing frequency and severity of ransomware attacks can be driven by several factors, such as different attack patterns, criminal business models around ‘ransomware as a service’ and cryptocurrencies, ransom demands, and the rise of supply chain attacks. Member States should develop a policy addressing the rise of ransomware attacks as part of their national cybersecurity strategy. |
Admin By Request acts as guardian against ransomware by enforcing the principle of least privilege, ensuring users have only the necessary access for only the amount of time they need it. It also enables you to monitor and log privileged activities. |
|
Paragraph 85 |
Addressing risks stemming from an entity’s supply chain and its relationship with its suppliers, such as providers of data storage and processing services or managed security service providers and software editors, is particularly important given the prevalence of incidents where entities have been the victim of cyber attacks and where malicious perpetrators were able to compromise the security of an entity’s network and information systems by exploiting vulnerabilities affecting third-party products and services. Essential and important entities should therefore assess and take into account the overall quality and resilience of products and services, the cybersecurity risk-management measures embedded in them, and the cybersecurity practices of their suppliers and service providers, including their secure development procedures. Essential and important entities should in particular be encouraged to incorporate cybersecurity risk-management measures into contractual arrangements with their direct suppliers and service providers. Those entities could consider risks stemming from other levels of suppliers and service providers. |
Mitigating the risk of access to your resources by, e.g., an external consultant, you can utilize the Remote Access feature in Admin By Request Server Editions to mitigate the risk of remote access to your servers. |
|
Paragraph 89 |
Essential and important entities should adopt a wide range of basic cyber hygiene practices, such as zero-trust principles, software updates, device configuration, network segmentation, identity and access management or user awareness. These entities should also schedule regular training for their staff and raise awareness concerning cyber threats, phishing or social engineering techniques. Furthermore, the entities should evaluate their own cybersecurity capabilities and, where appropriate, pursue the integration of cybersecurity enhancing technologies, such as artificial intelligence or machine-learning systems to enhance their capabilities and the security of network and information systems. |
Entities can address this objective with Admin By Request by managing all privileged access within their organization. Further, machine learning capabilities for elevation approval can be enabled. |
|
Paragraph 102 |
Where essential or important entities become aware of a significant incident, they should be required to submit an early warning without undue delay and in any event within 24 hours. That early warning should be followed by an incident notification. The entities concerned should submit an incident notification without undue delay and in any event within 72 hours of becoming aware of the significant incident, with the aim, in particular, of updating information submitted through the early warning and indicating an initial assessment of the significant incident, including its severity and impact, as well as indicators of compromise, where available. A final report should be submitted not later than one month after the incident notification. The early warning should include only the information necessary to make the CSIRT, or where applicable the competent authority, aware of the significant incident and allow the entity concerned to seek assistance, if required. Such early warning, where applicable, should indicate whether the significant incident is suspected of being caused by unlawful or malicious acts, and whether it is likely to have a cross-border impact. Member States should ensure that the obligation to submit that early warning, or the subsequent incident notification, does not divert the notifying entity’s resources from activities related to incident handling that should be prioritized, in order to prevent incident reporting obligations from either diverting resources from significant incident response handling or otherwise compromising the entity’s efforts in that respect. EN Official Journal of the European Union 27.12.2022 L 333/99: "In the event of an ongoing incident at the time of the submission of the final report, Member States should ensure that entities concerned provide a progress report at that time, and a final report within one month of their handling of the significant incident." |
The Admin By Request auditlog makes it easy to audit and report on all activity undertaken by users while they have elevated privileges. |